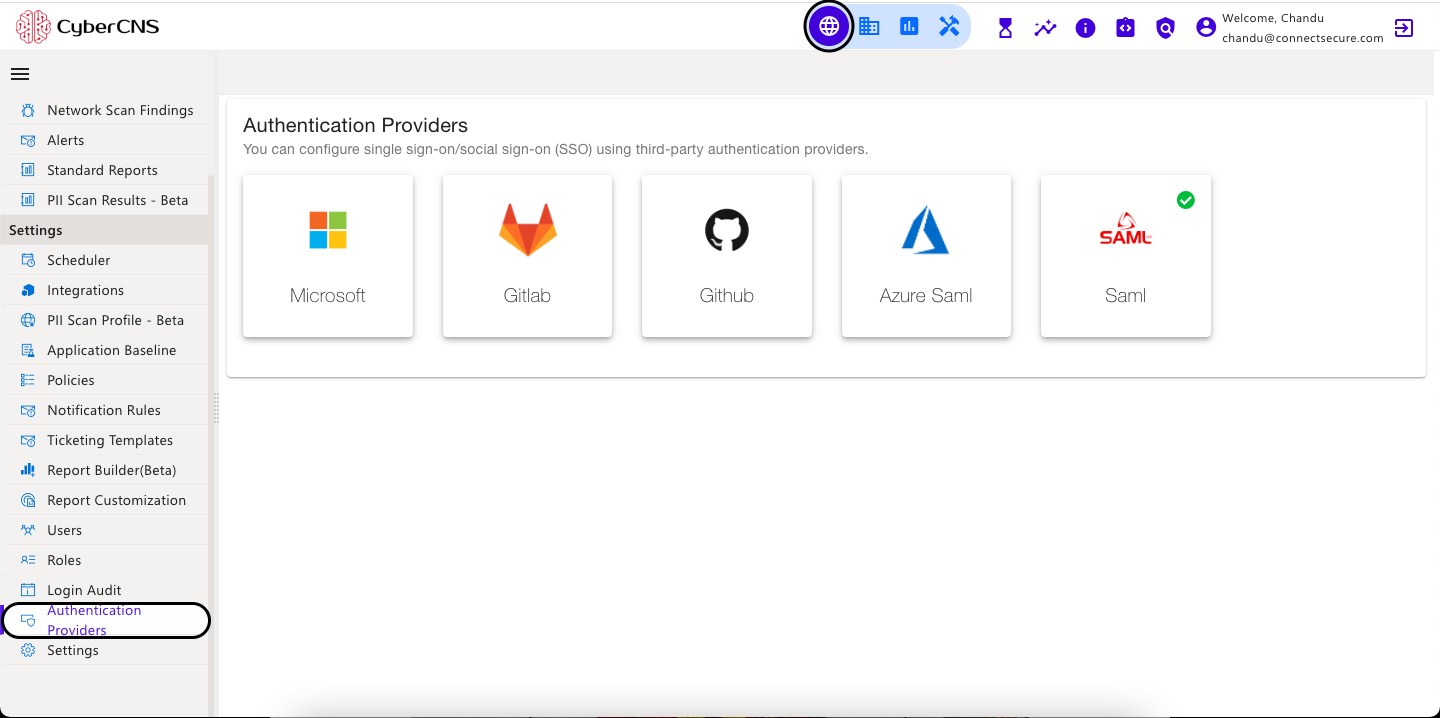
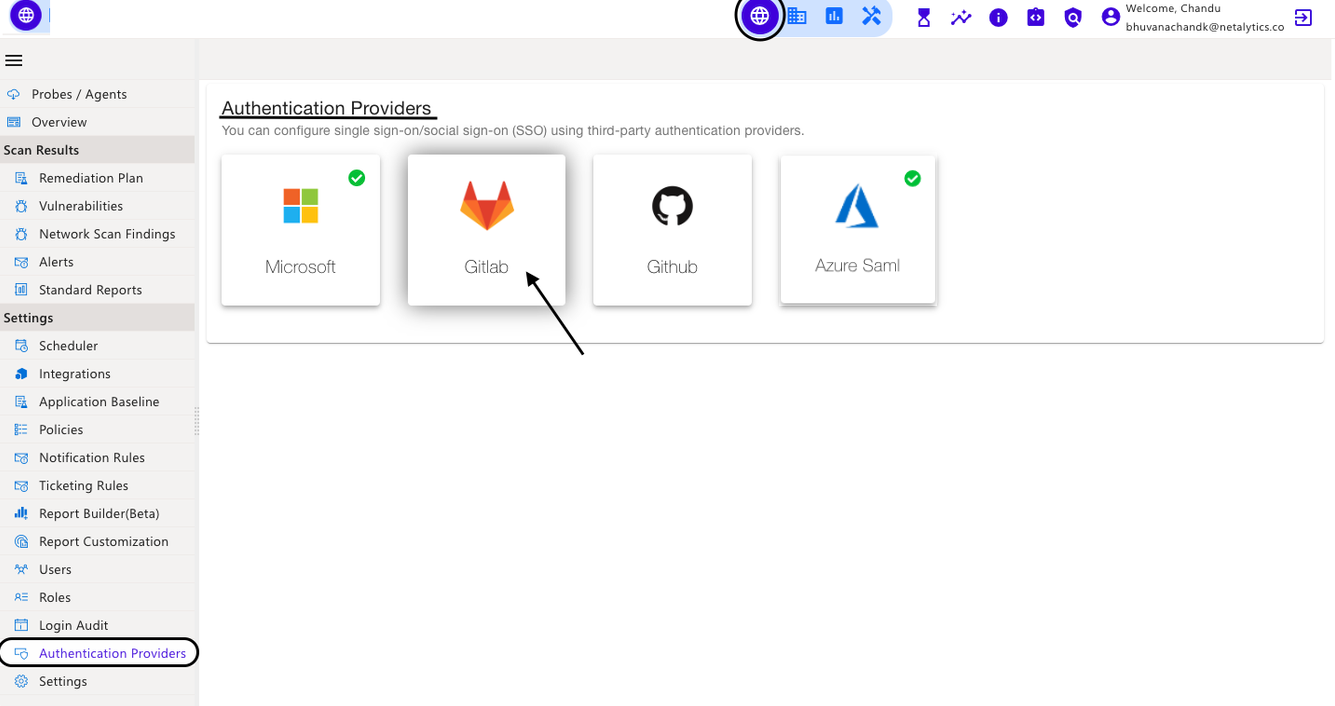
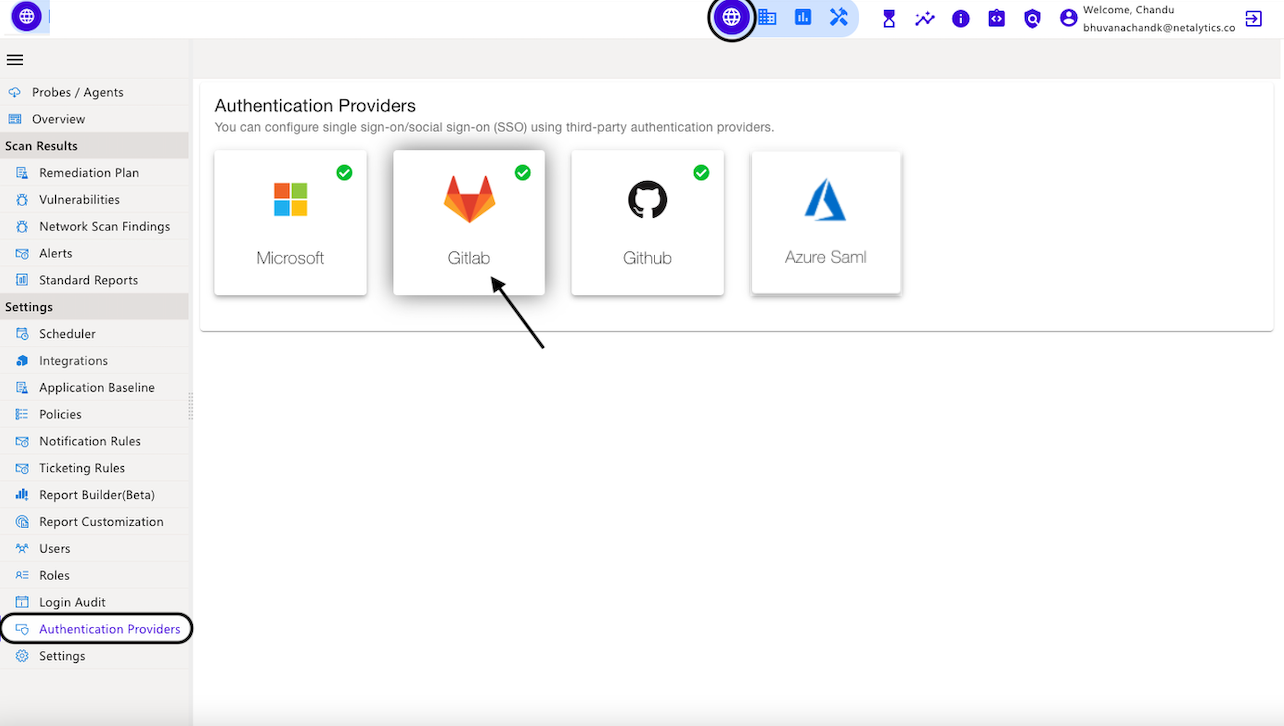
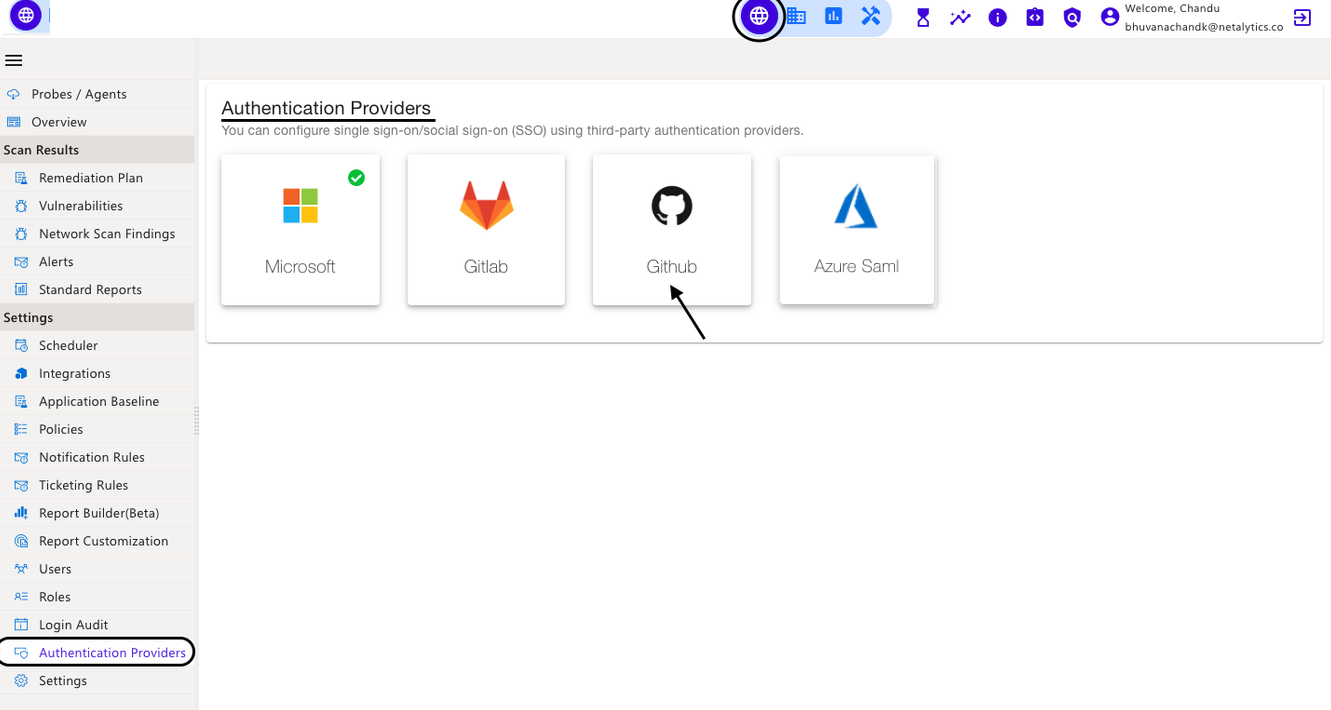
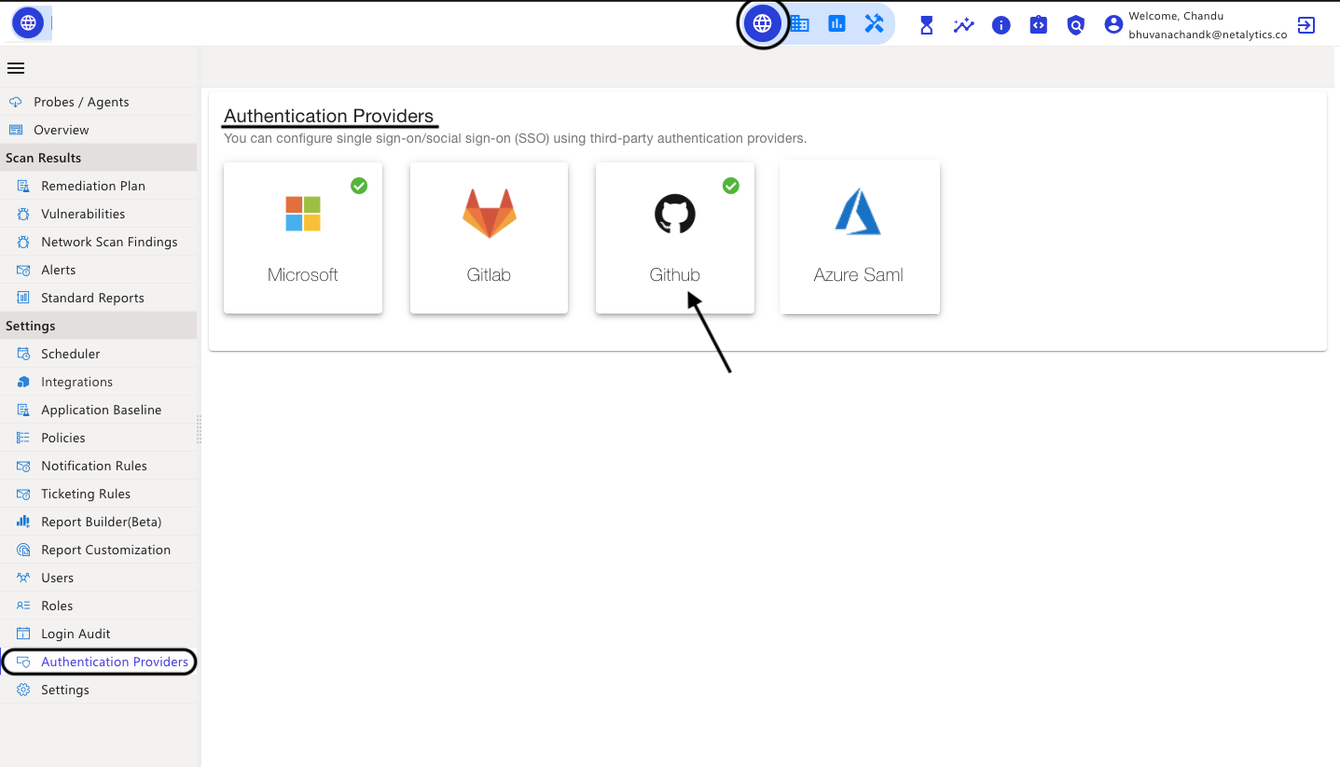
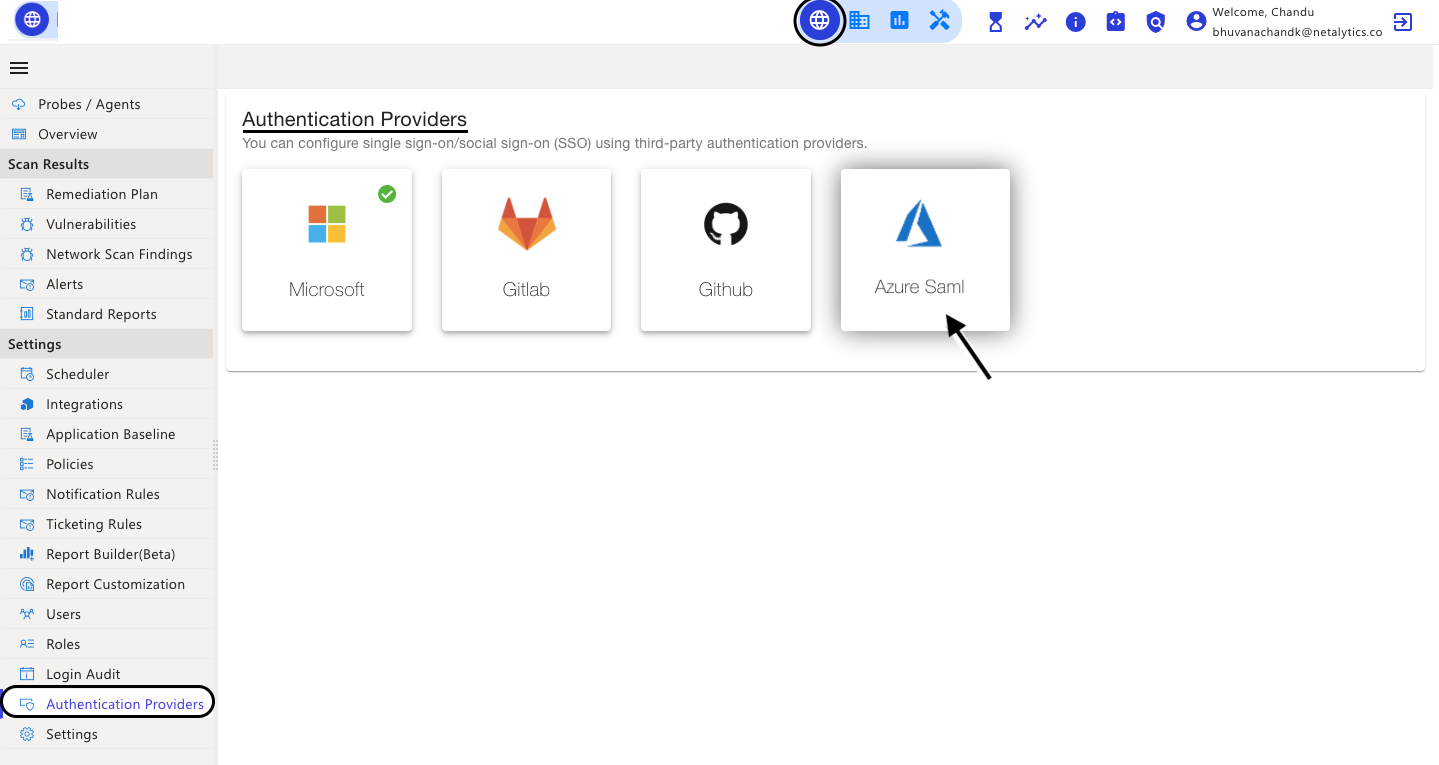
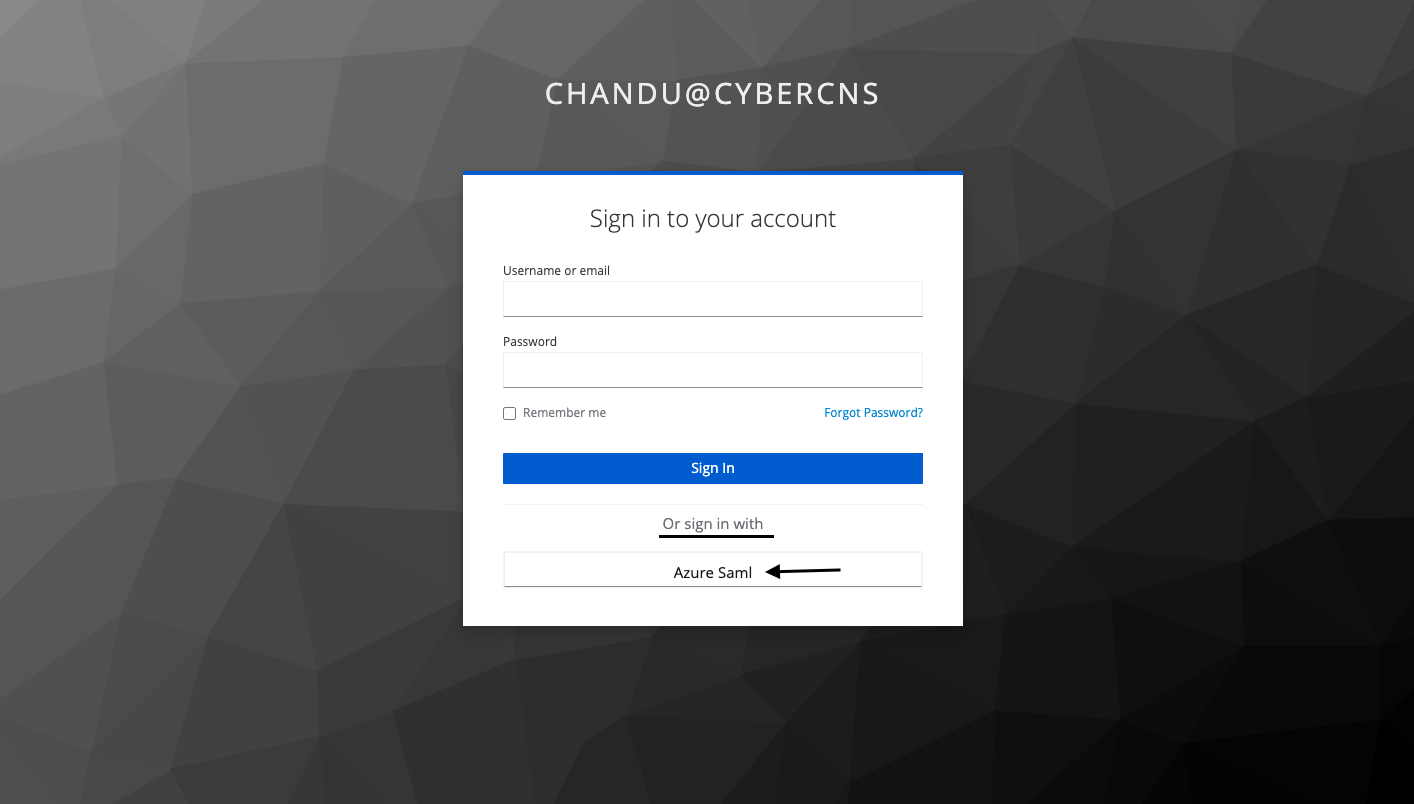
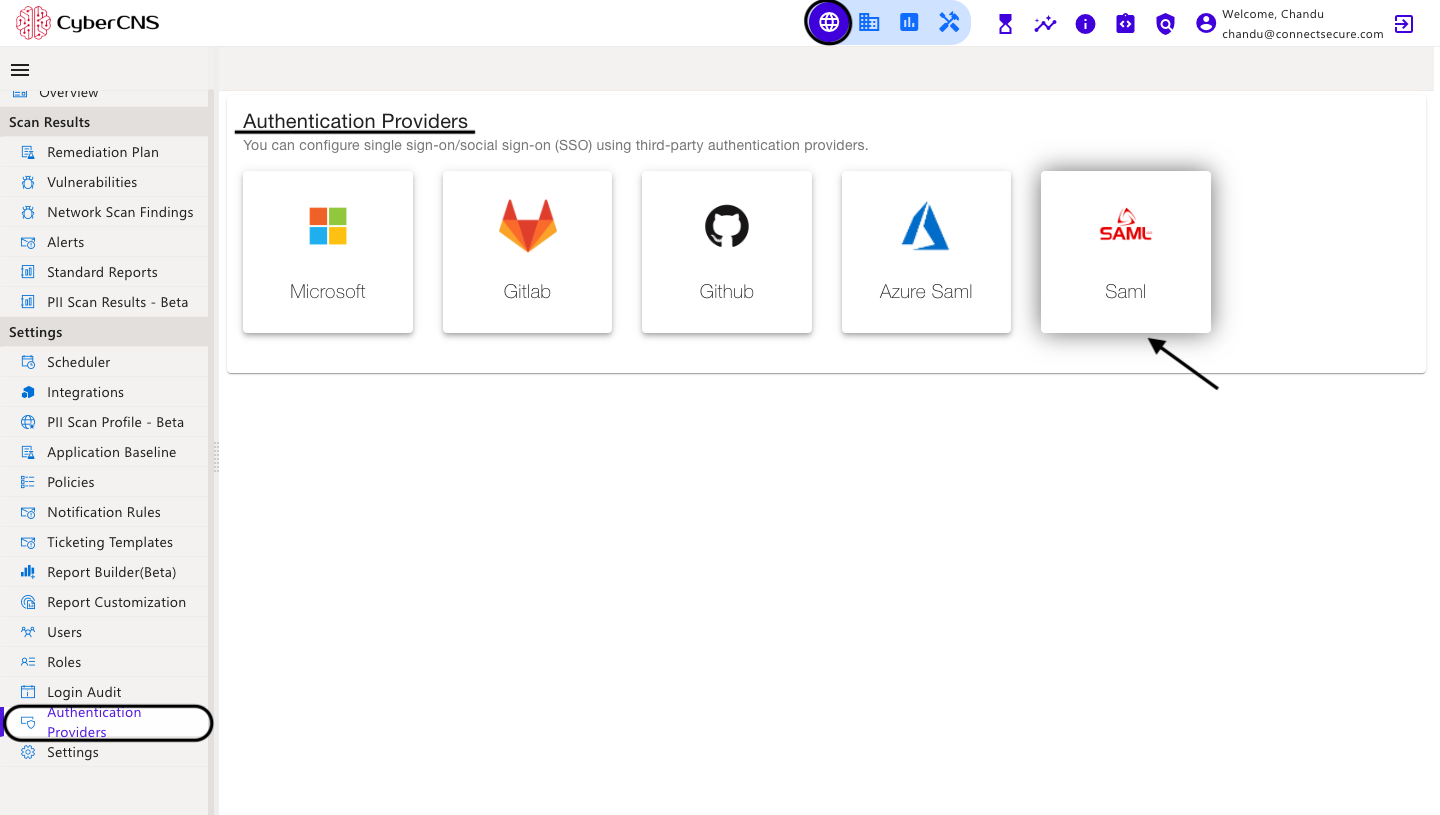
Using third-party authentication providers, you can set up single sign-on/social sign-on (SSO). These authentication providers are Microsoft, Gitlab, Github, Azure Saml, and SAML.
Microsoft
To allow authentication to Web APIs hosted in the CyberCNS app using a client library such as the Active Directory Authentication Library.
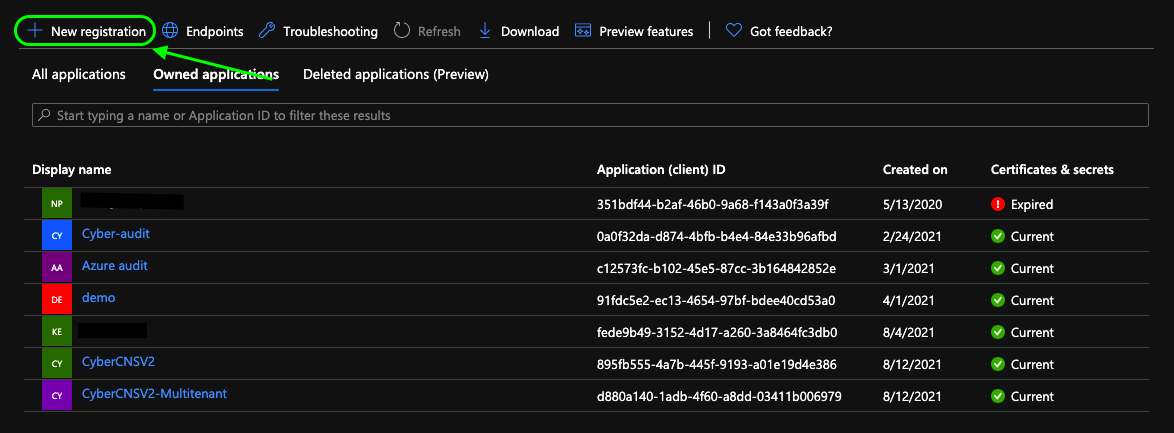
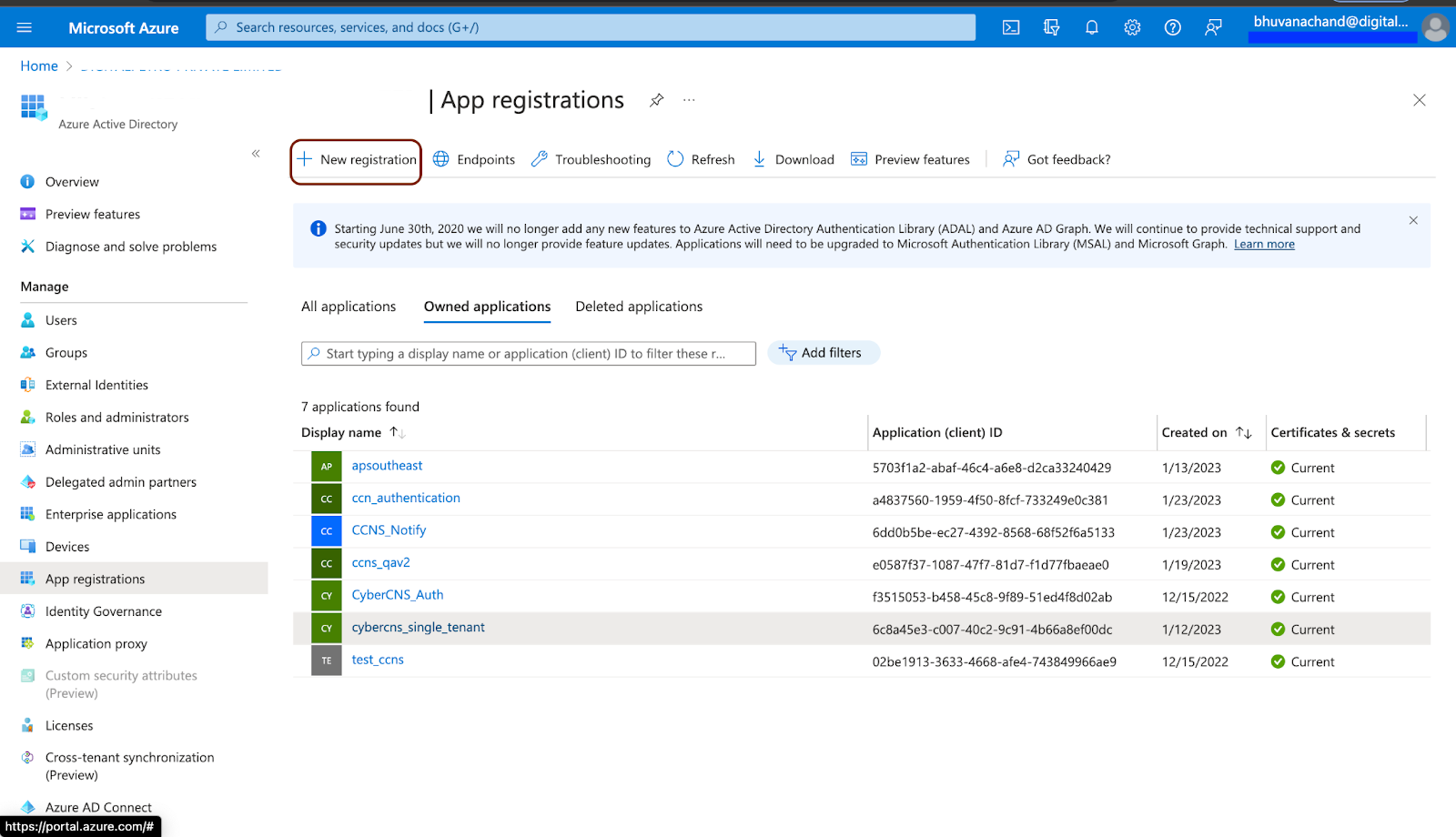
In the Azure portal, navigate to Active Directory > App registrations > New registration.
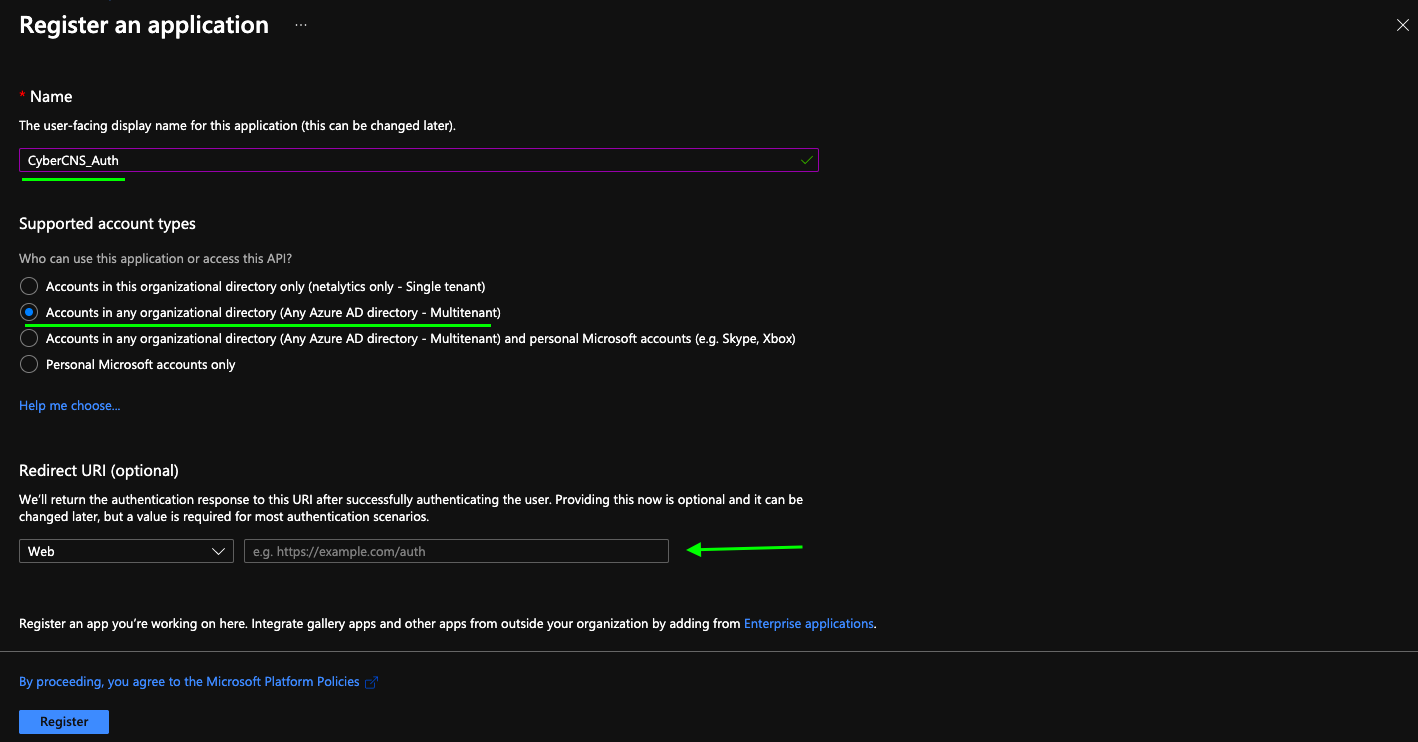
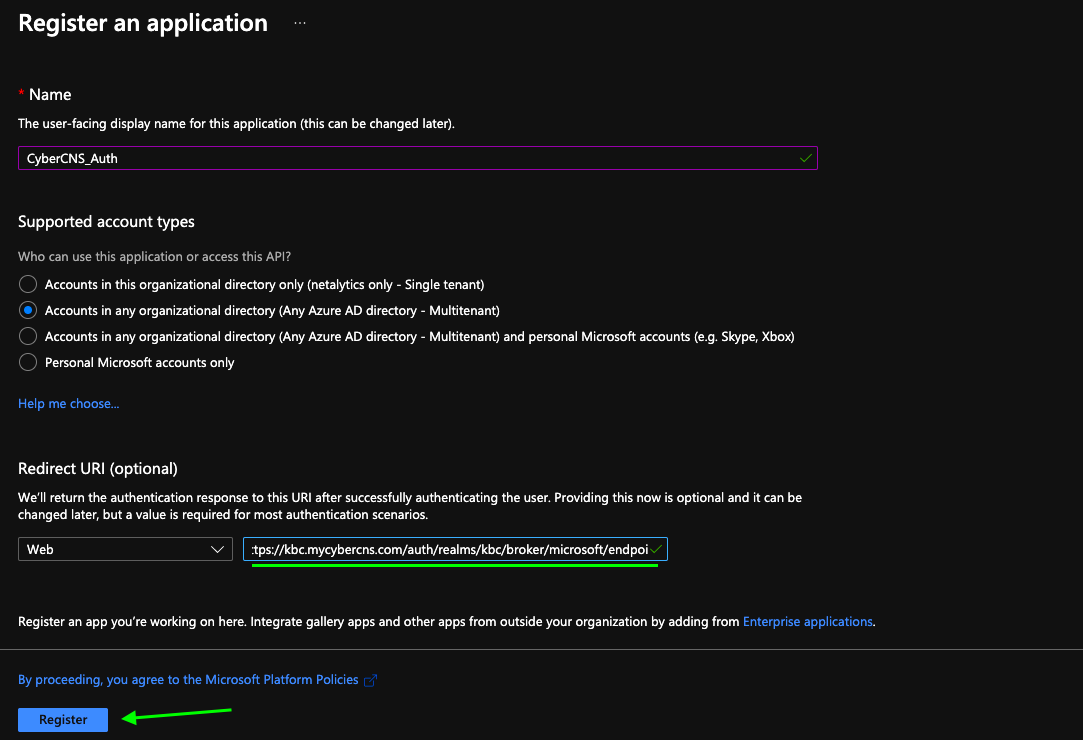
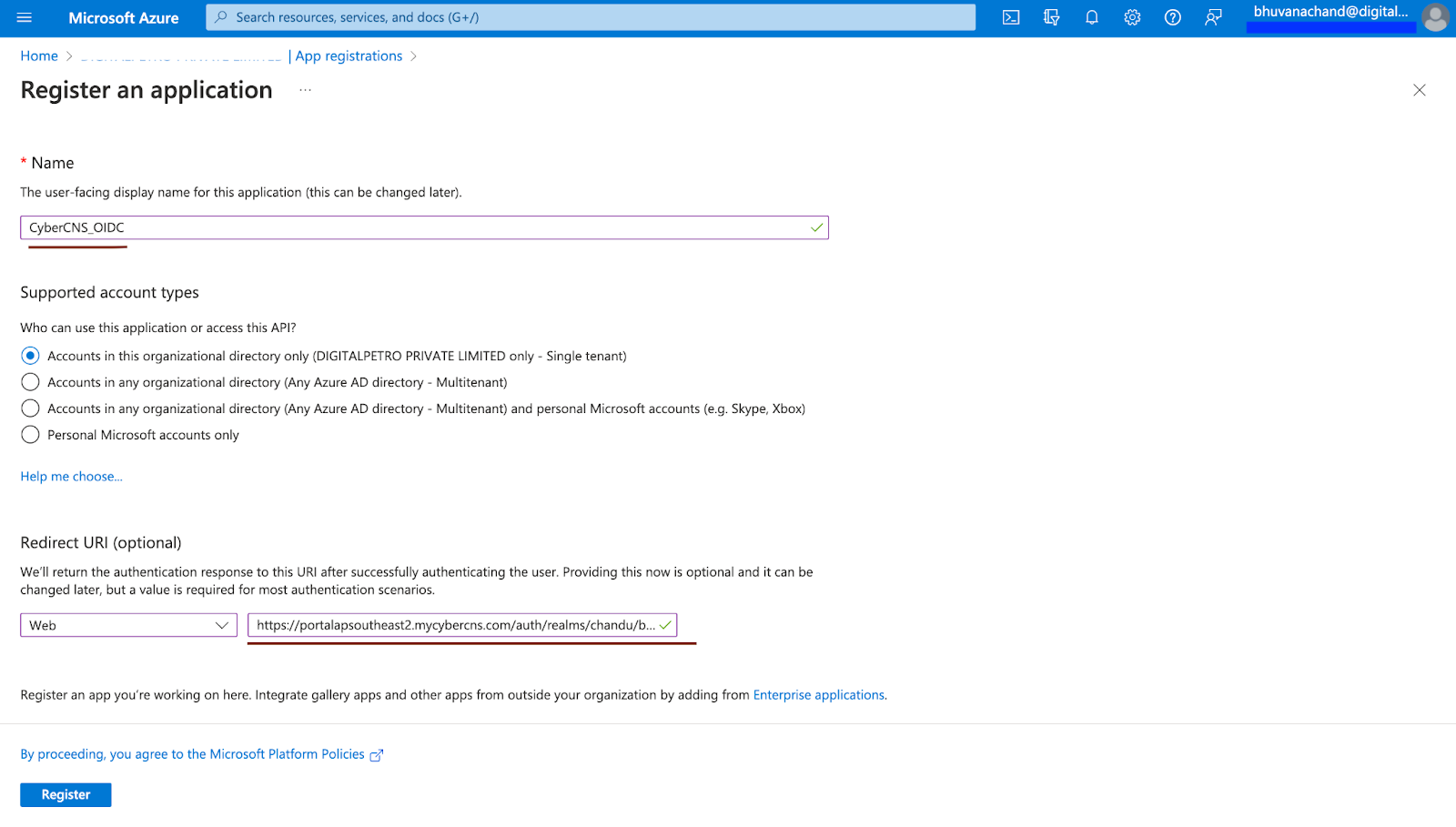
In the Register an application page, enter a Name of your choice for app registration.
Please select Account types as Multitenant (shown below). As supported by Microsoft, we need to select Multitenant.
Also, mention the redirect URL and click on Register to successfully register an application. (Redirect URL to be copied from CyberCNS)
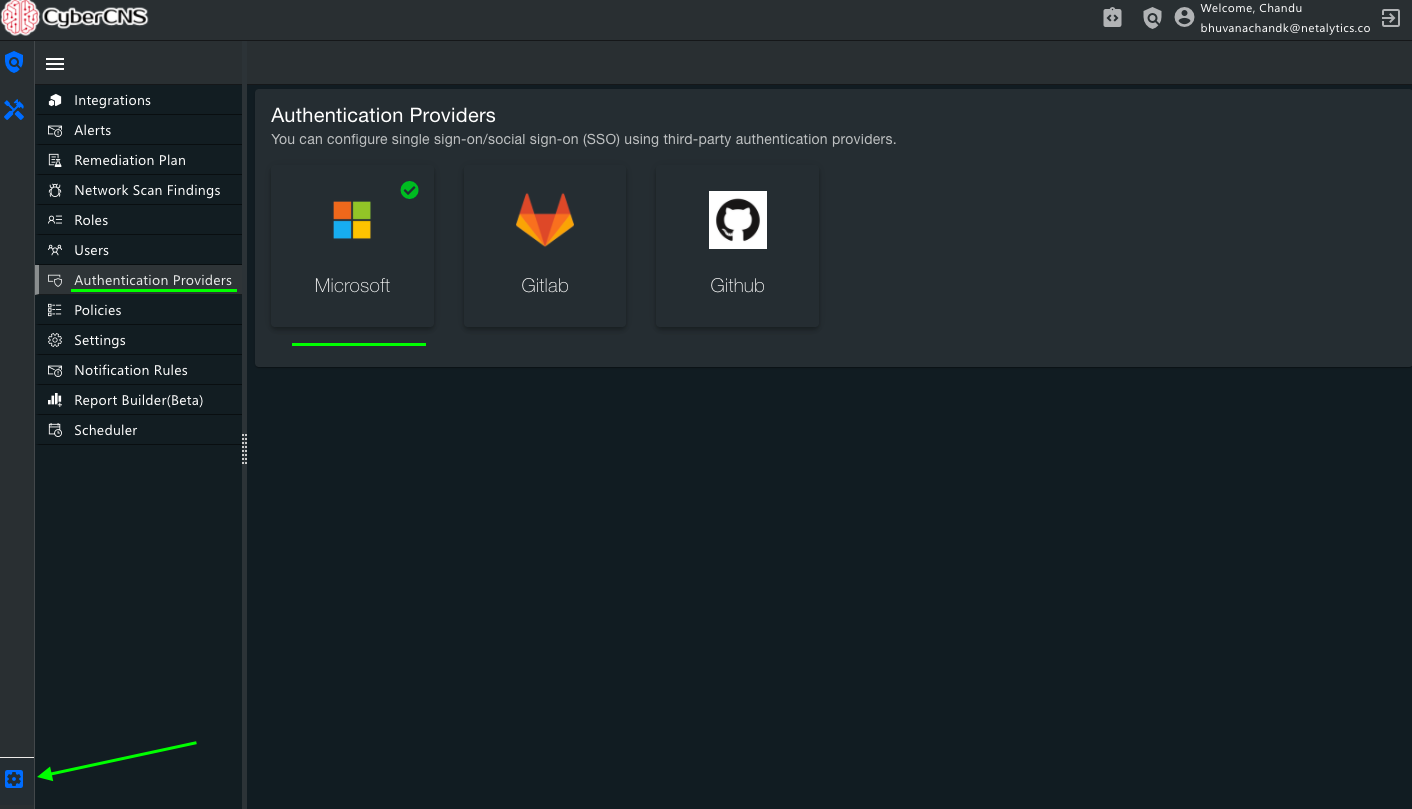
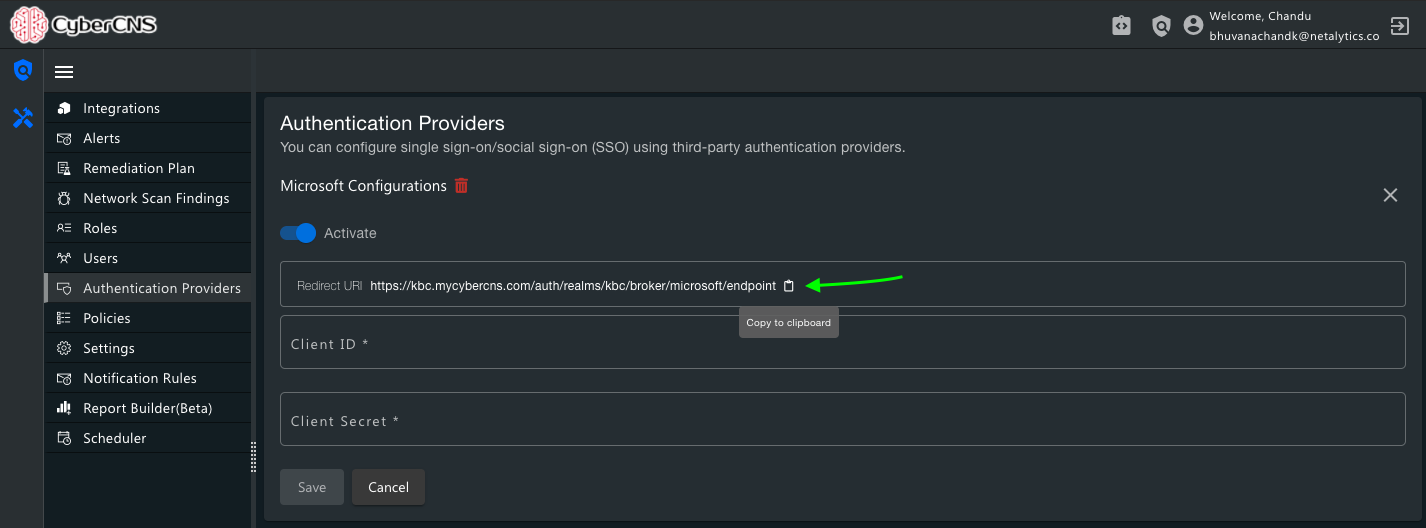
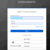
3. In the CyberCNS portal navigate to Global Settings>Authentication Providers and select Microsoft.
Please copy Redirect URL from the CyberCNS portal and paste it into an Application created into Azure under Active Directory.
Register this application once you change the redirect URL.
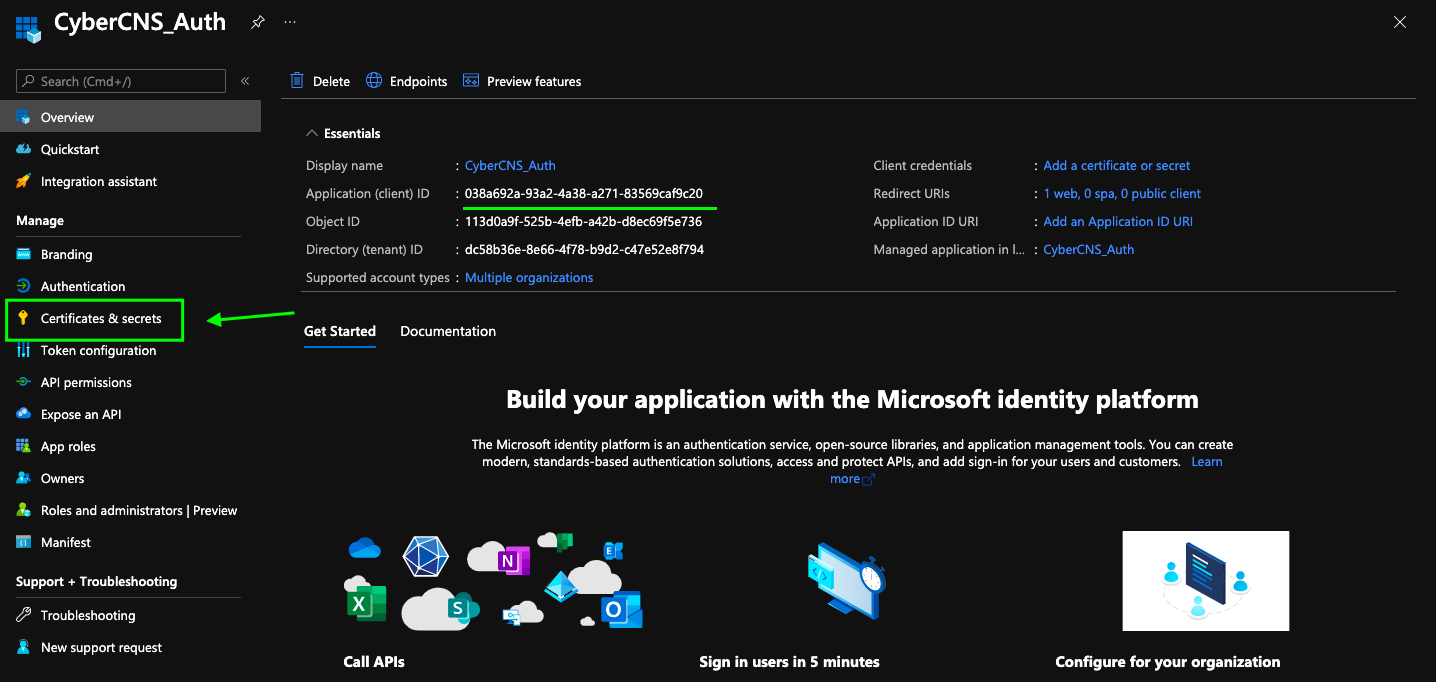
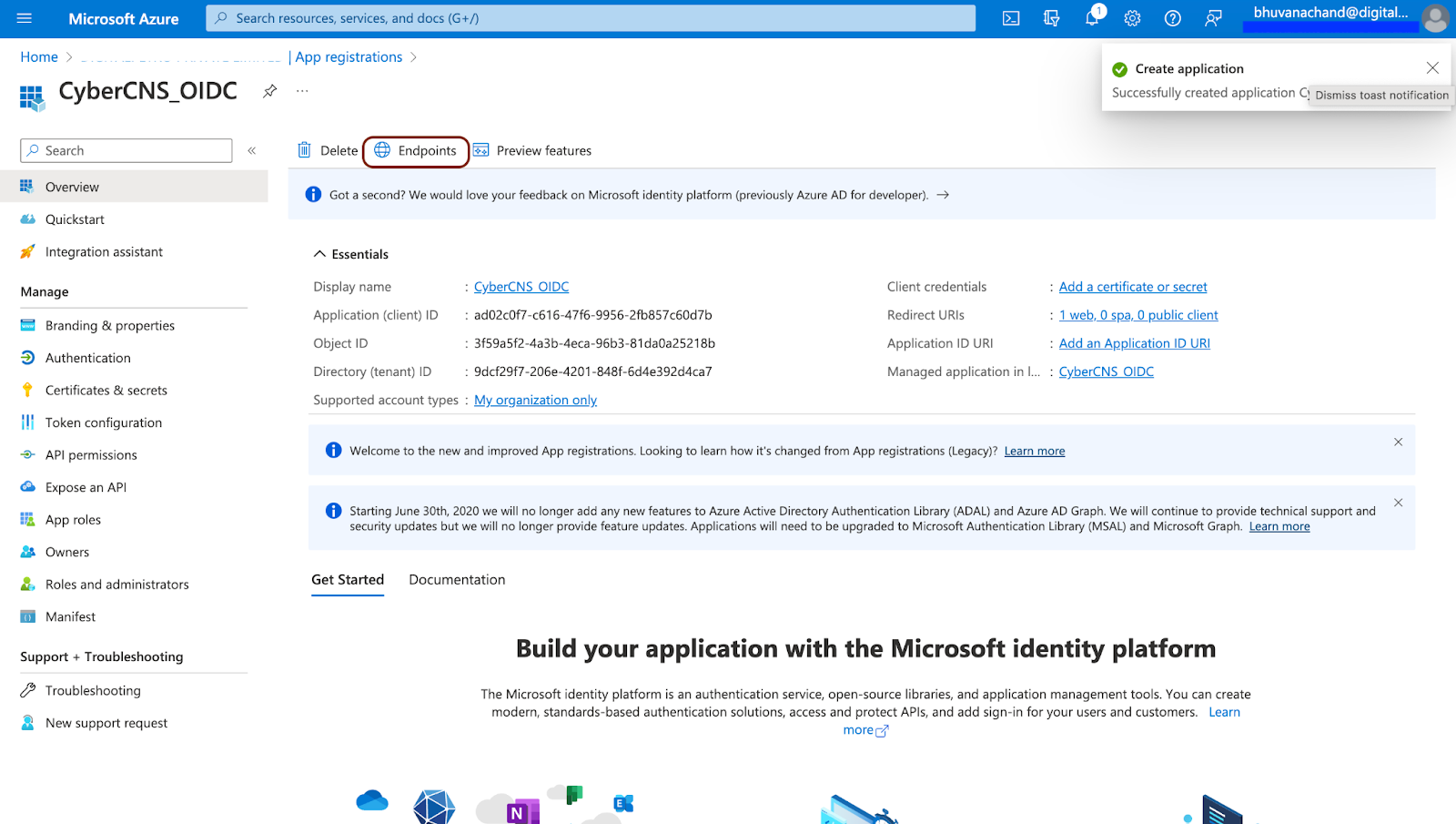
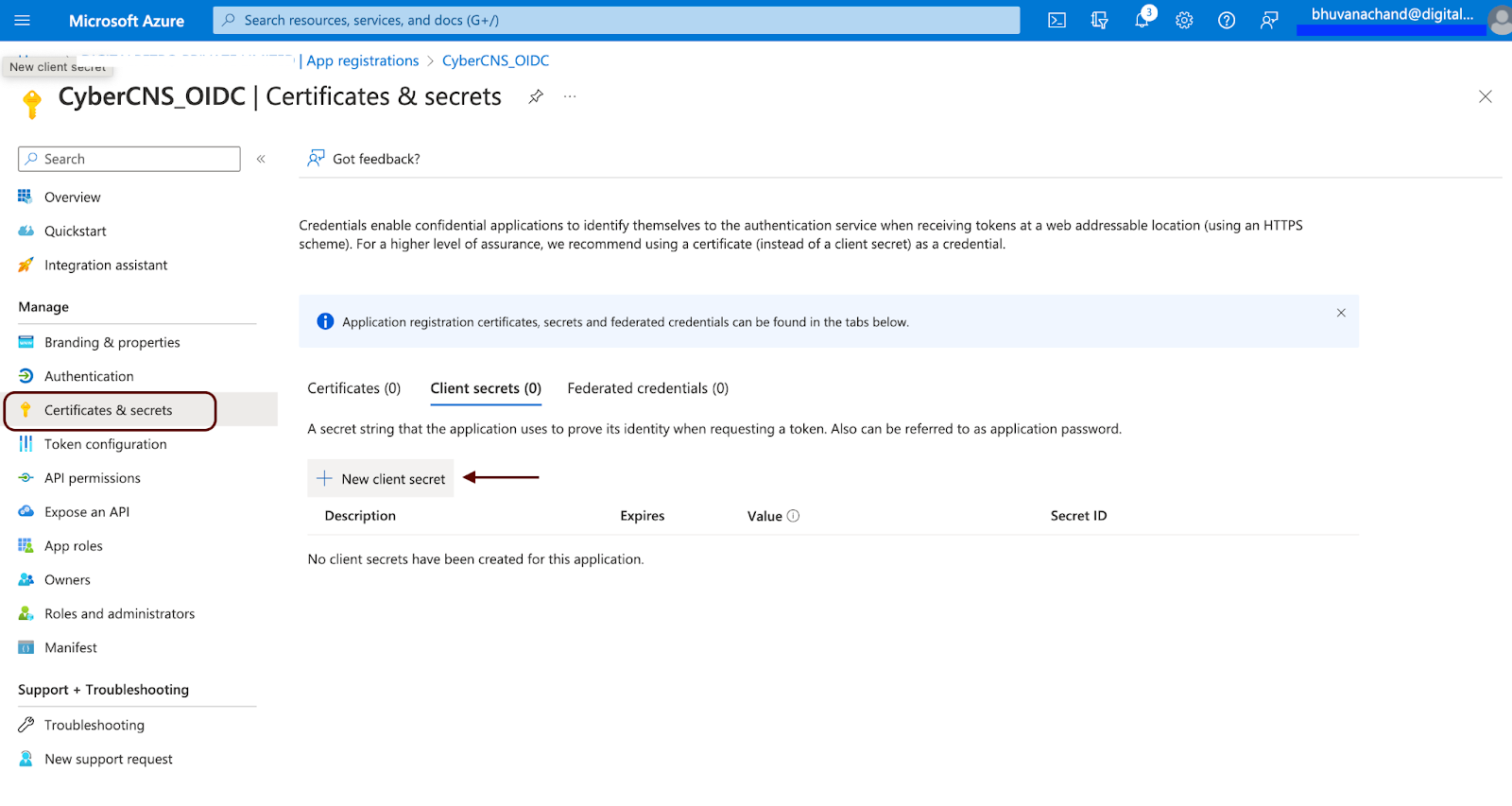
Navigate to the Certificates & Secrets section for the registered application.
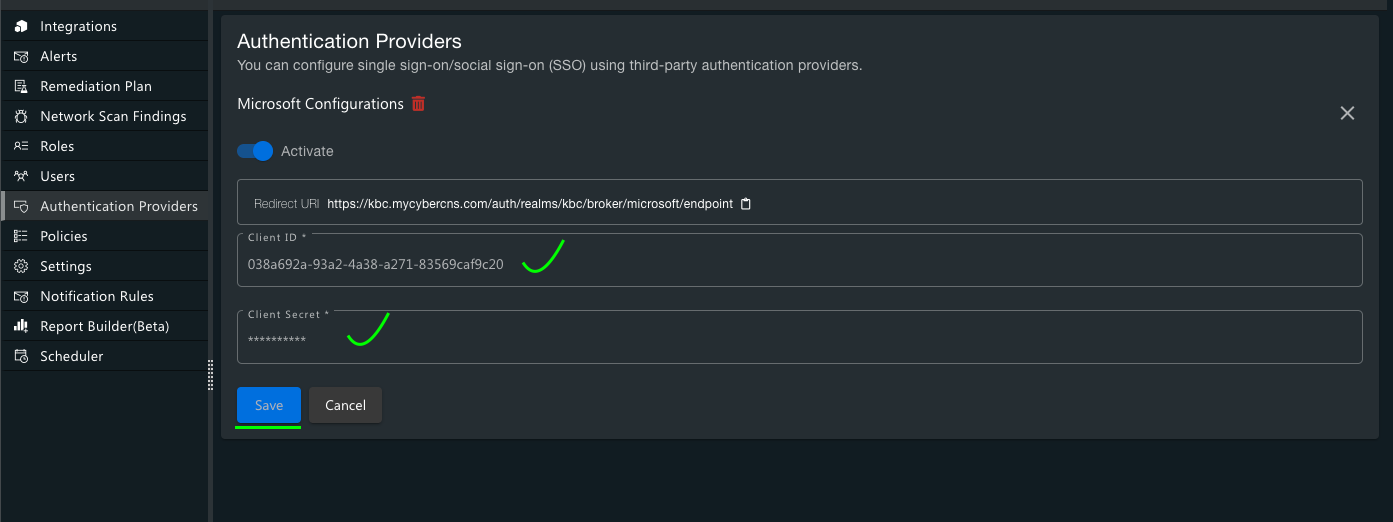
Copy the Application (Client) ID from here to be provided into the CyberCNS portal.
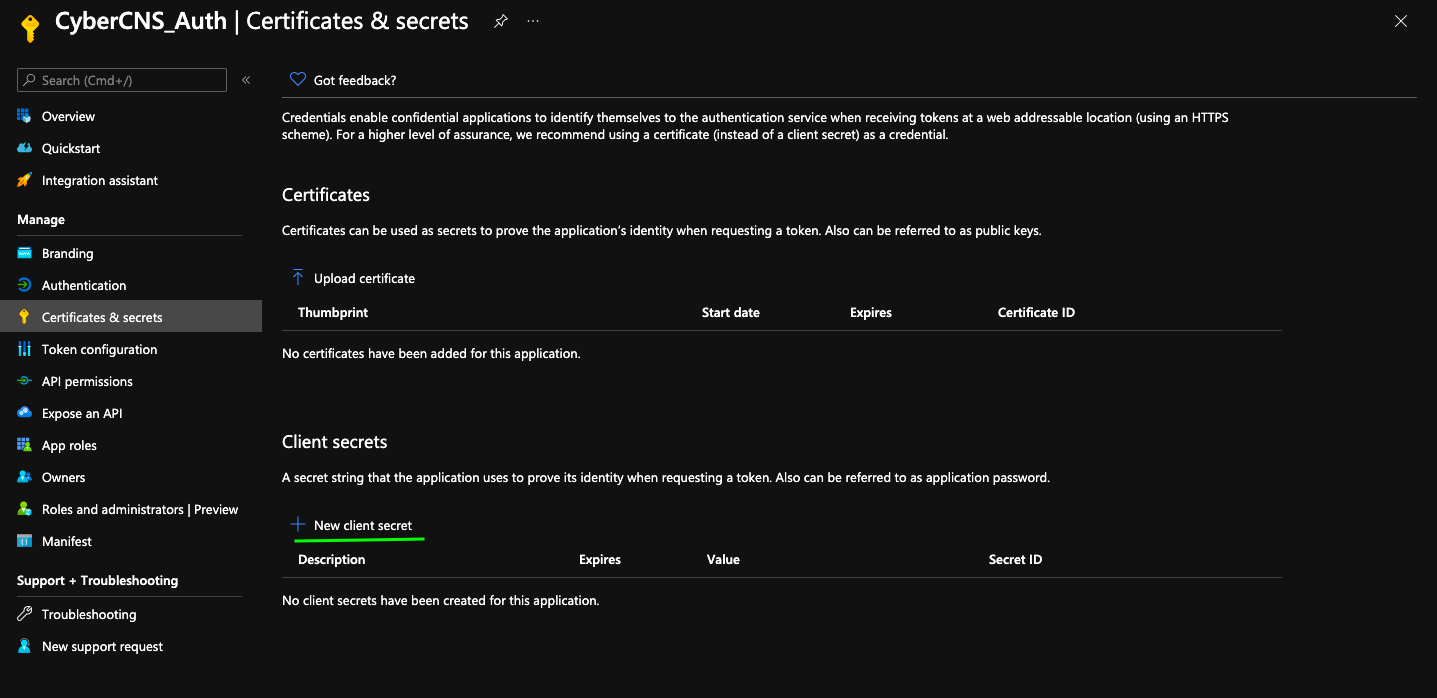
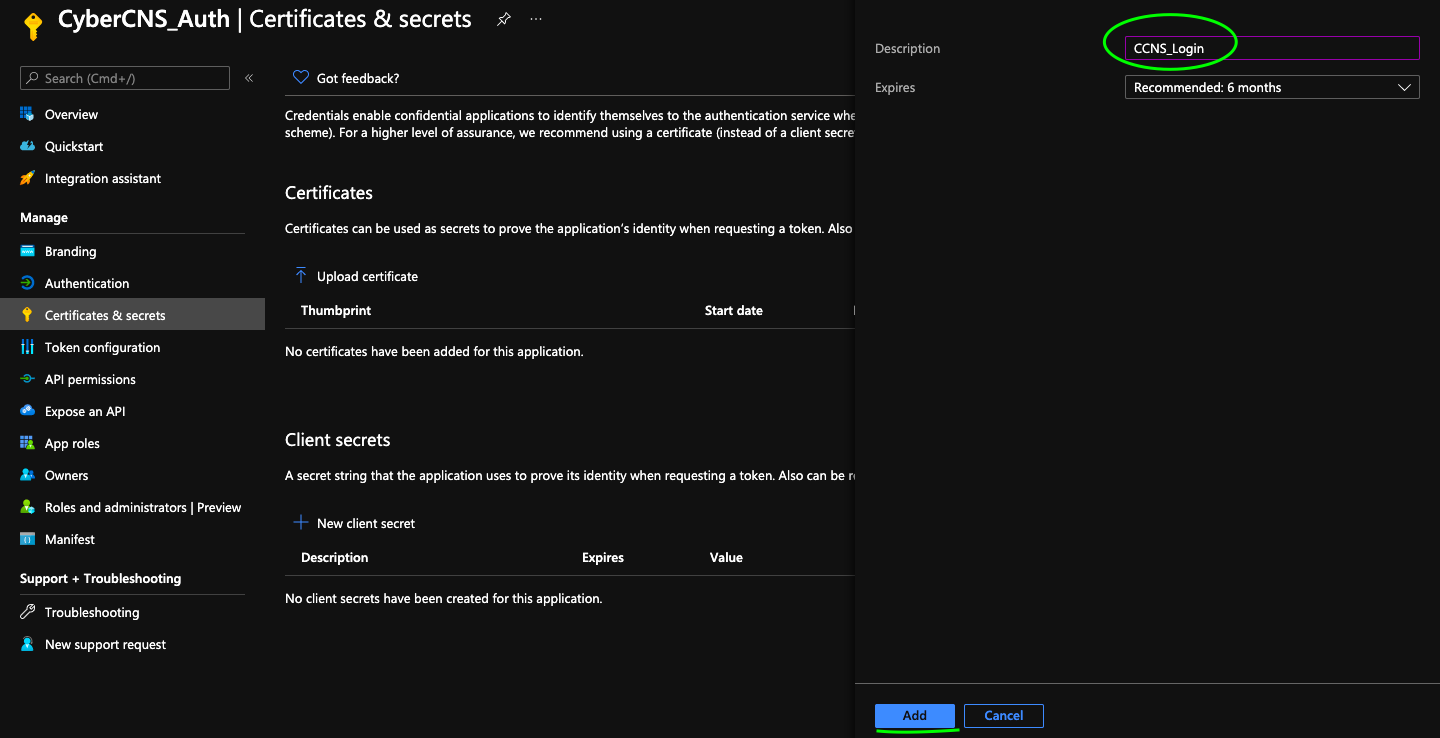
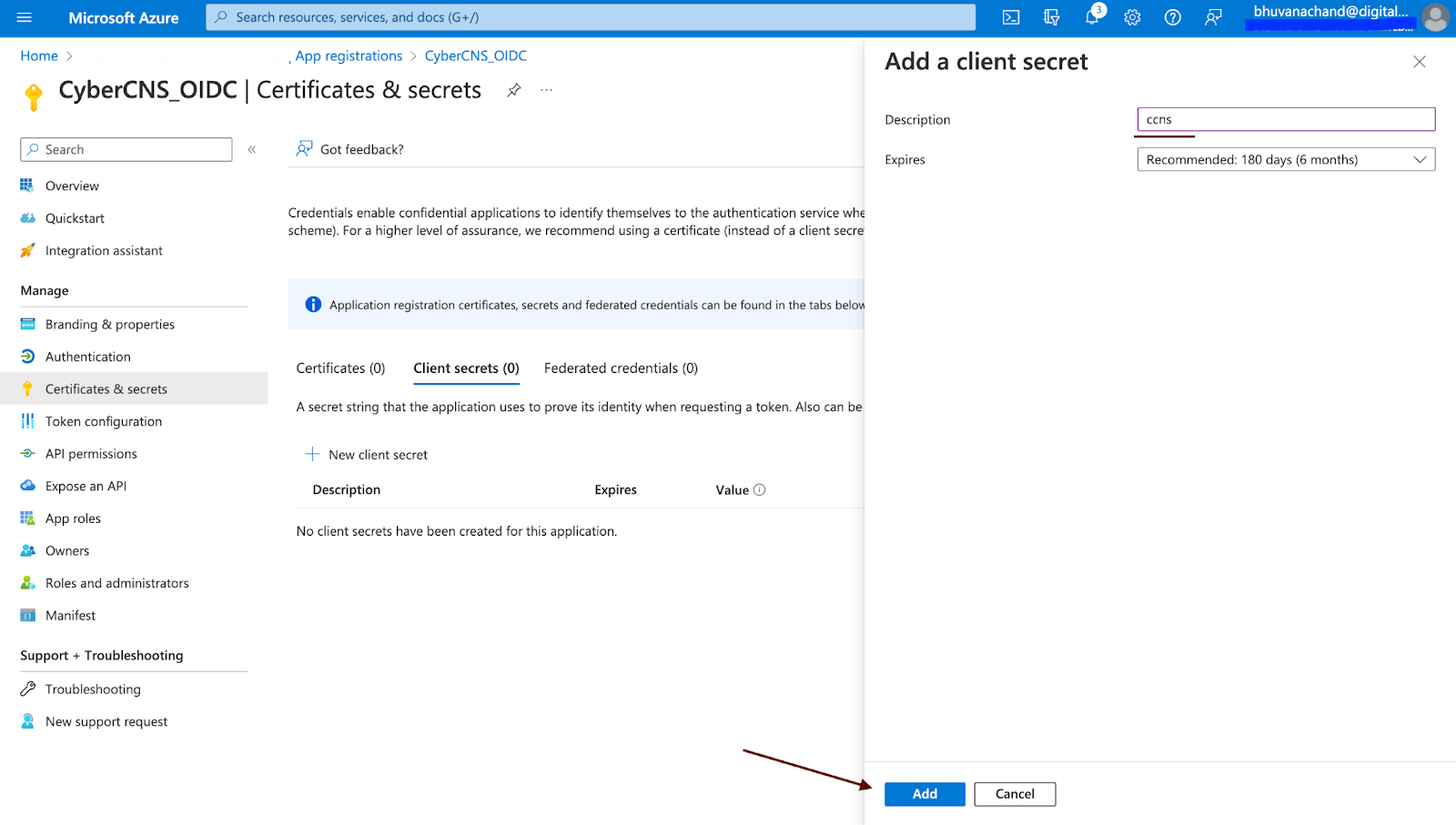
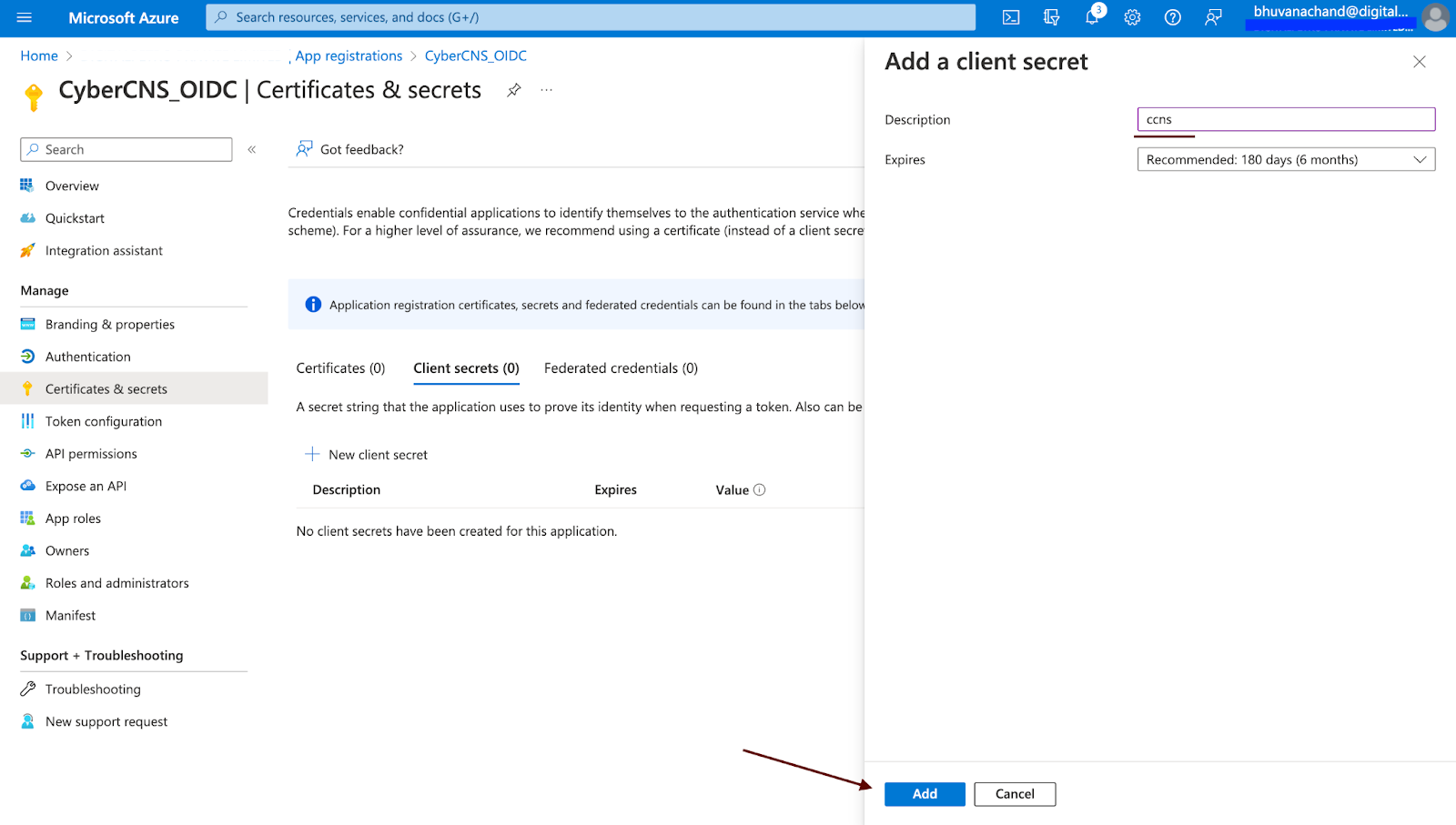
Create a New Client Secret for this application.
Provide a description for this new client secret and click on Add.
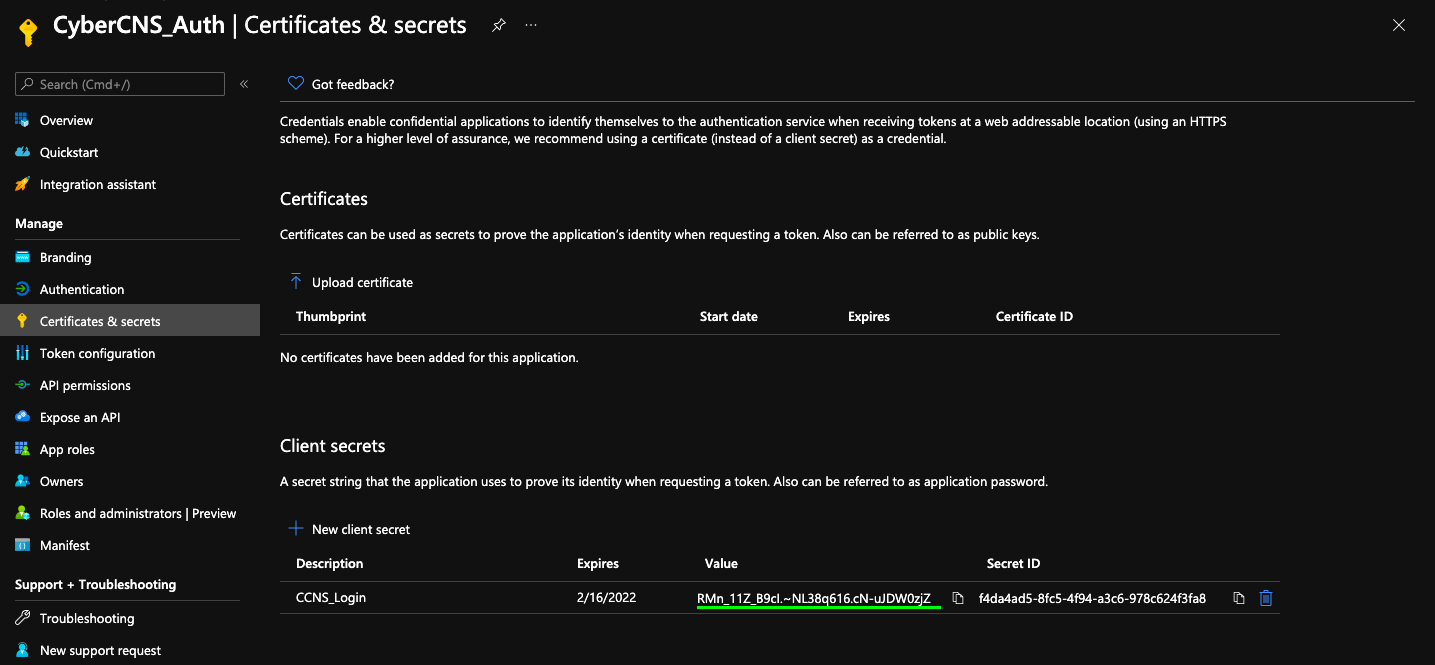
Once added an auto-generated Value will be seen. Copy this Value and use it as a Client Secret into CyberCNS Portal.
Once all required details are added into CyberCNS, Save Authentication Providers. This completes the setup for authentication providers.
To redirect to cybercns portal from My Apps Please follow the steps below
Step 1: Goto App registration and select the CyberCNS application
Step 2: Select the “Branding & properties” of the application.
Step 3: Update the URL HomePage URL based on your region and update the tenant name
https://portaluseast2.mycybercns.com/api/<tenantname>/authorize
https://portalapsoutheast2.mycybercns.com/api/<tenantname>/authorize
https://portaluswest2.mycybercns.com/api/<tenantname>/authorize
https://portaleuwest2.mycybercns.com/api/<tenantname>/authorize
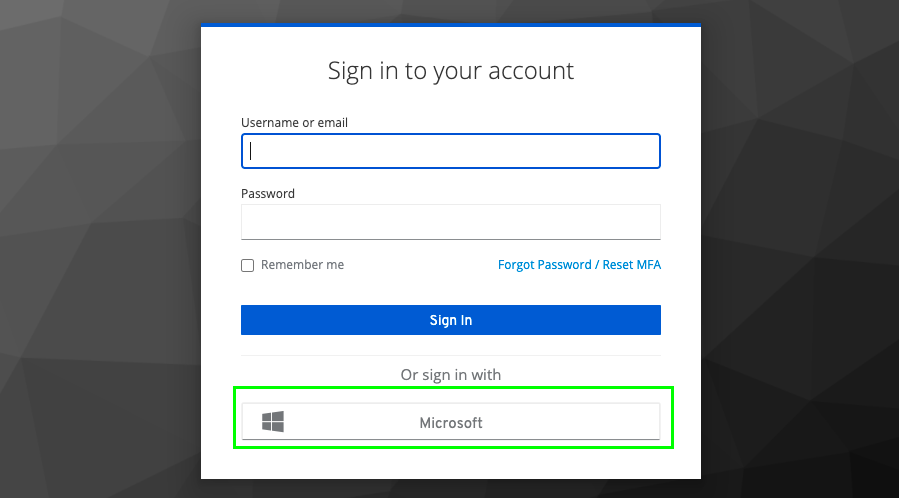
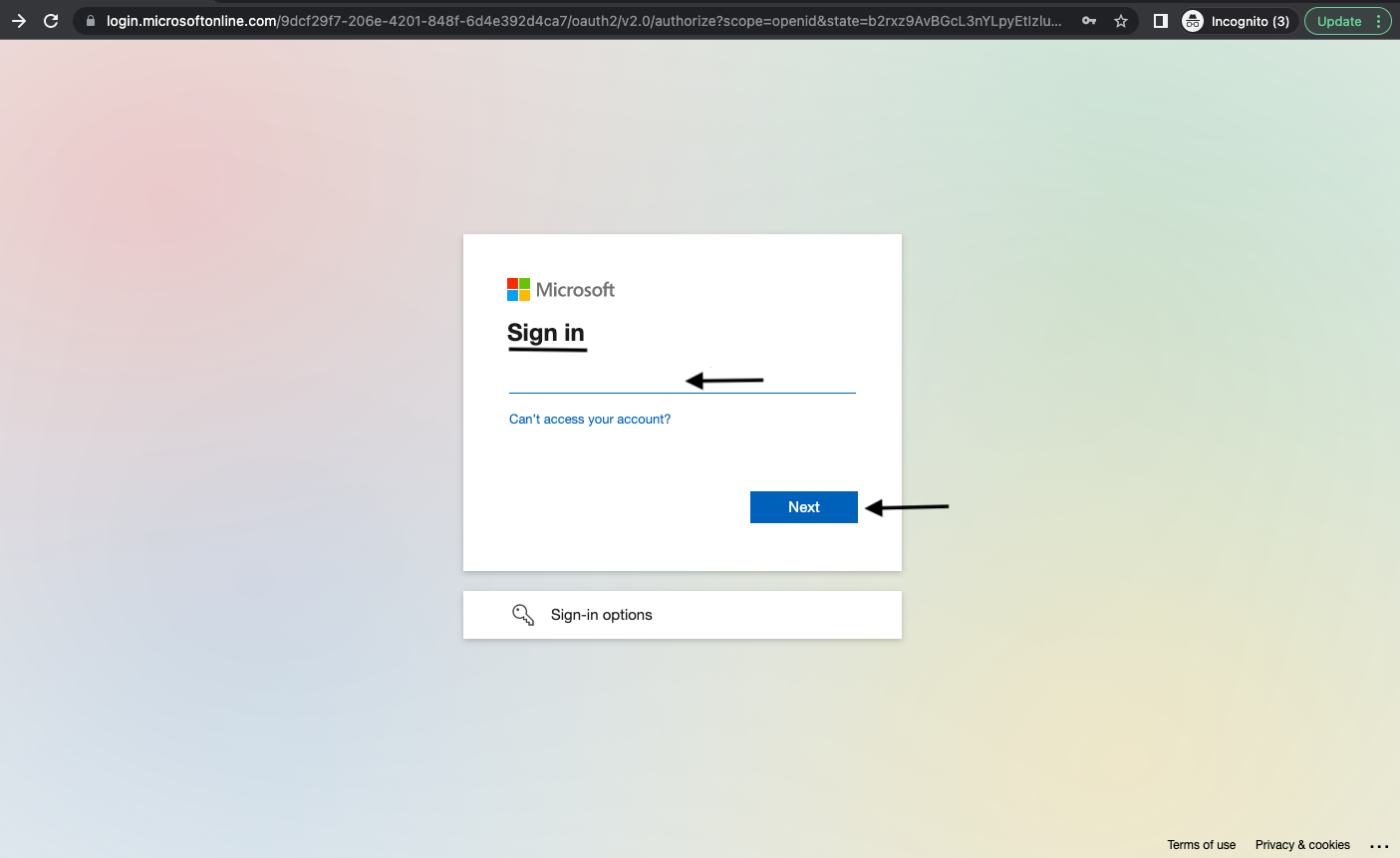
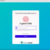
https://portaleucentral1.mycybercns.com/api/<tenantname>/authorizeNavigate to the sign-in page for CyberCNS and select the Microsoft option to sign in.
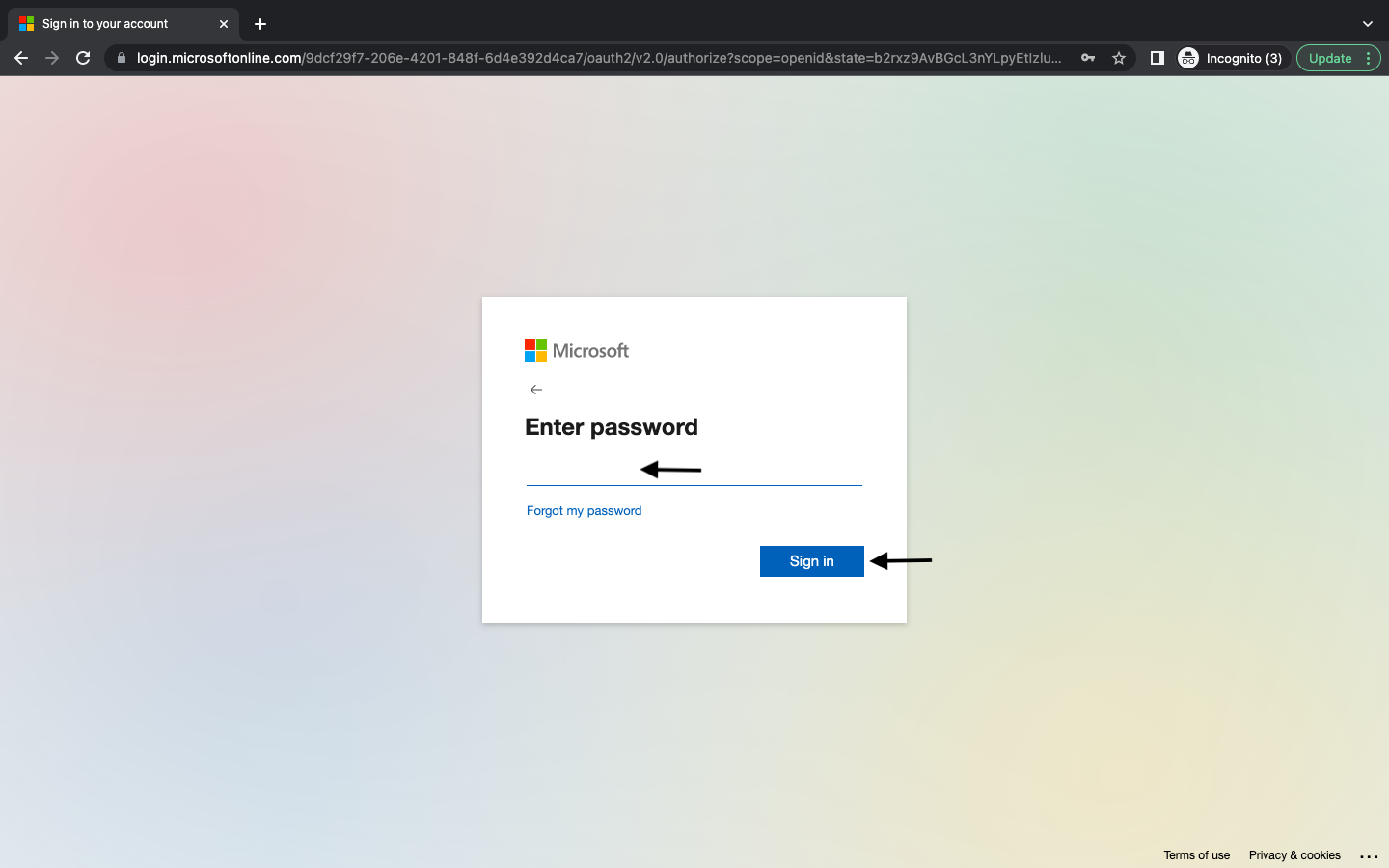
Provide Microsoft login details as requested for successful login to CyberCNS.
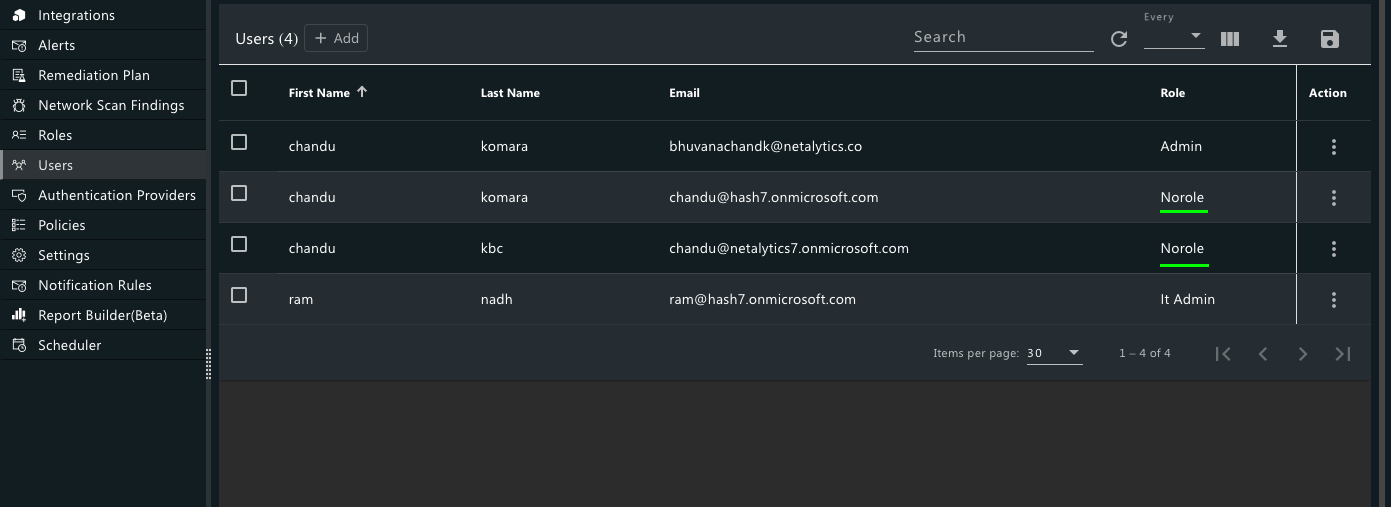
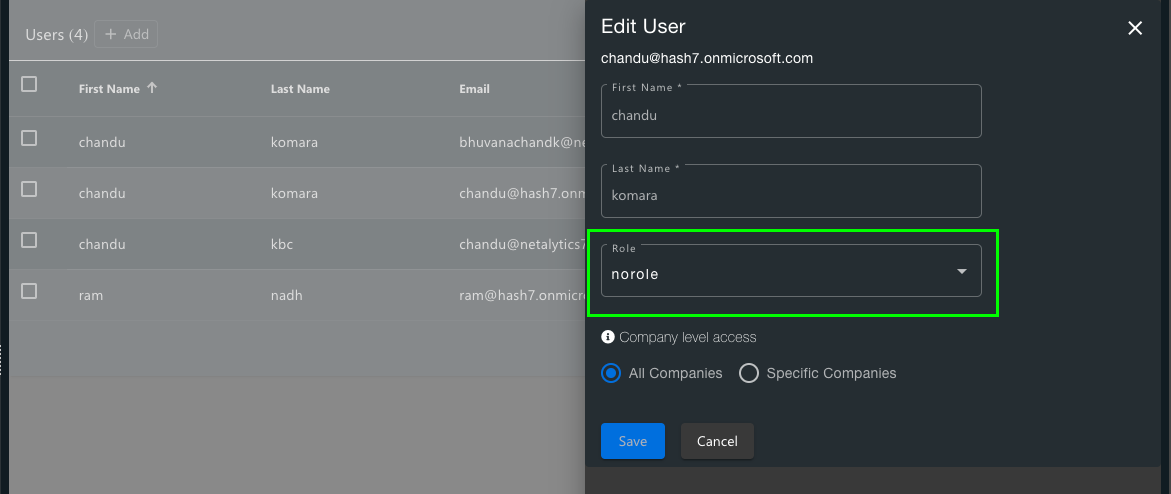
In case the user does not exist in CyberCNS then it will be auto-created but will not have any role attached to it. The role assigned will be No role. Users will be asked to request the admin to assign a role.
CyberCNS admin has to assign respective roles to Users with No role. Post role assignment, the user will be able to successfully login into CyberCNS using Microsoft authentication.
Gitlab
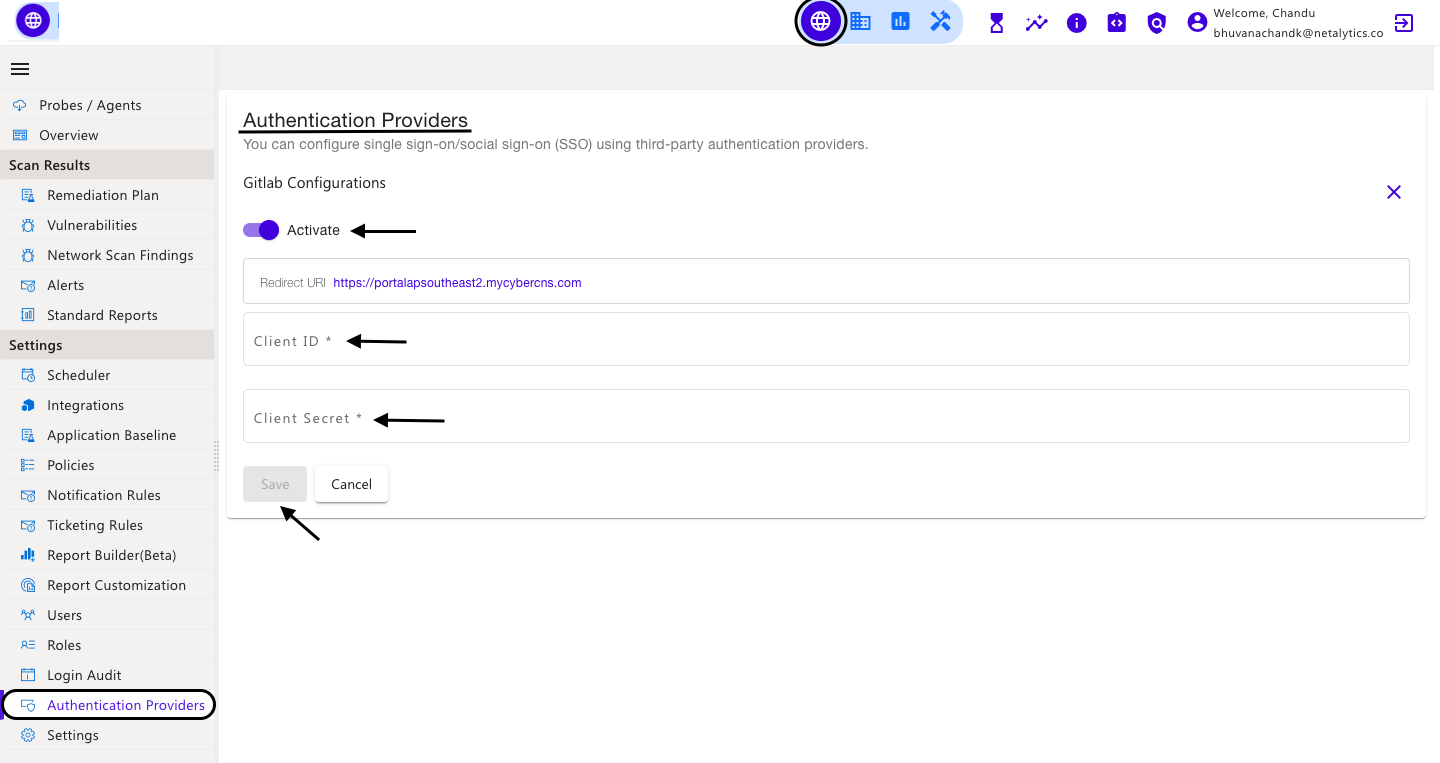
In the CyberCNS portal navigate to Global Settings>Authentication Providers and select Gitlab.
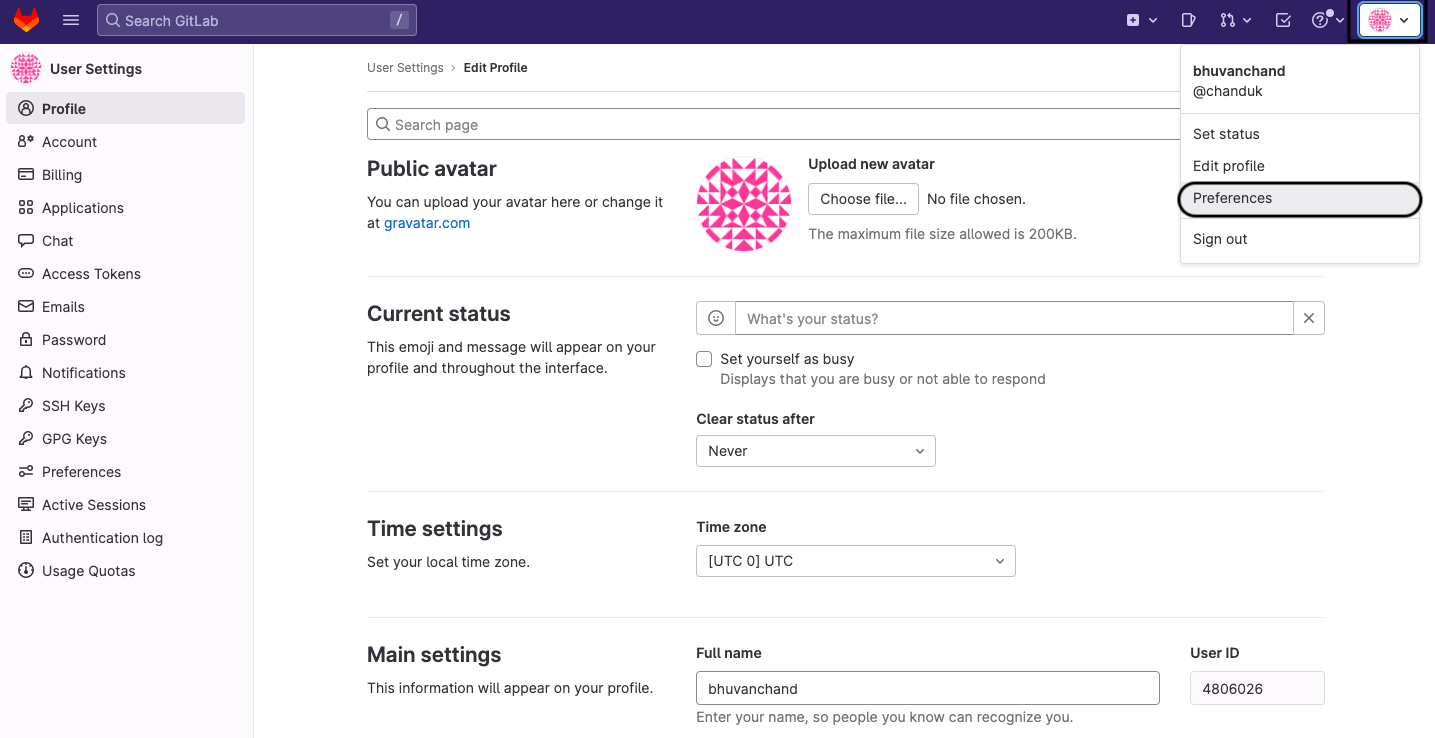
Navigate to the Preferences under the Profile settings.
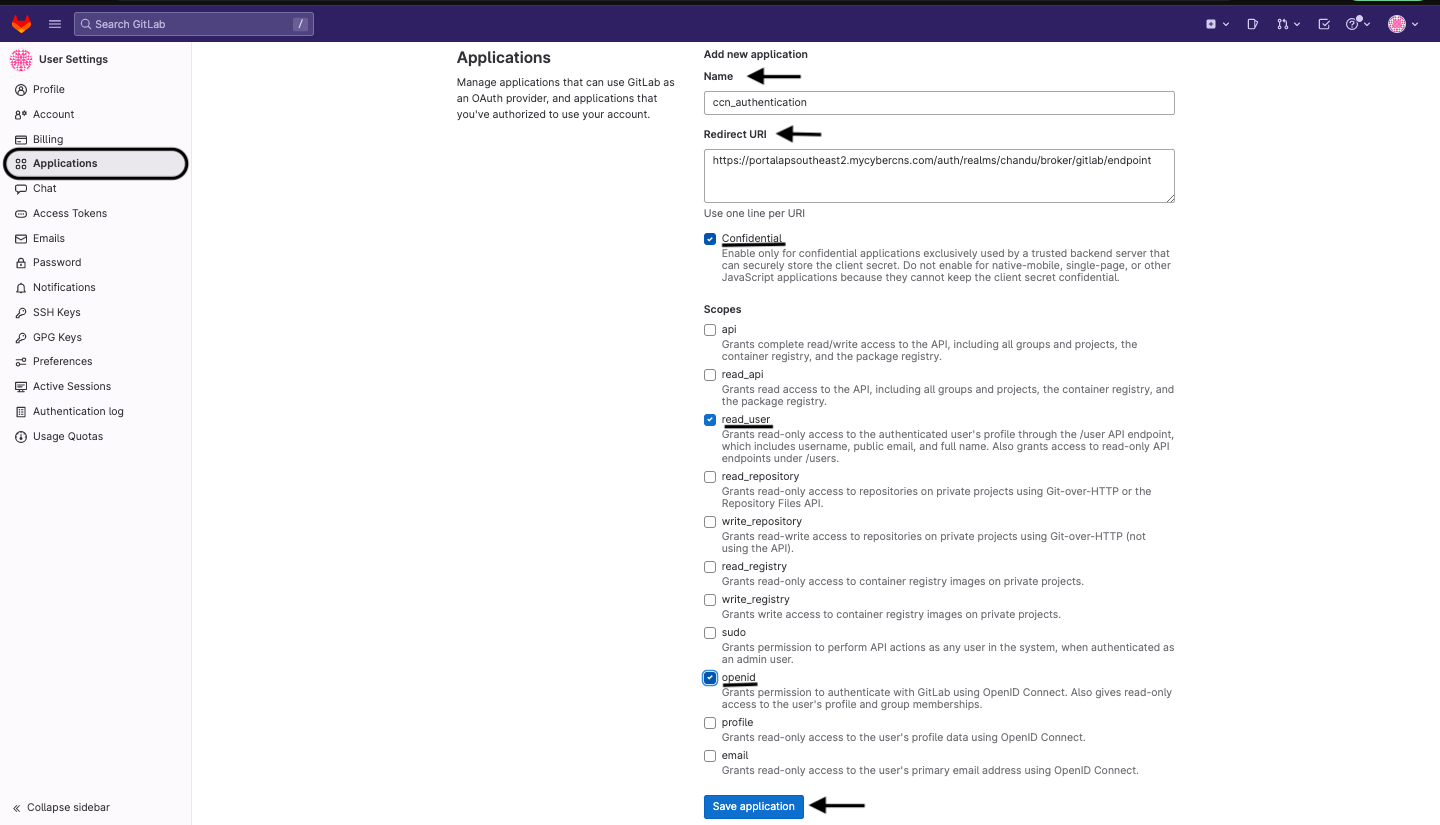
In the Applications tab, enter a new application name, Redirect URL, and click on Save application.
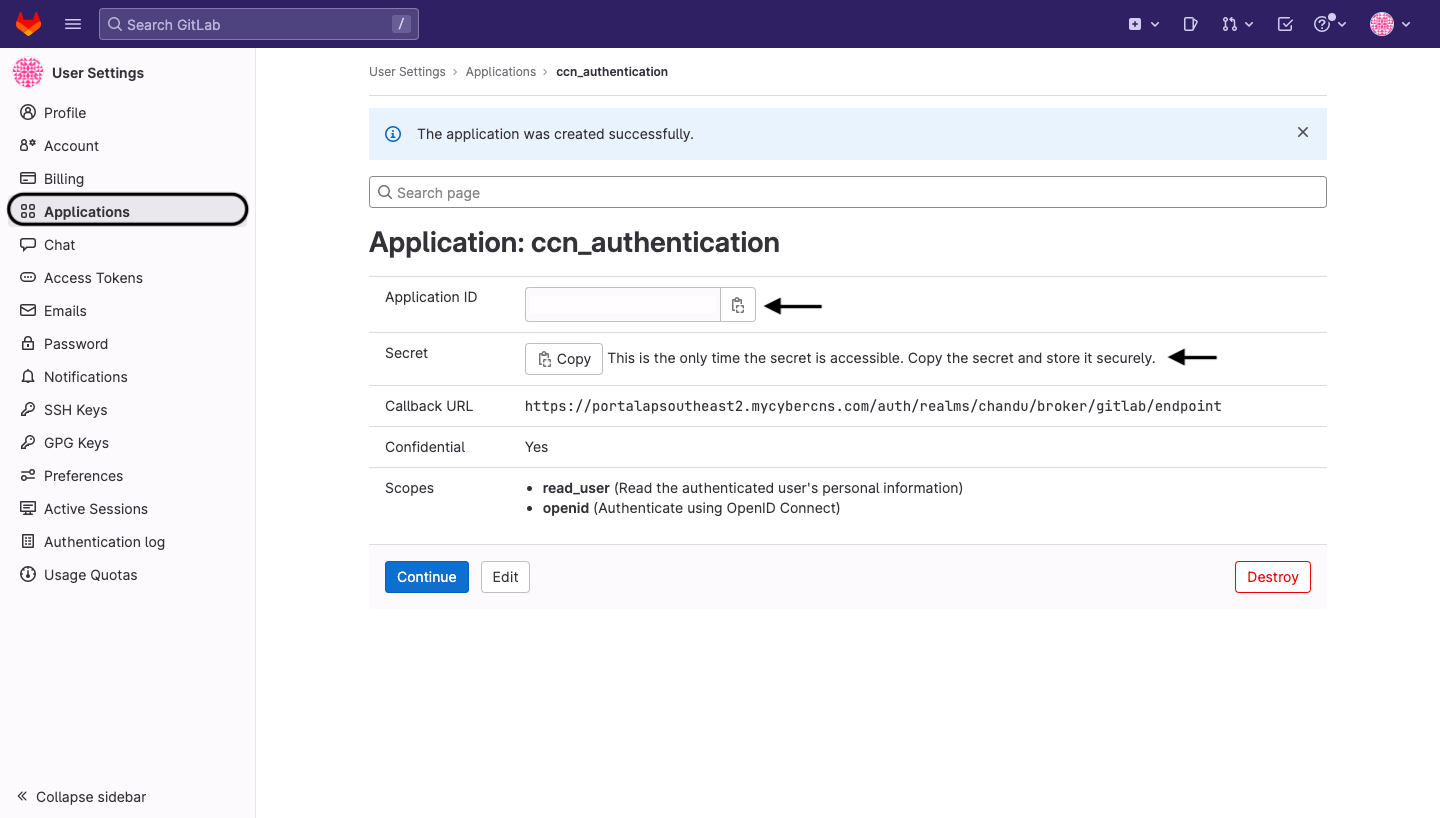
Once the application created successfully, copy the Application ID(Client ID) and Secret key(Client Secret) to enter to the CyberCNS portal.
Once all required details are added into CyberCNS, Save Authentication Providers. This completes the setup for authentication providers.
When the Gitlab is added, go back to the home page it shows as Authenticated(:green_tick_mark:).
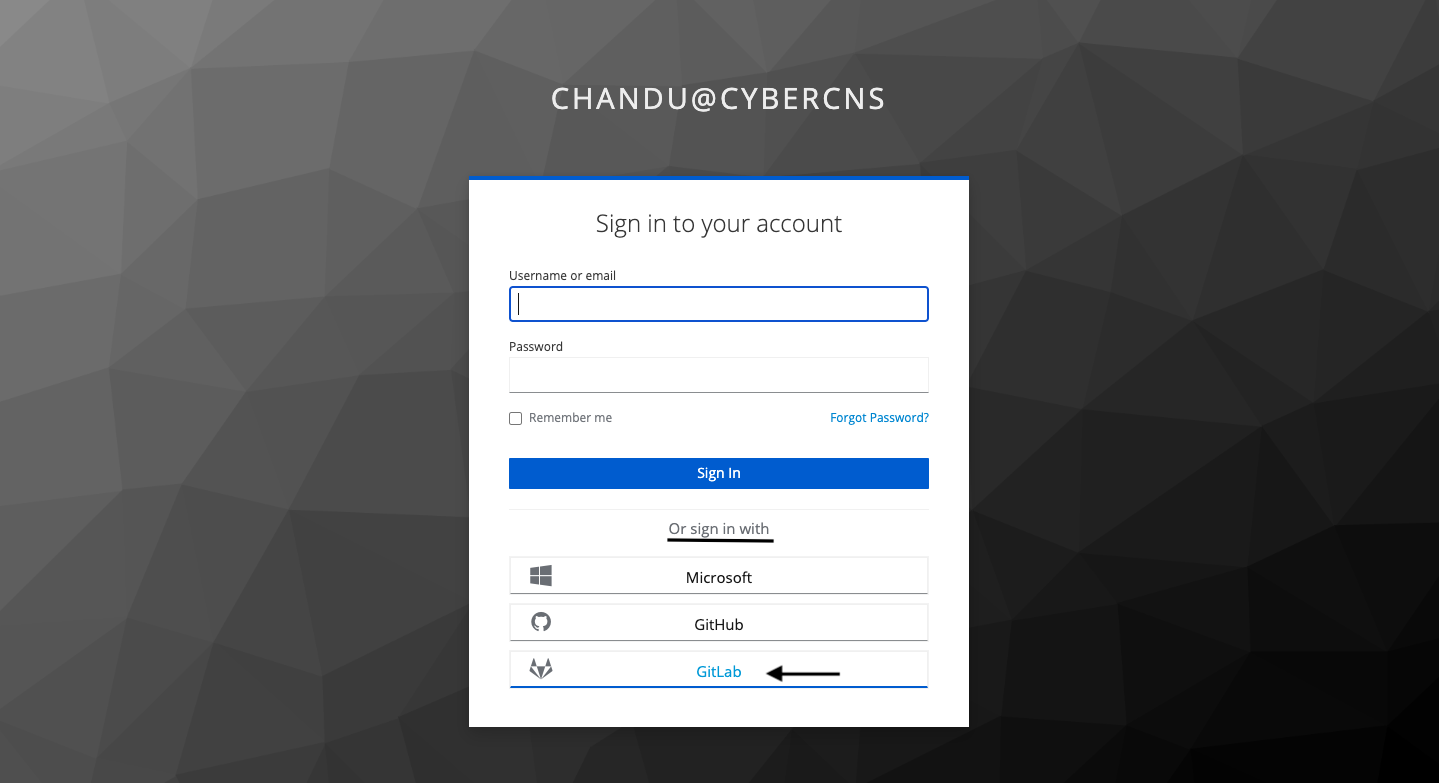
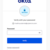
Navigate to the sign-in page for CyberCNS and select the GitLab option to sign in.
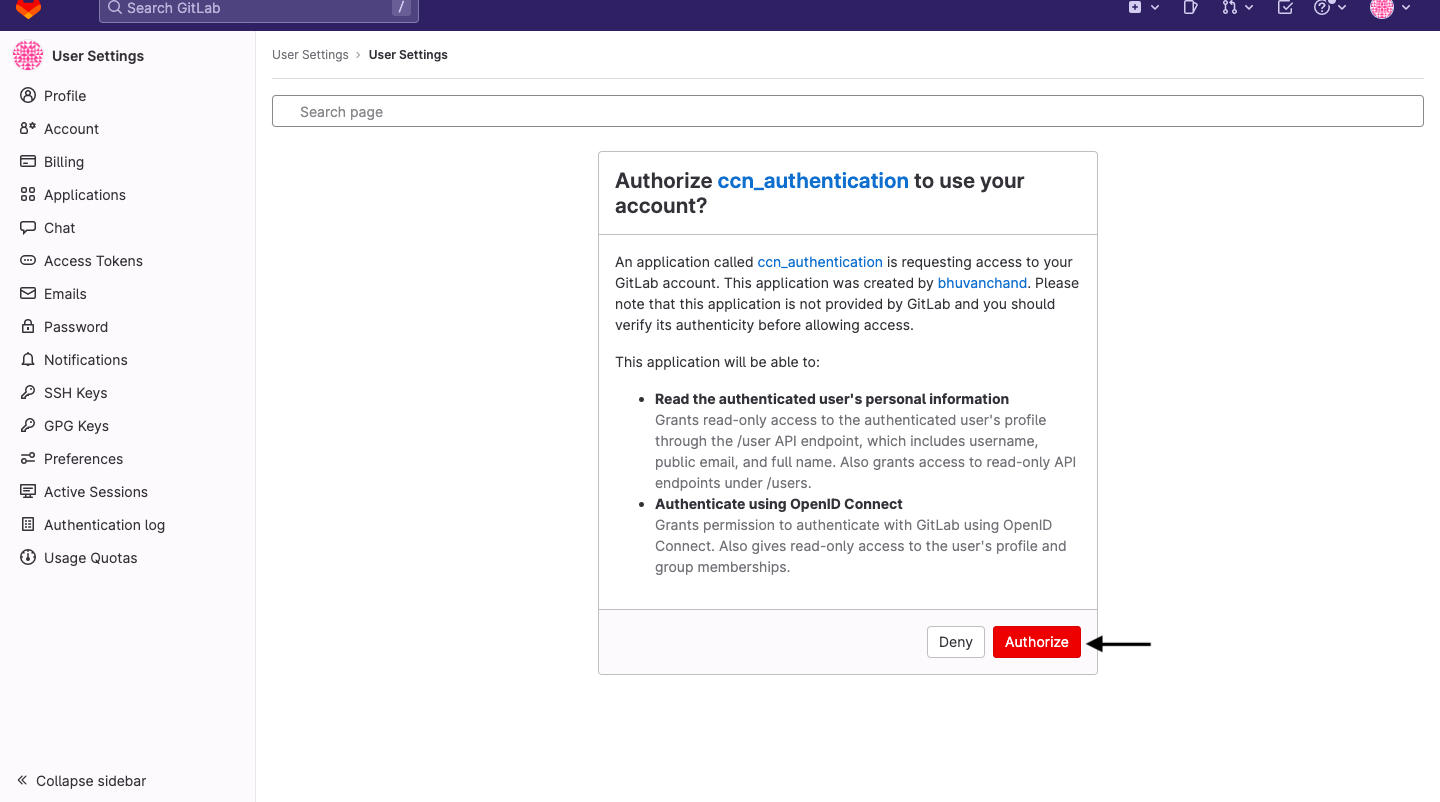
Click on Authorize to sign in.
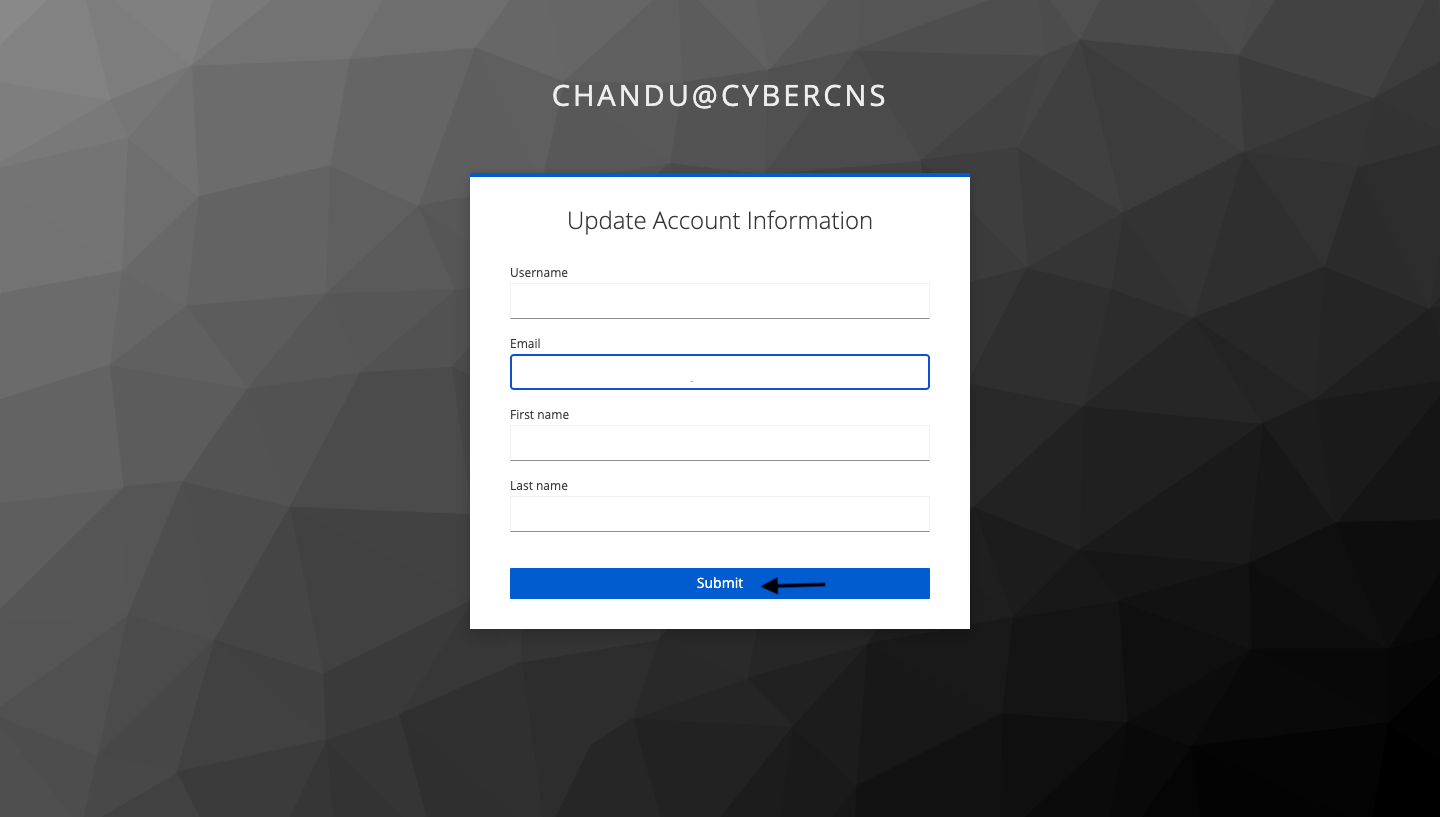
Provide Account Information such as Username, Email, First name, and Last name as requested for successful login to CyberCNS.
Click on Submit Button.
GitHub
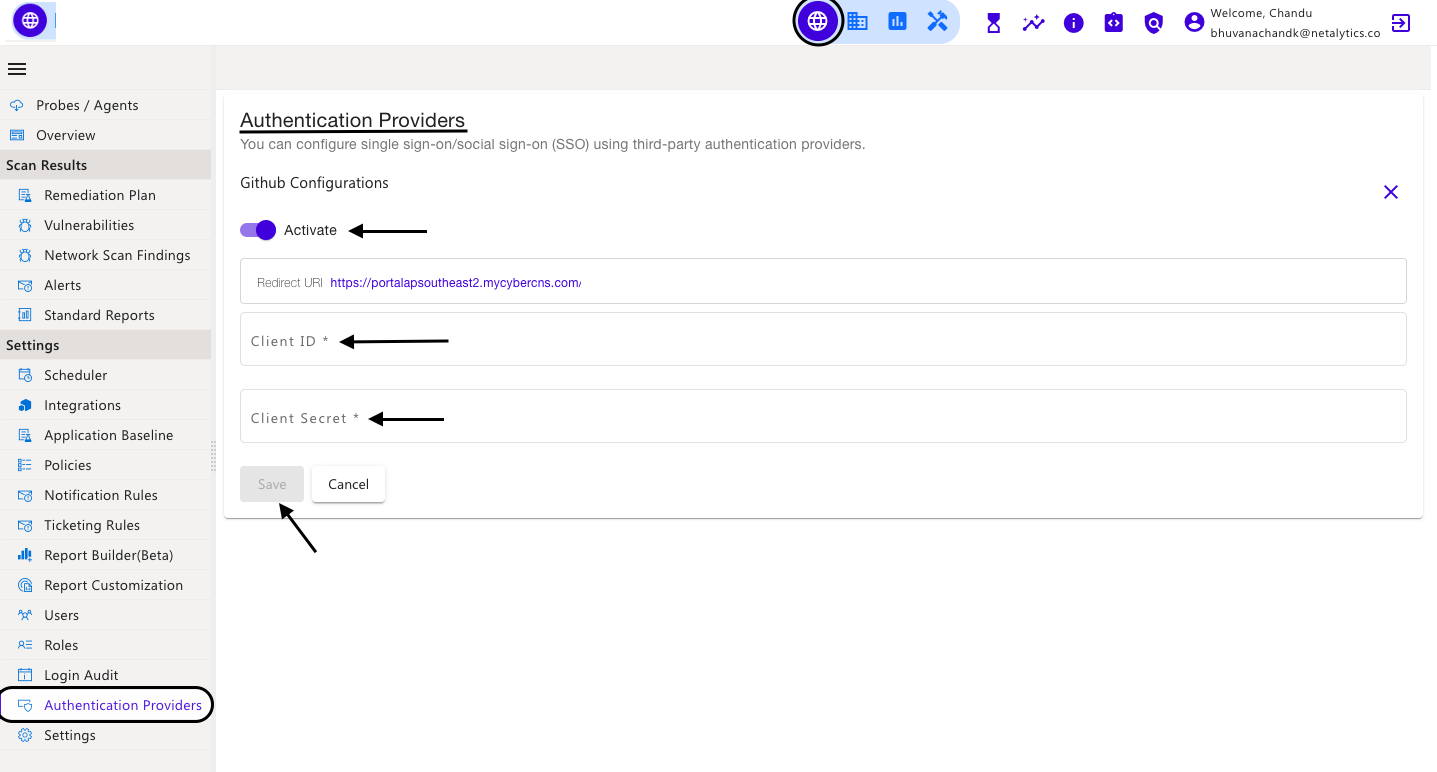
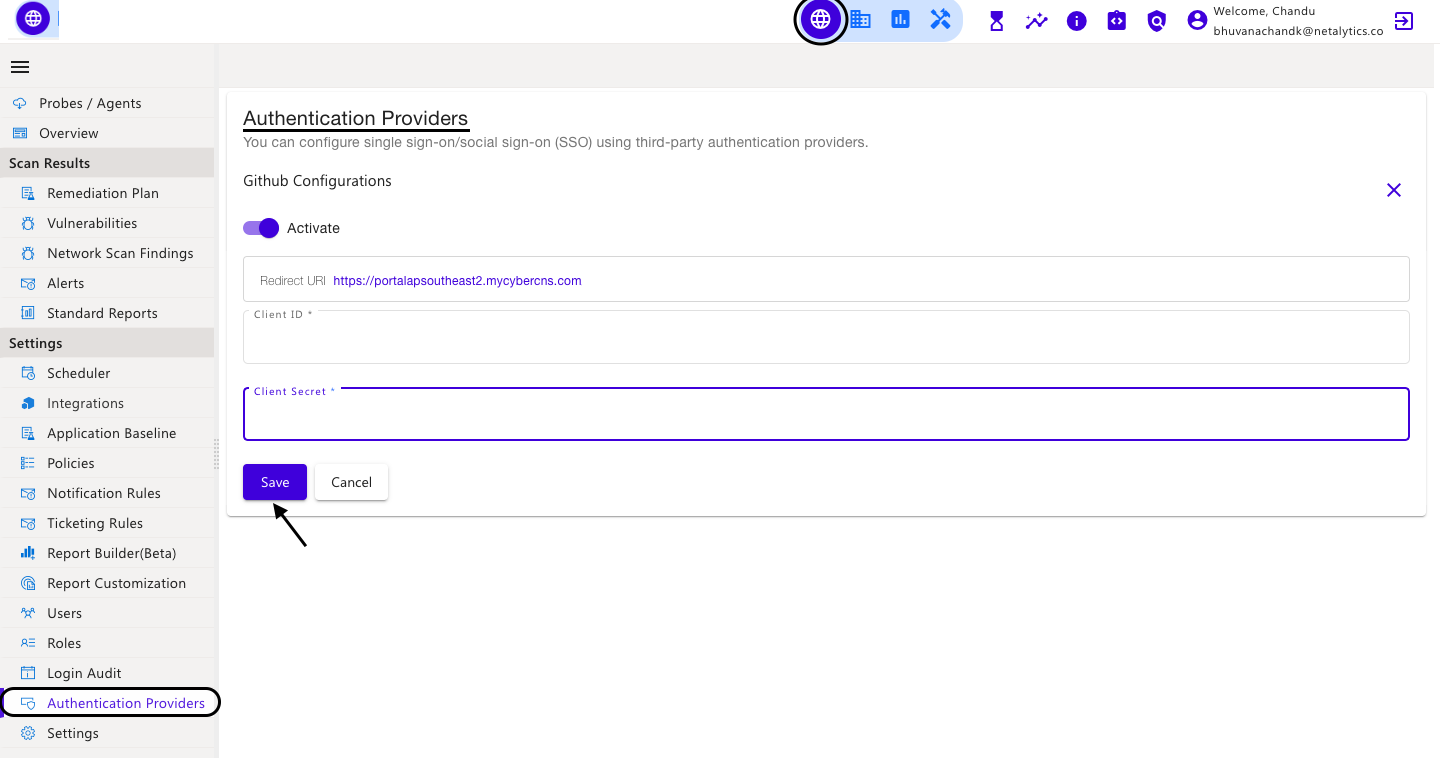
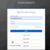
In the CyberCNS portal navigate to Global Settings>Authentication Providers and select GitHub.
You can configure single sign-on/social sign-on (SSO) using third-party authentication providers.
Enter the required fields to login through Github and click on Save.
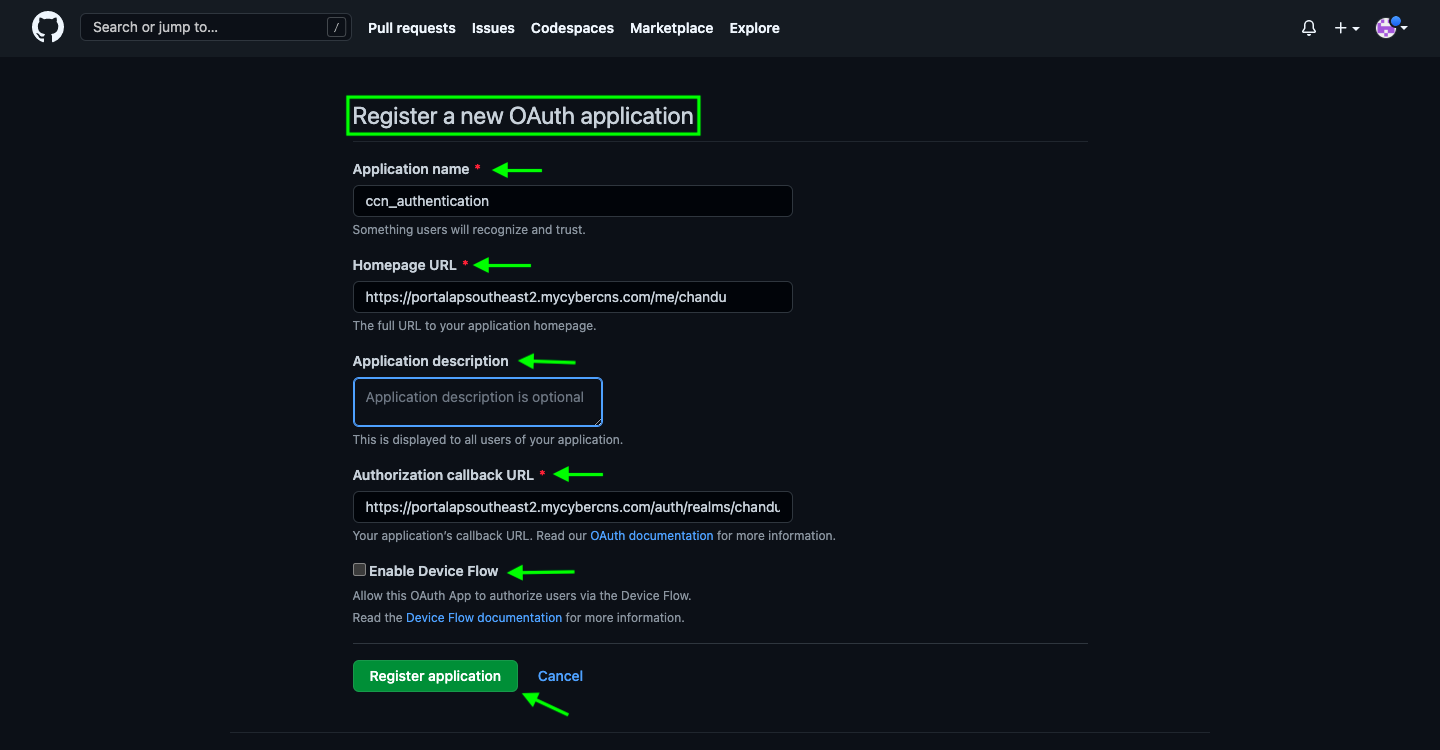
In the Register a new OAuth application page, enter an Application Name of your choice for app registration.
Also, mention the Homepage URL, Application Description, Authorization callback URL, Enable Device Flow, and click on Register application to successfully register an application. (Redirect URL to be copied from CyberCNS)
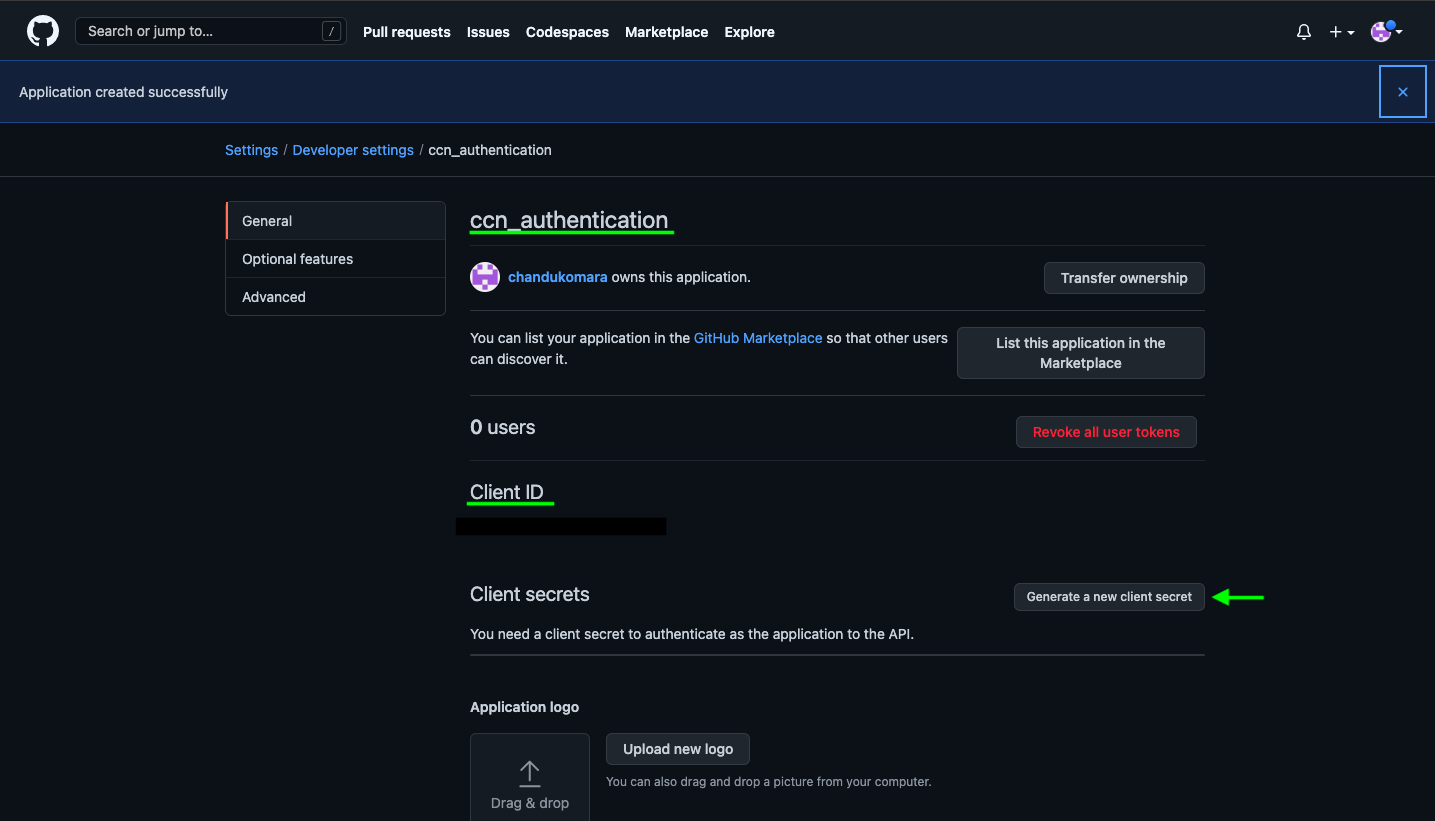
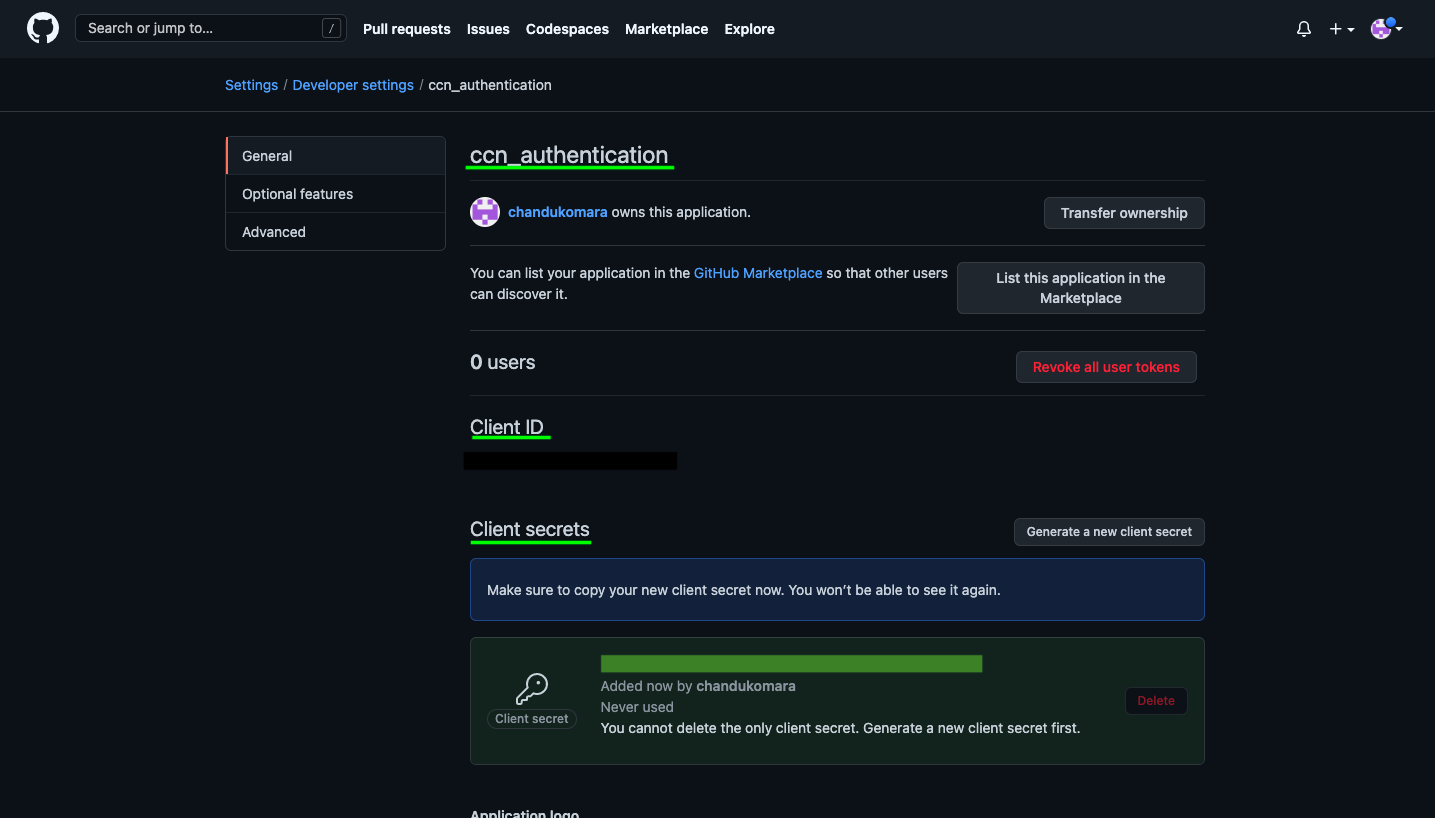
In ccn_authentication copy the Application (Client) ID from here to be provided into the CyberCNS portal and click on Generate a new client secret to provide into the CyberCNS portal.
Copy the Client Secret from here to be provided into the CyberCNS portal.
Once all required details are added into CyberCNS, Save Authentication Providers. This completes the setup for authentication providers.
When GitHub is added, go back to the home page in Authentication Providers, and it shows as Authenticated(:green_tick_mark:).
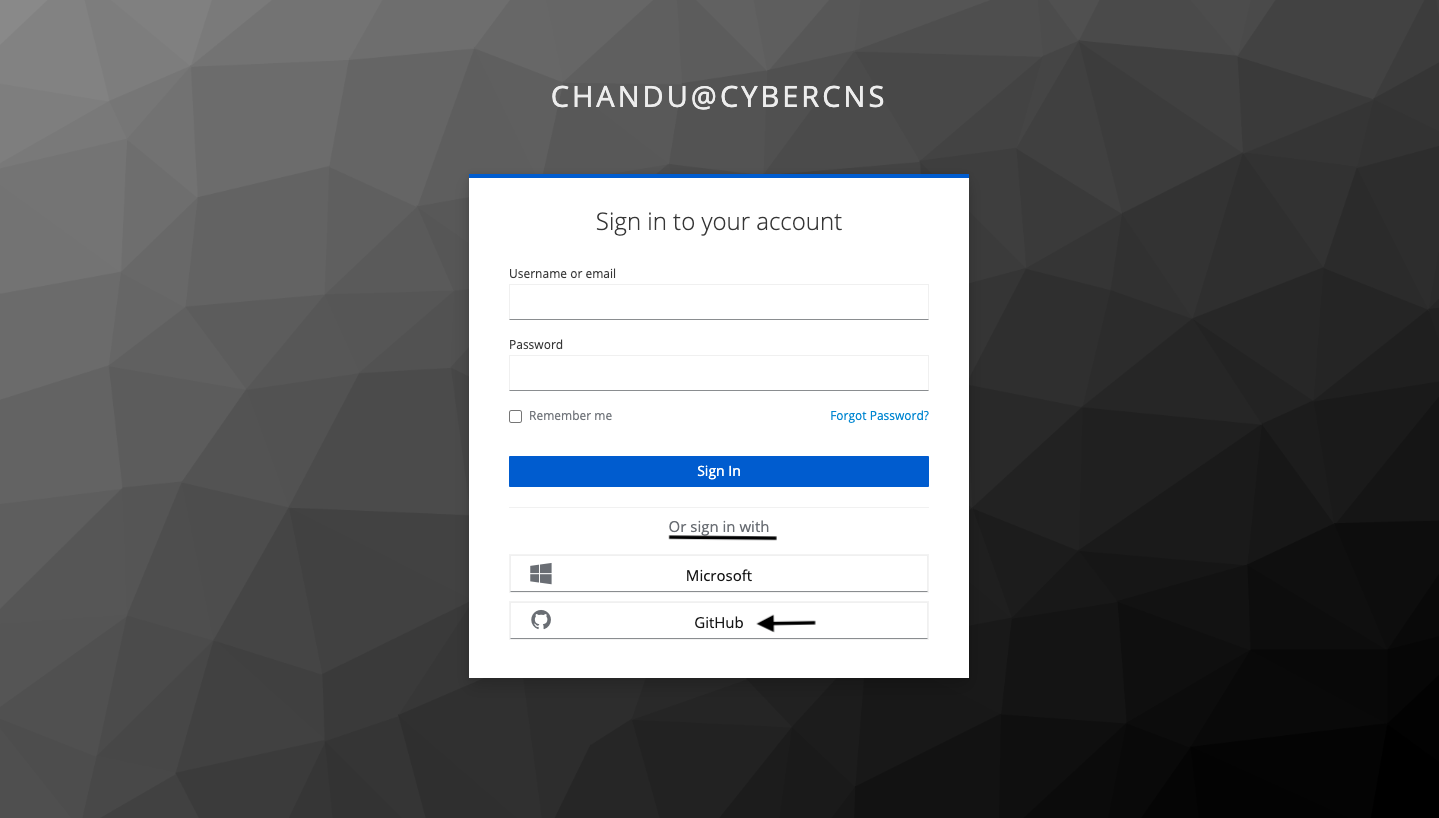
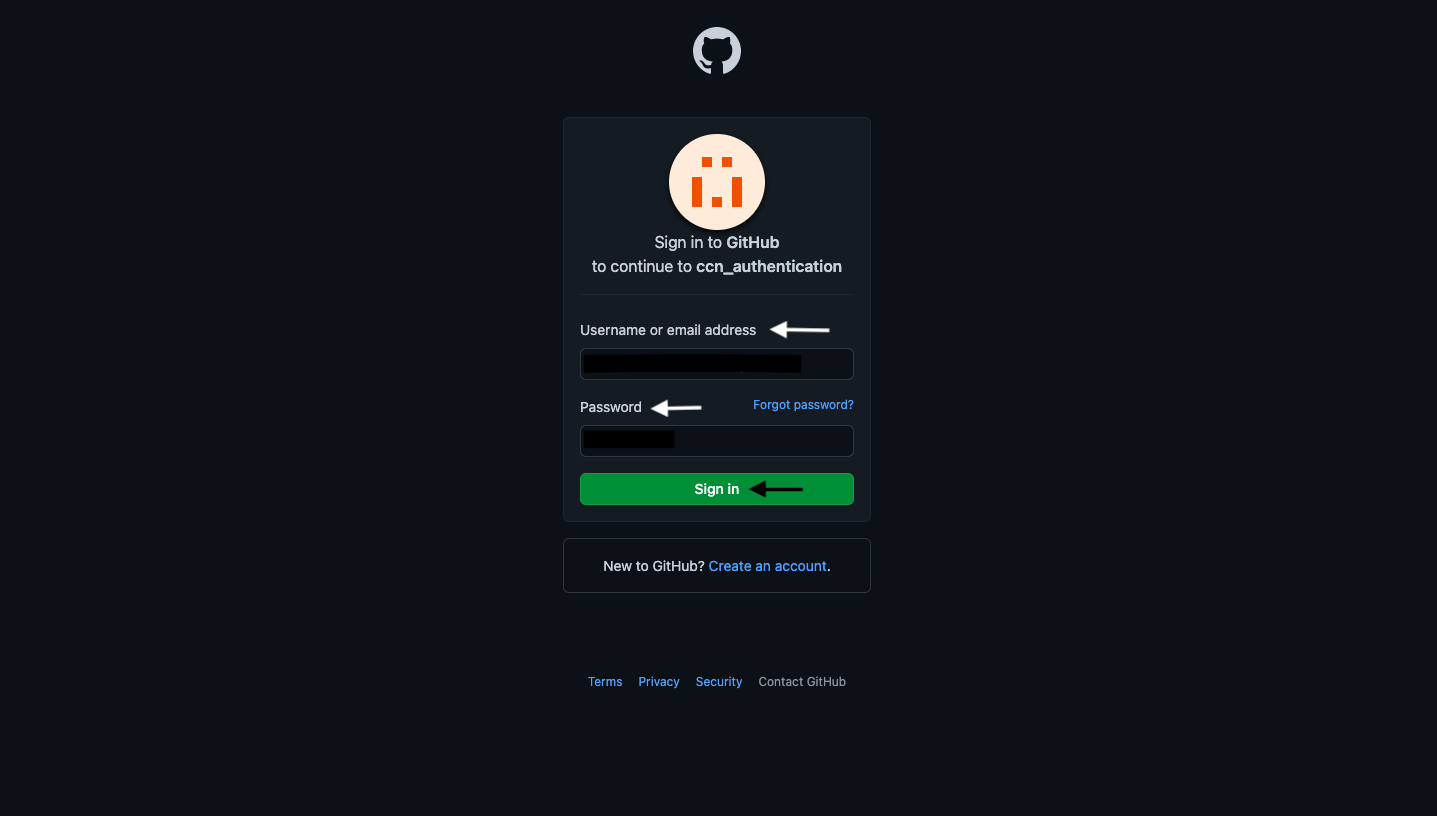
Navigate to the sign-in page for CyberCNS and select the GitHub option to sign in.
Provide Account Information such as Username or Email address and Password as requested for successful login to CyberCNS.
Click on Sign-in Button.
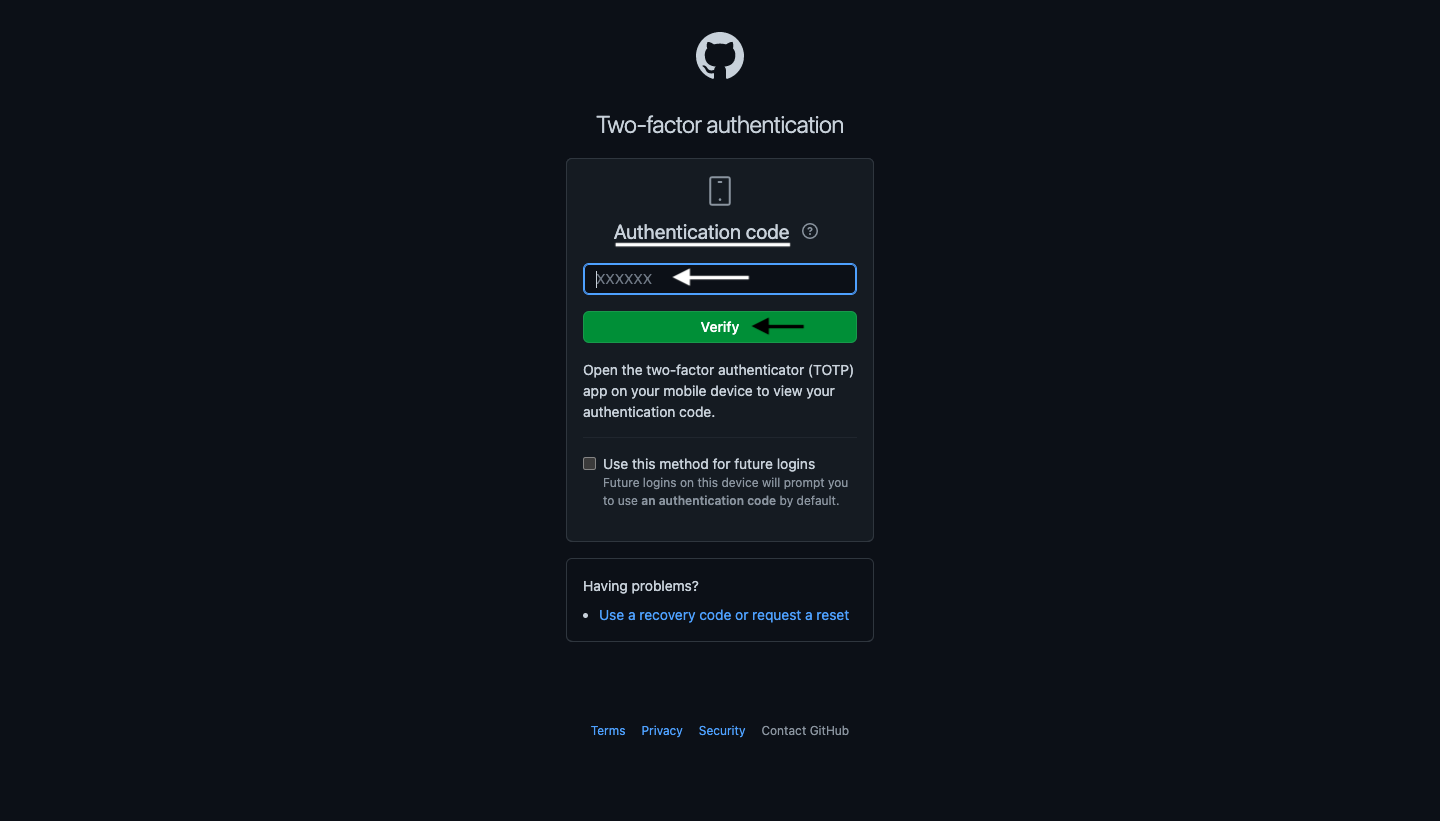
To view your authentication code, launch the two-factor authenticator (TOTP) app on your mobile device. Enter the TOTP and click the Verify button.
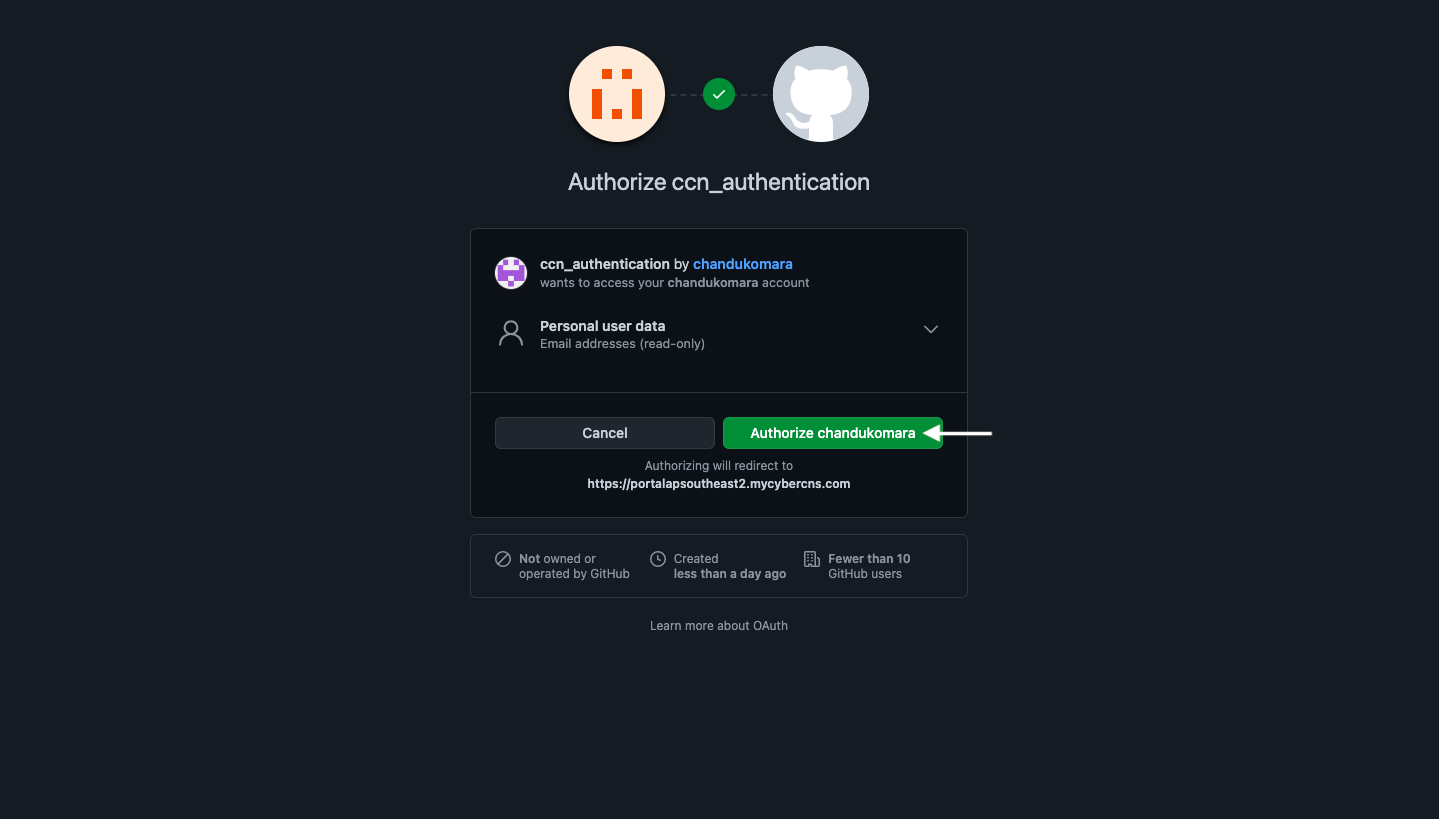
Click on Authorize to sign in.
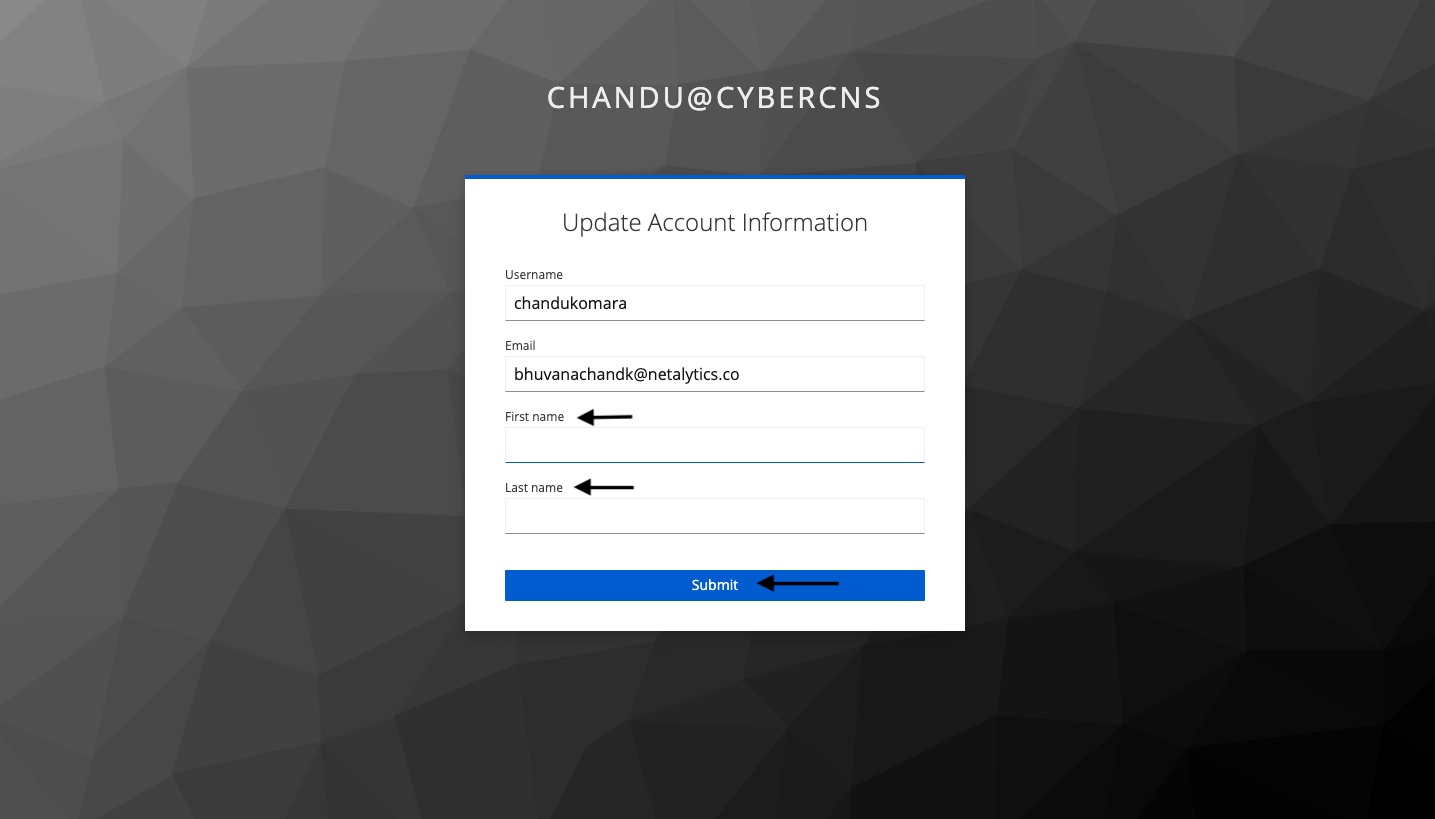
Provide Account Information such as Username, Email, First name, and Last name as requested for successful login to CyberCNS.
Click on Submit Button.
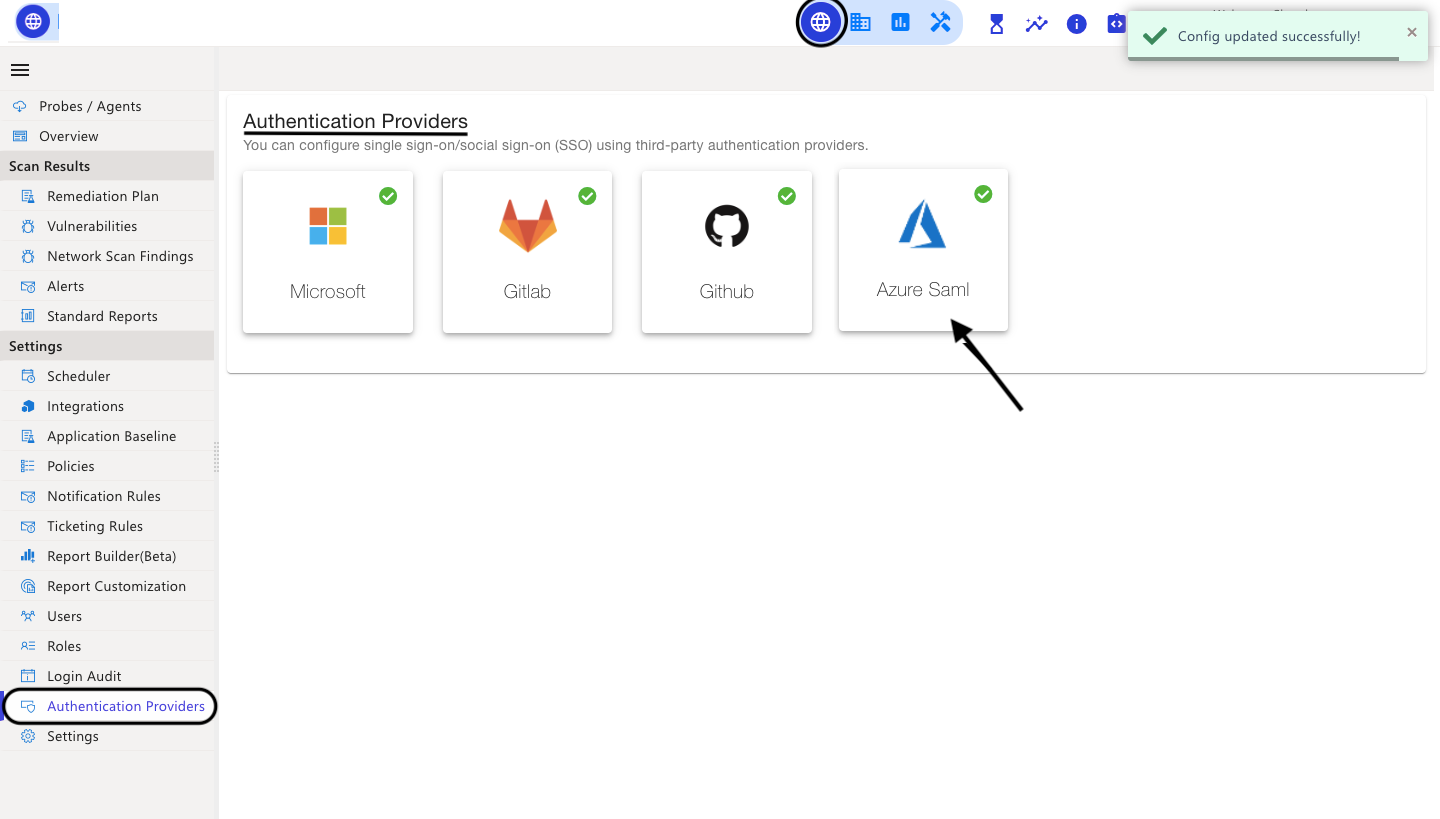
Azure Saml
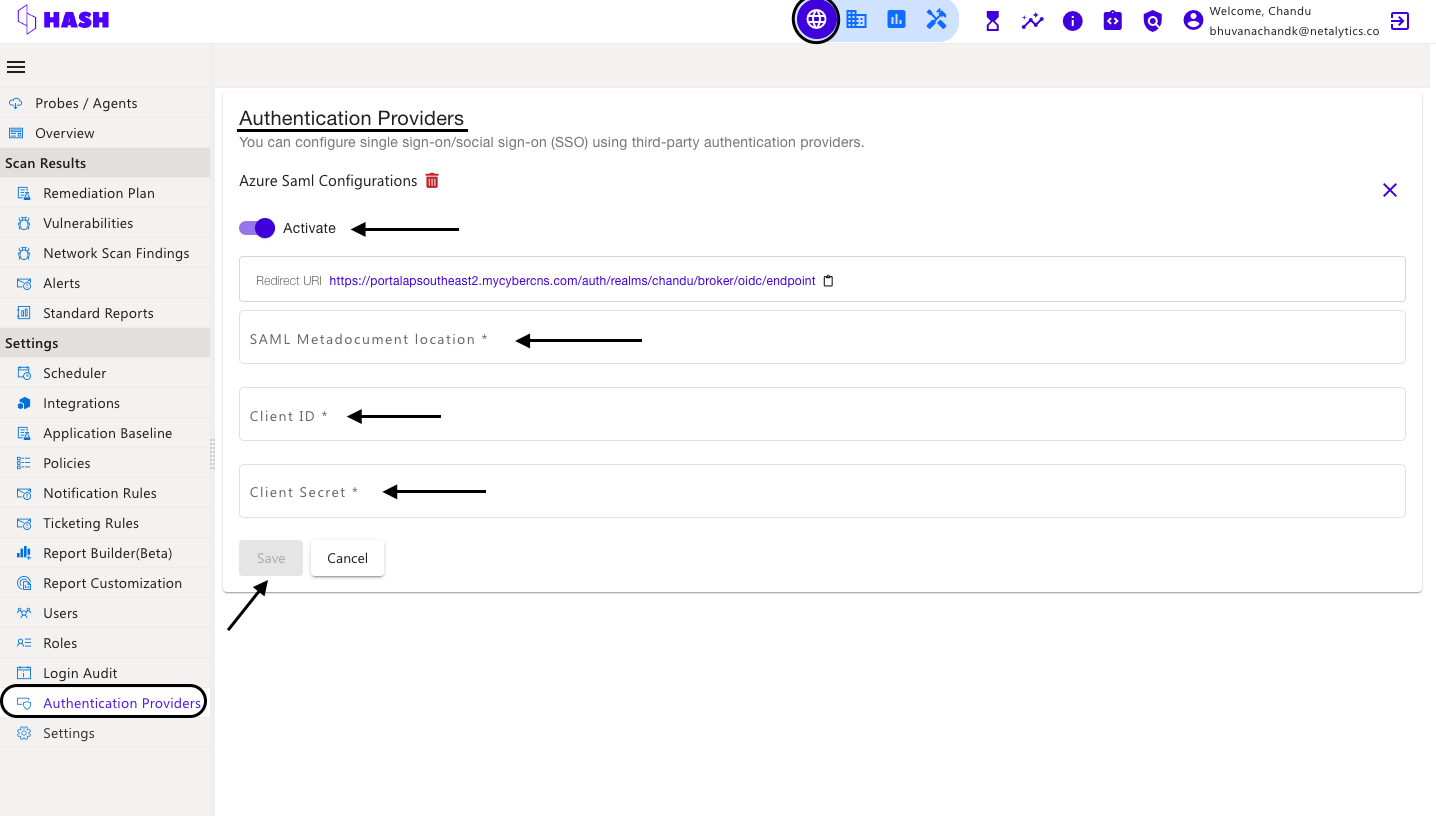
In the CyberCNS portal navigate to Global Settings>Authentication Providers and select Azure Saml.
You can configure single sign-on/social sign-on (SSO) using third-party authentication providers.
Enter the required fields to log in through Azure Saml and click on Save.
All the field values are captured through Microsoft Azure Portal except Alias Name.
Alias Name is the name of choice to appear on the login page using Azure Saml.
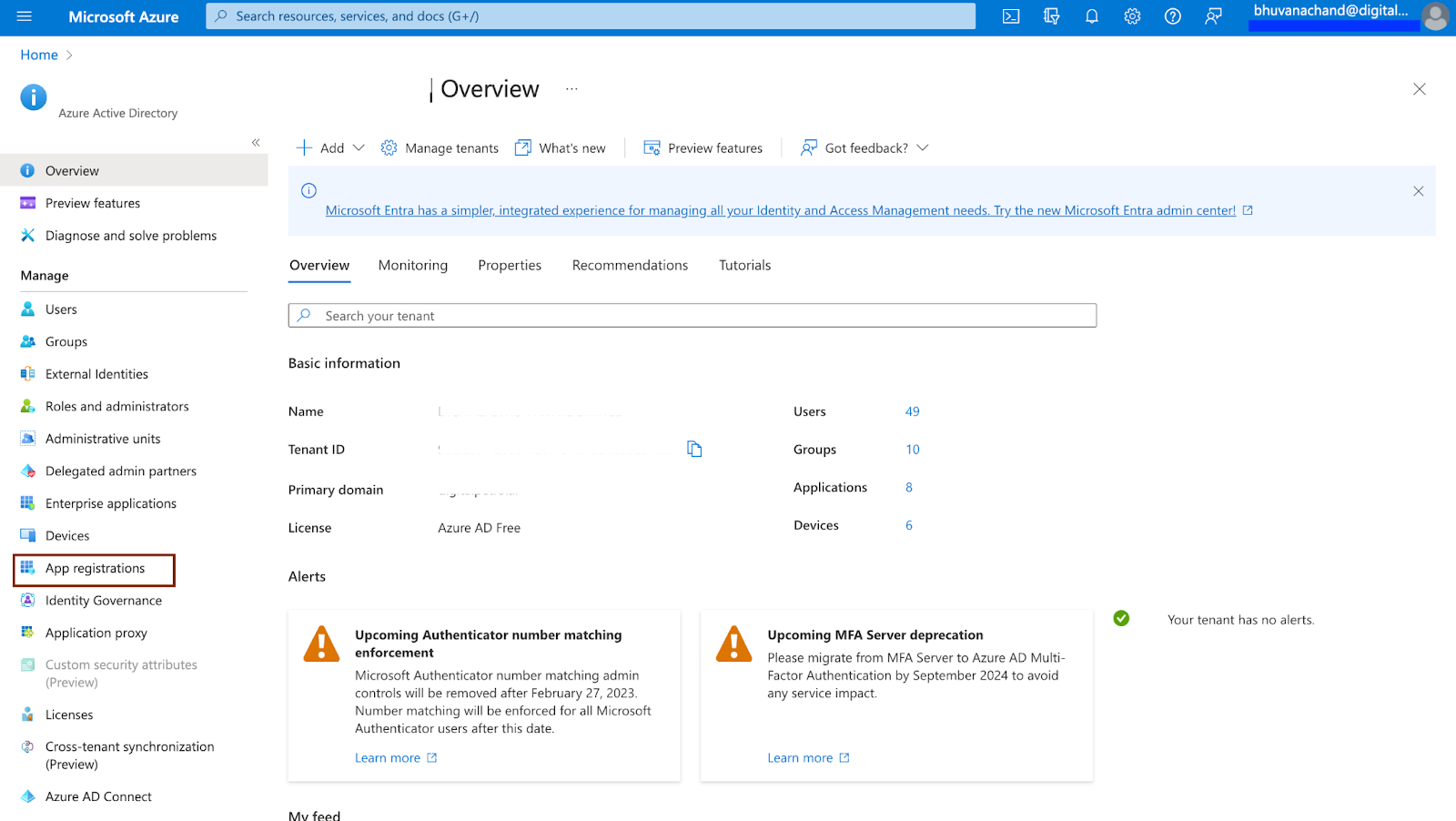
In the Microsoft Azure portal, navigate to App Registrations> New registration.
In the Microsoft Azure portal, navigate to App registrations.
In the Microsoft Azure portal, navigate to App Registrations> New Registration.
Copy the Redirect URL from the CyberCNS portal.
Paste the copied redirect URL to the Microsoft Azure Portal.
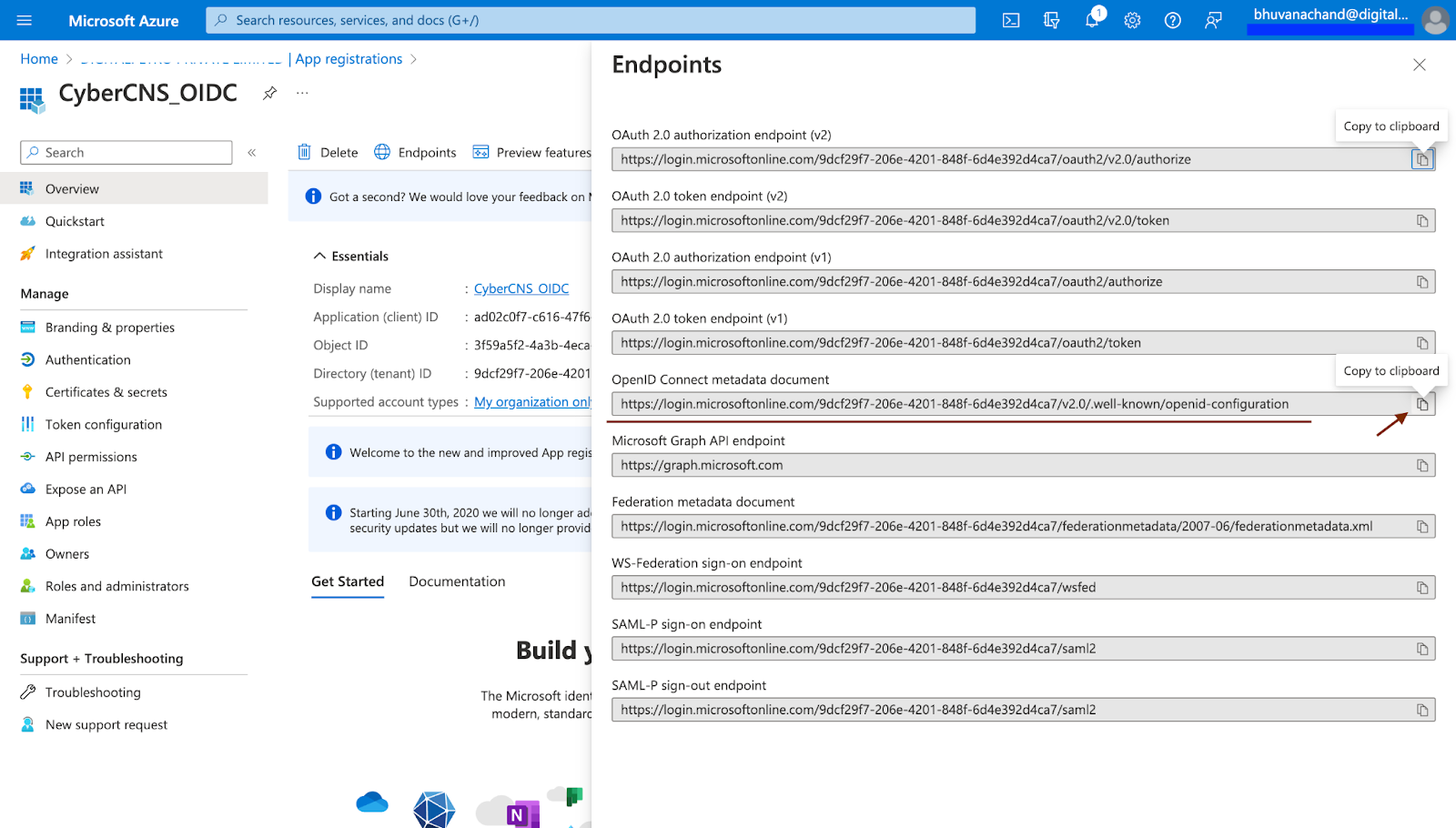
Navigate to Overview and click on Endpoints.
Copy the Azure Saml Connect metadata document.
Paste the Azure Saml Connect metadata document into the CyberCNS portal.
Copy the Application (Client) ID from here to be provided into the CyberCNS portal.
Click on +New Client Secret to create a new client secret ID.
Create a New Client Secret for this application.
Provide a description for this new client secret and click on Add.
Once added an auto-generated Value will be seen. Copy this Value and use it as a Client Secret into CyberCNS Portal.
Once all required details are added into CyberCNS, Save Authentication Providers. This completes the setup for authentication providers.
When Azure Saml is added, go back to the home page in Authentication Providers, and it shows as Authenticated(:green_tick_mark:).
Navigate to the sign-in page for CyberCNS and select the Azure Saml ( Alias Name given will appear here) option to sign in.
Provide Microsoft login details as requested for successful login to CyberCNS.
SAML
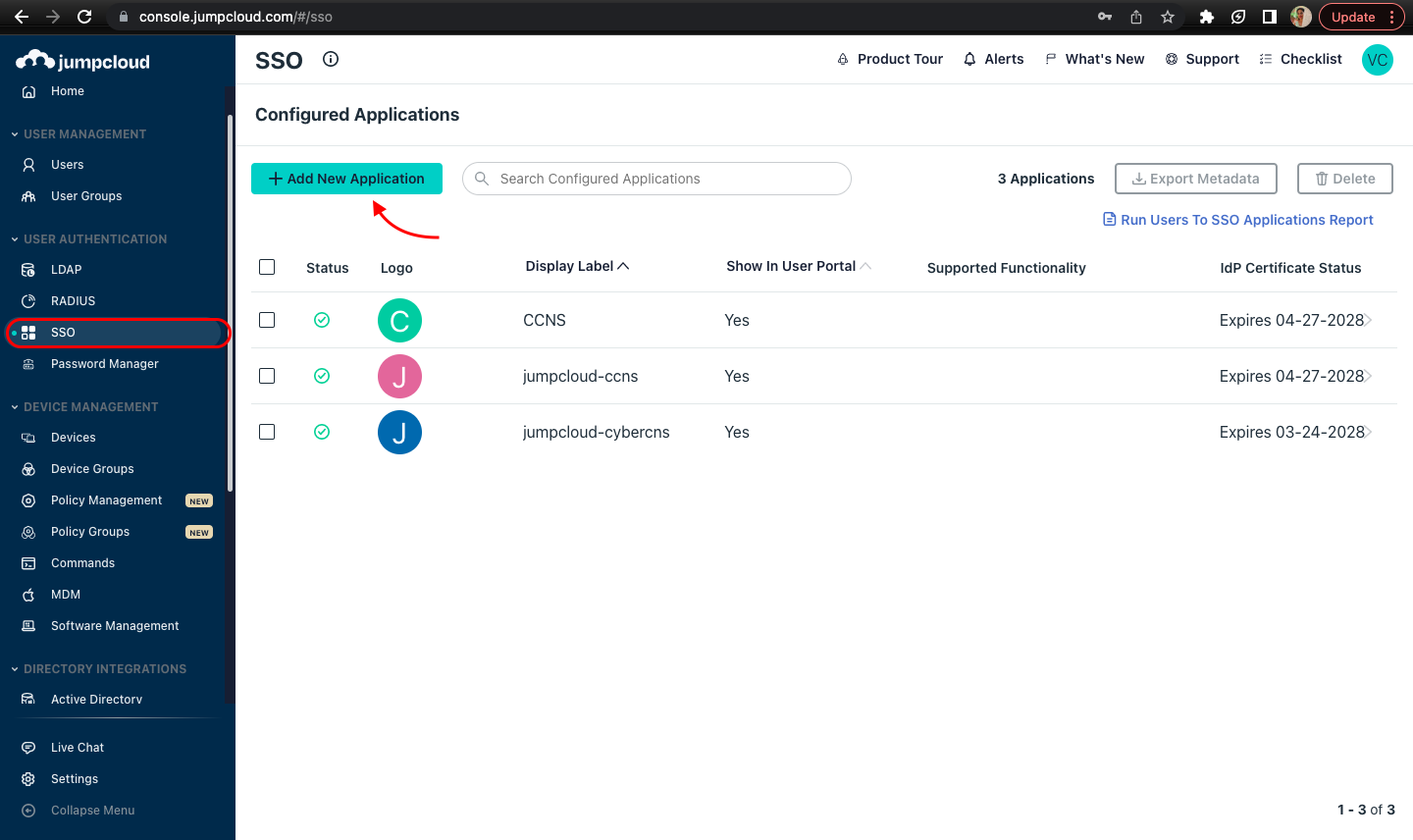
In the CyberCNS portal navigate to Global Settings > Authentication Providers and select Saml.
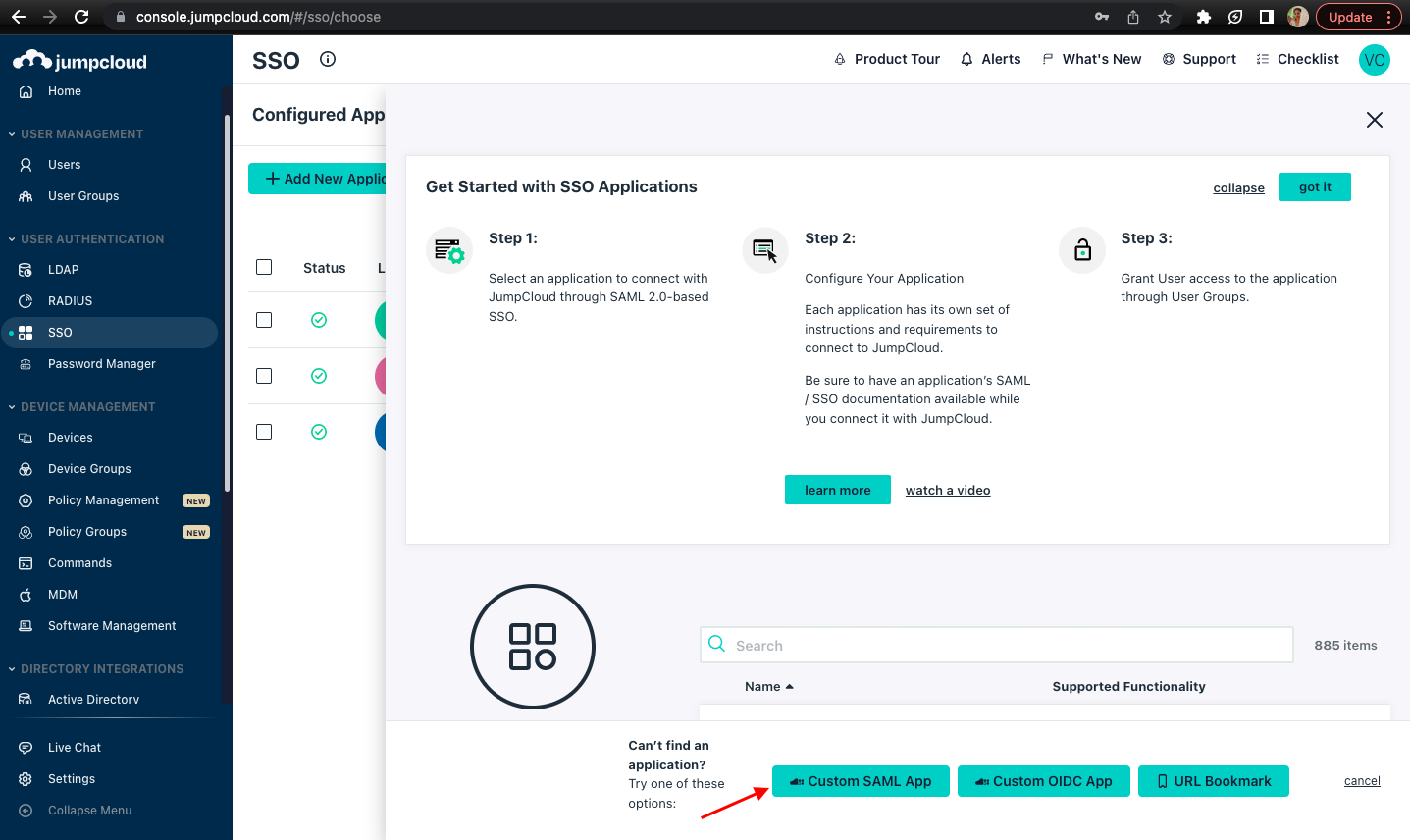
Navigate to the jumpcloud portal, and SSO section to add New Application.
In that get Started with SSO Applications section, click on Custom SAML App.
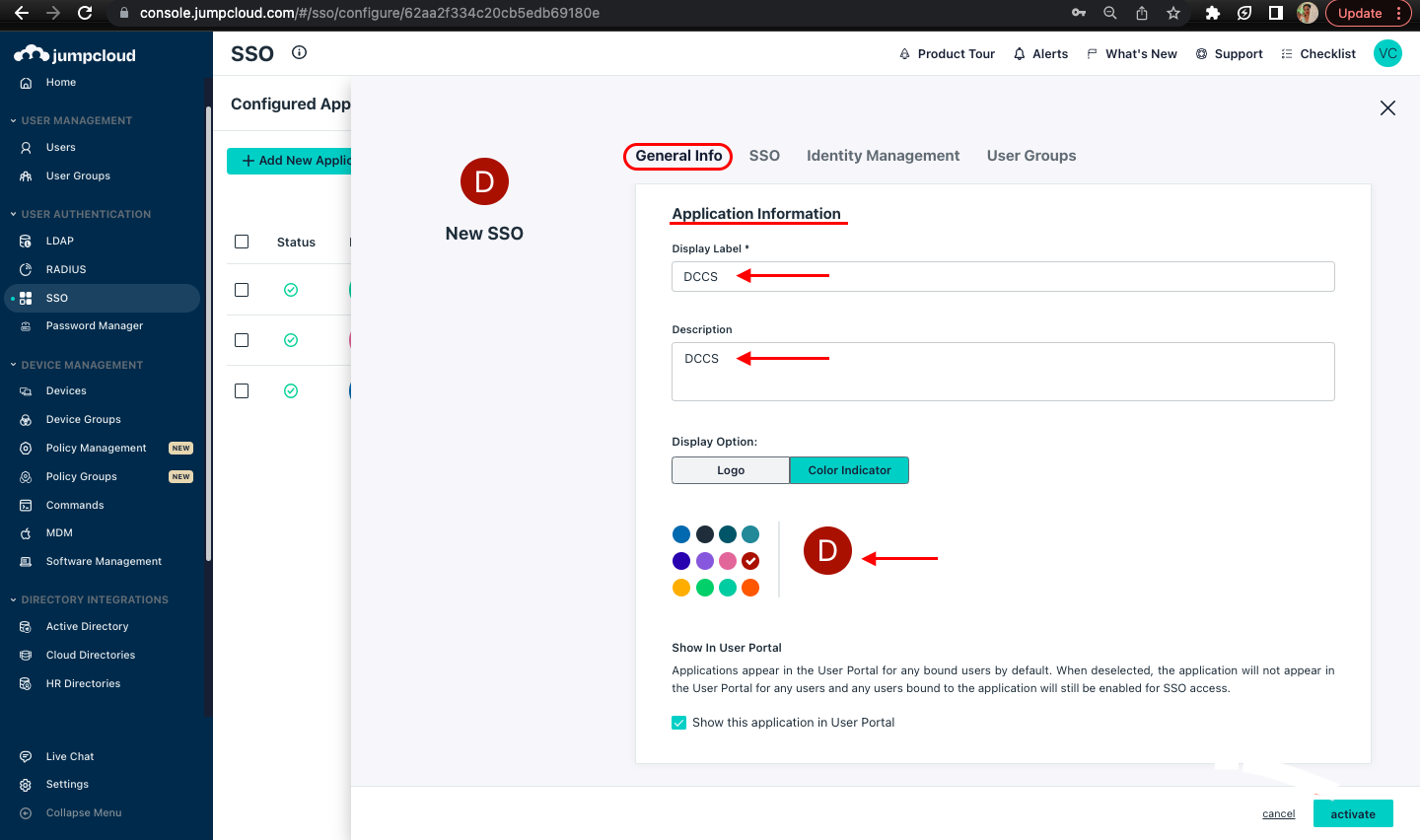
Enter the General Info details as Display Label, Description, Display Option(can choose the required color), and select the checkbox to show the application in the User portal.
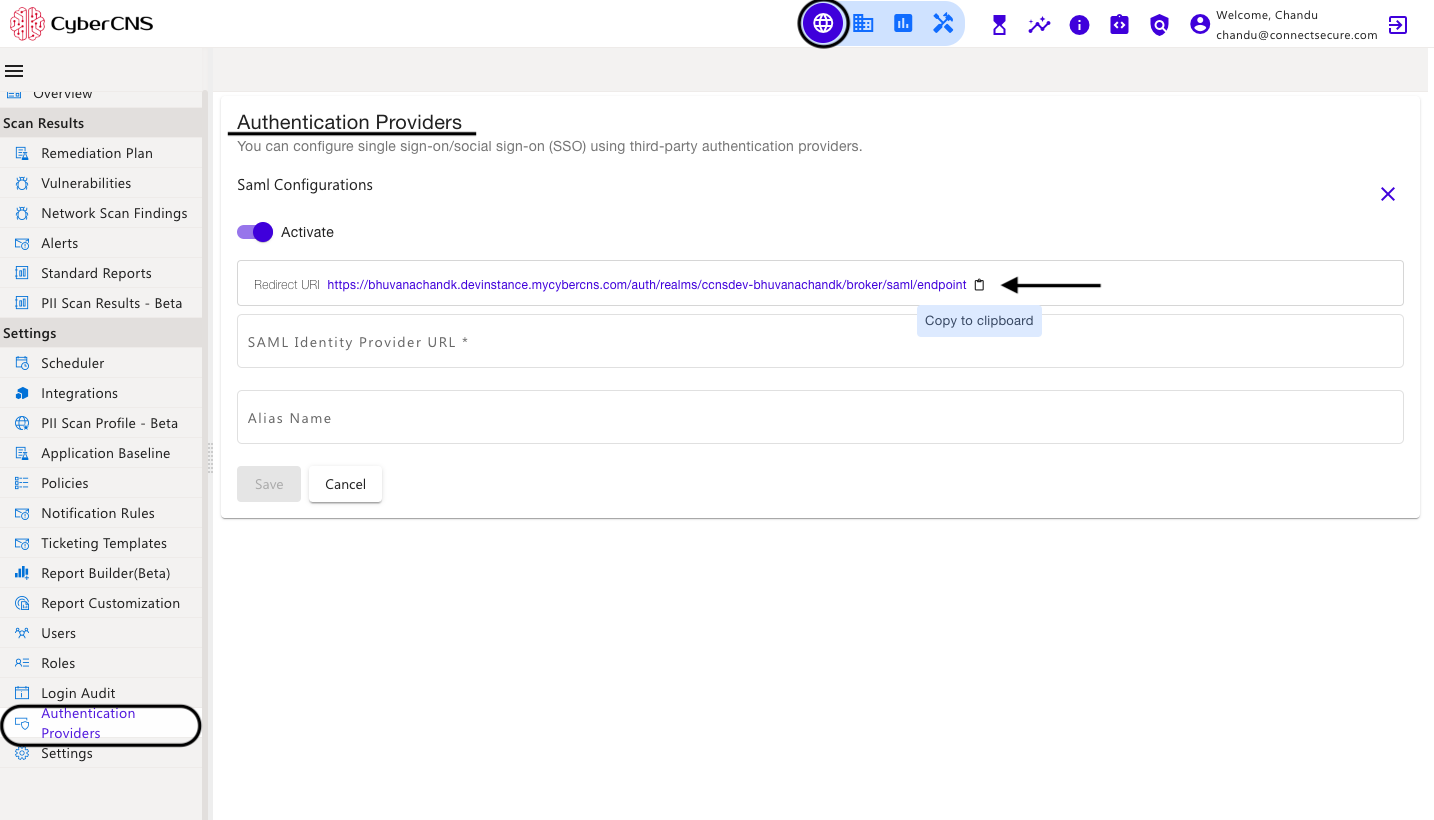
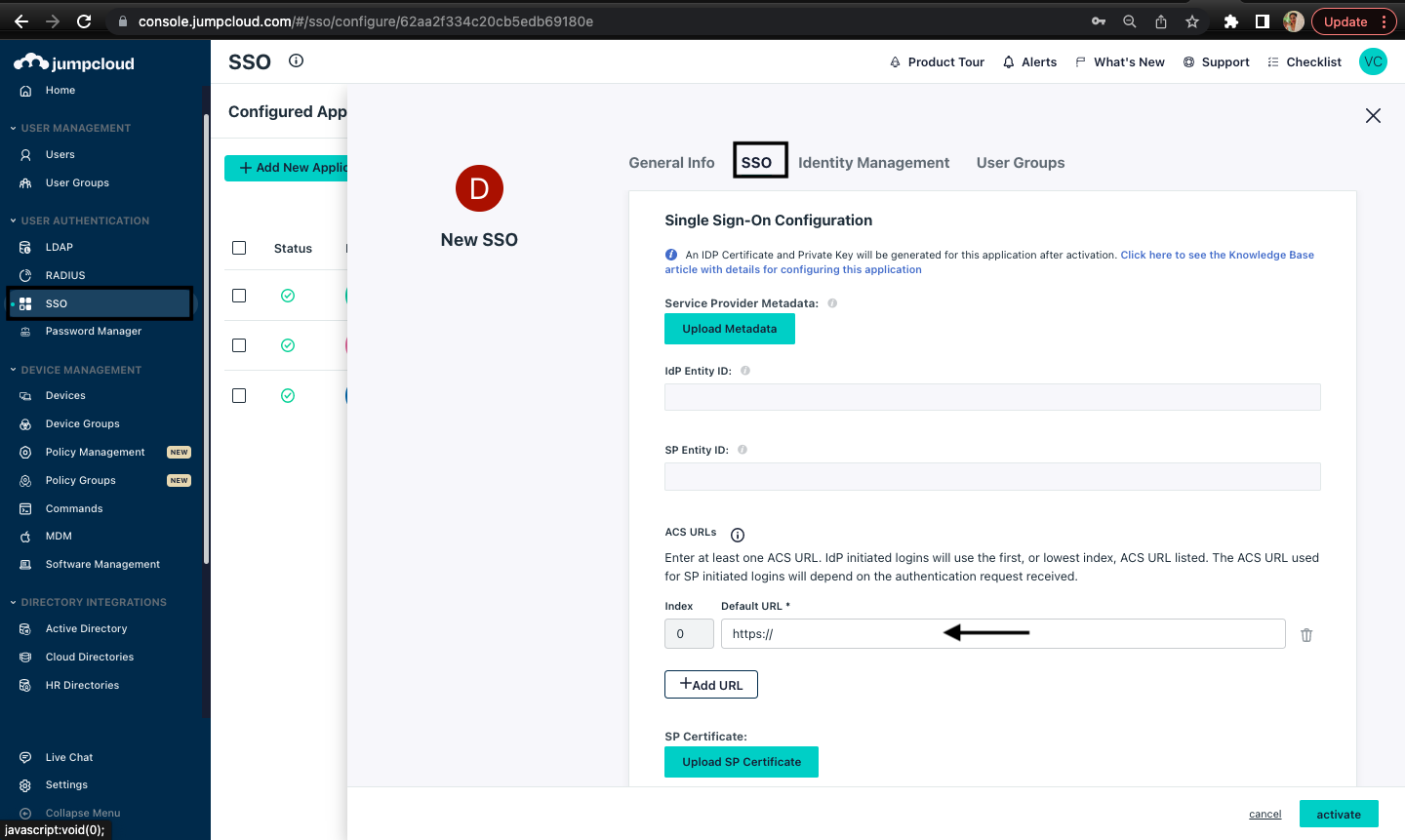
Under CyberCNS Portal, copy the URL available in the Redirect URL section under the Saml Configuration.
In the jumpcloud portal, navigate to the SSO section and paste the URL in the ACS URLs section.
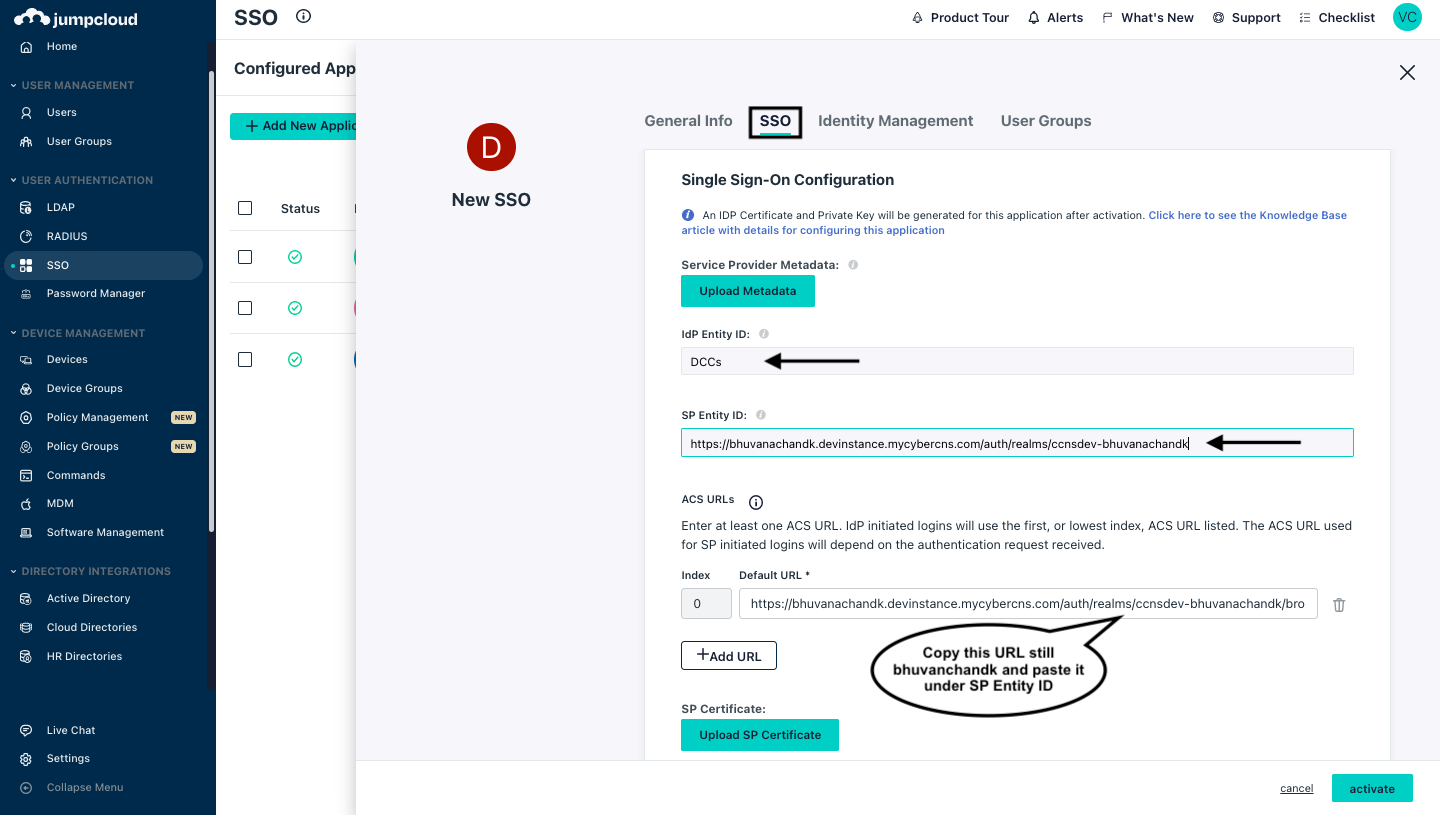
The name which is provided in the Display Label under the General Info section of Jumpcloud portal, is the same name to be given in the IDP Entity ID.
In the ACS URLs> Default URL section copy the URL only up to the part as shown below the (eg: bhuvanachandk) and paste it under the SP Entity ID.
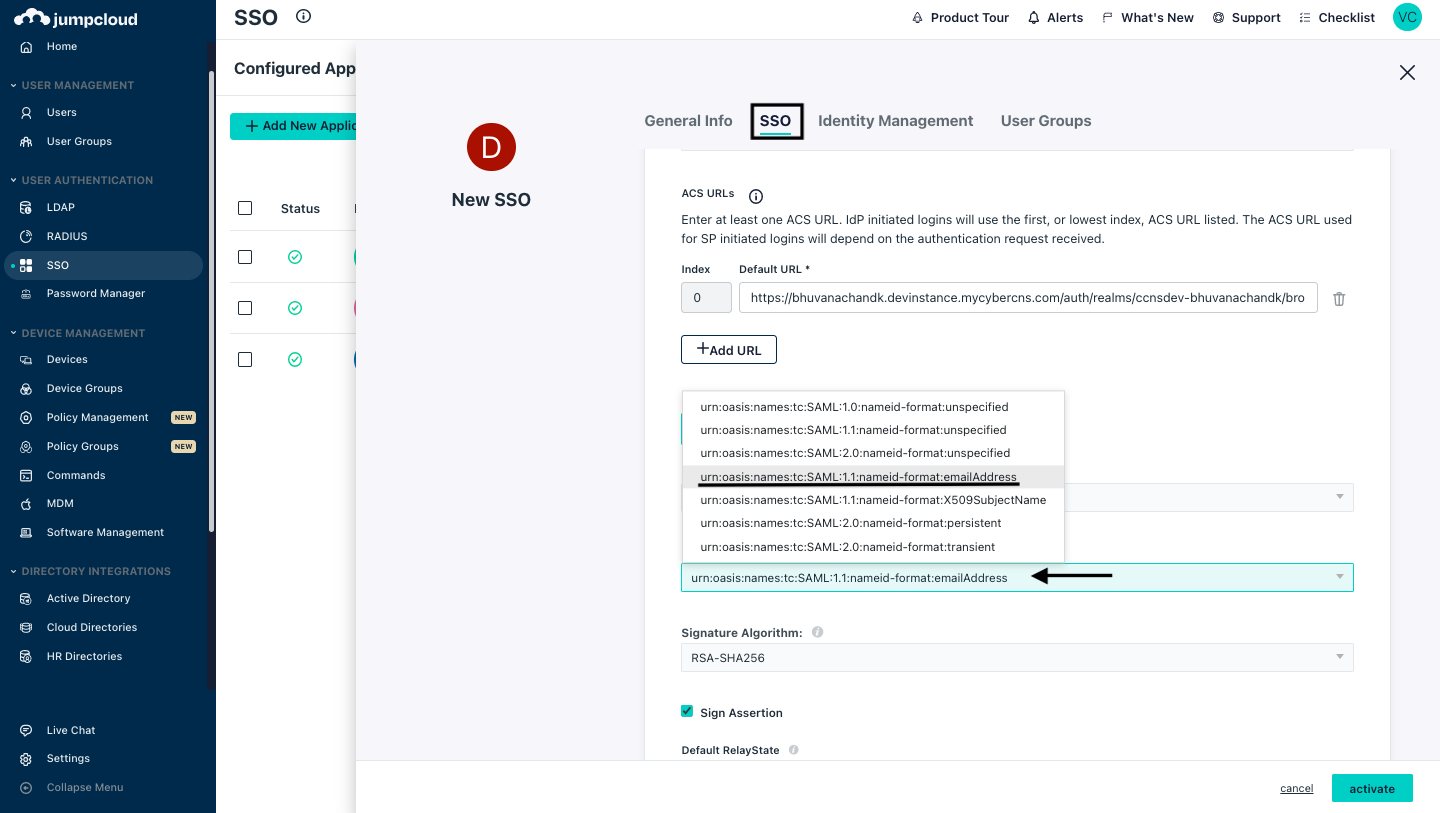
In the SAML Subject Name ID Format section, select → urn:oasis:names:tc:SAML:1.1:nameid-format:email address from the drop-down.
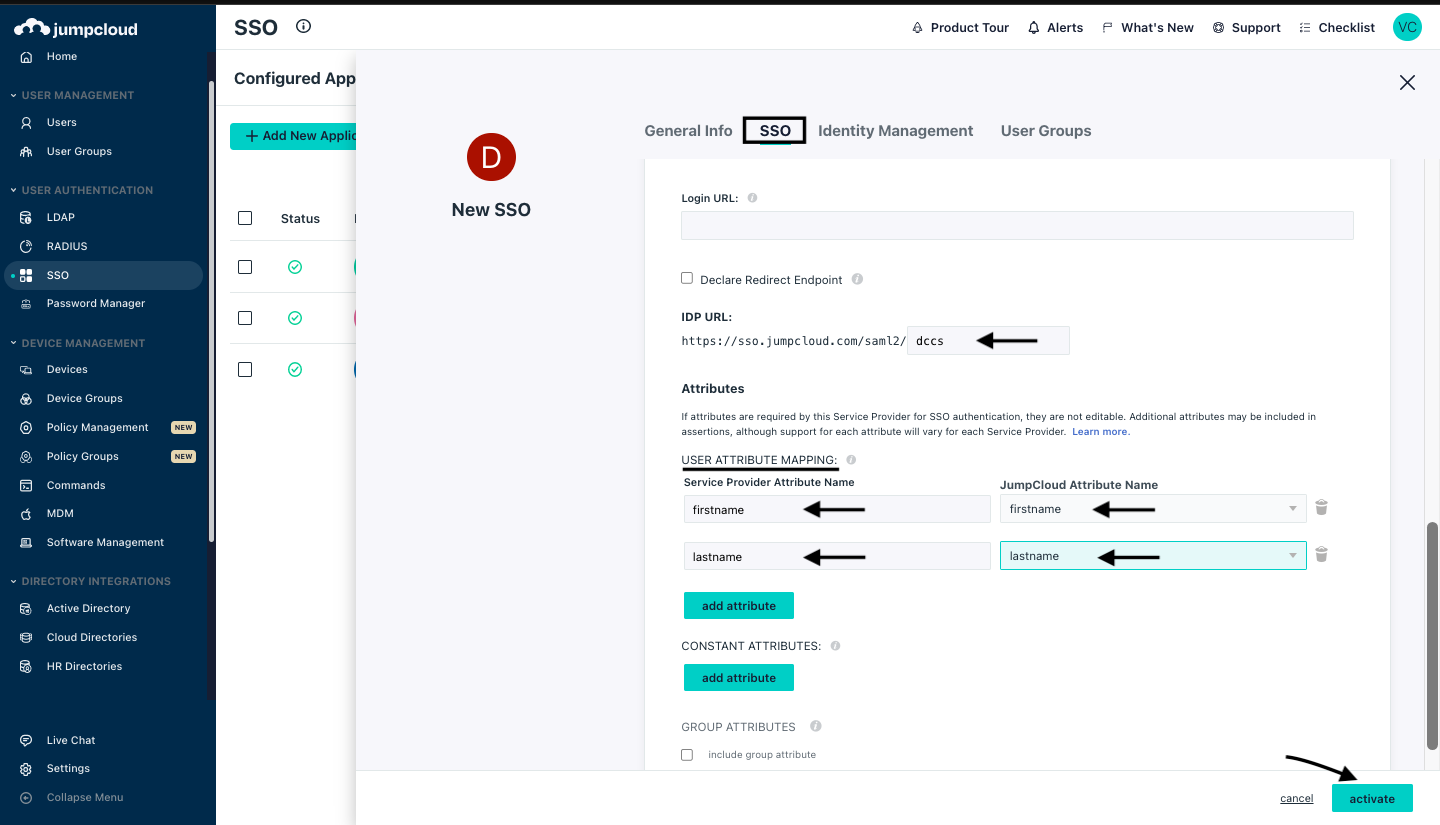
In the IDP URL section provide the name of your choice and in the Attributes section provide the service provider Attribute Name and the same name to be selected from the Jump Attribute Name using the dropdown and click on Activate.
Multiple attributes can be added by clicking on Add Attribute.
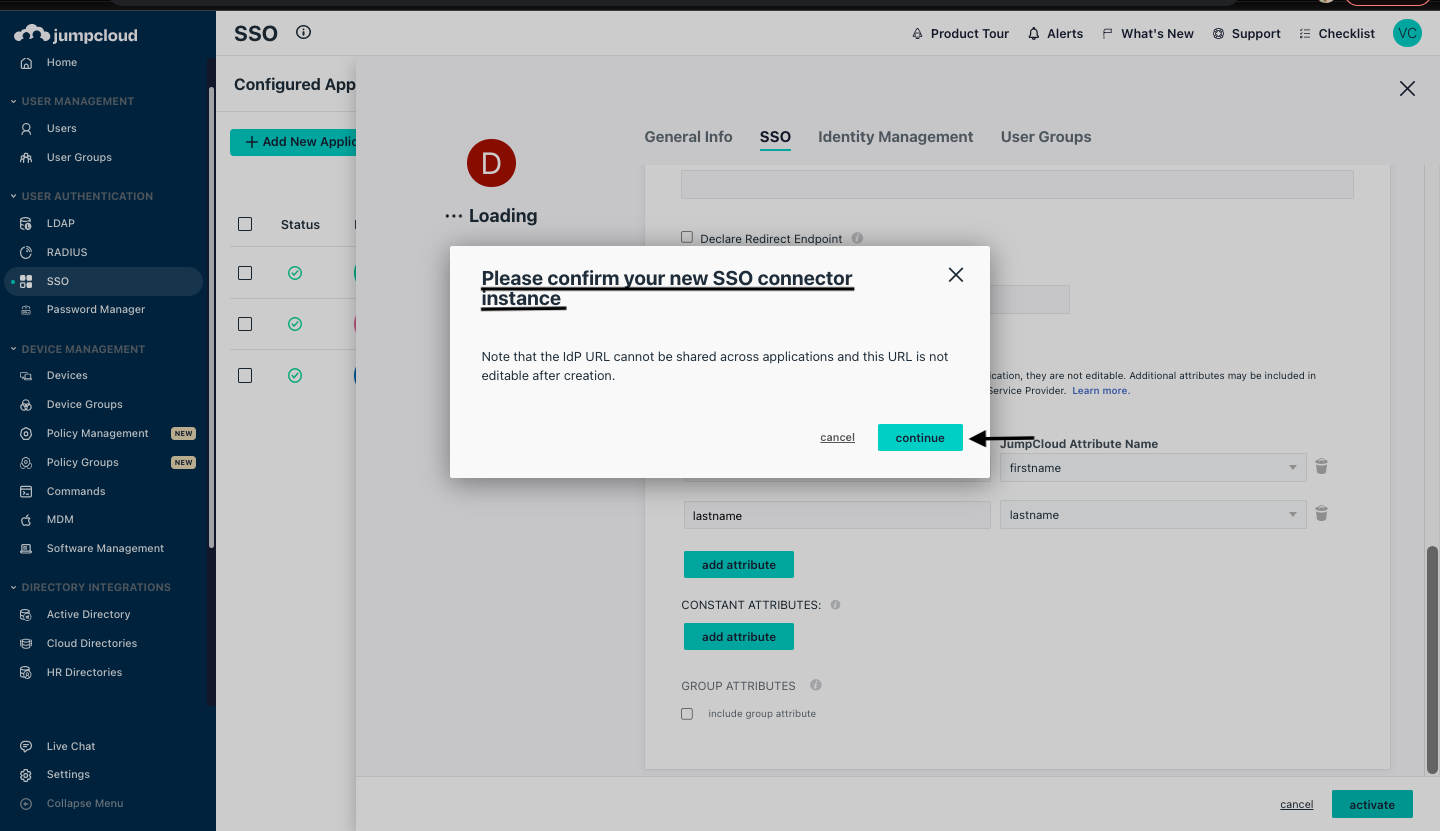
In the confirmation dialog box please confirm your new SSO connector instance and click on Continue.
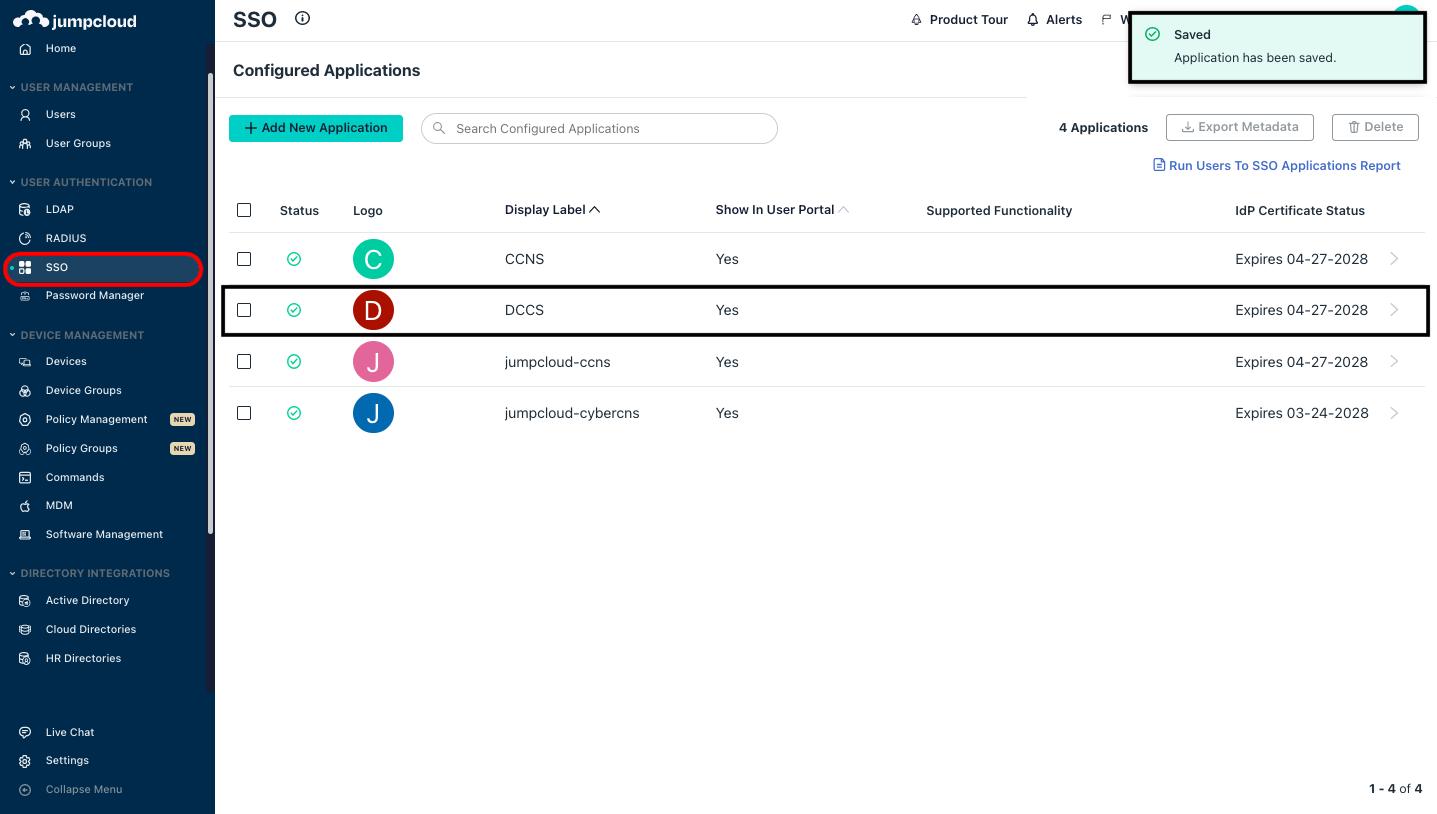
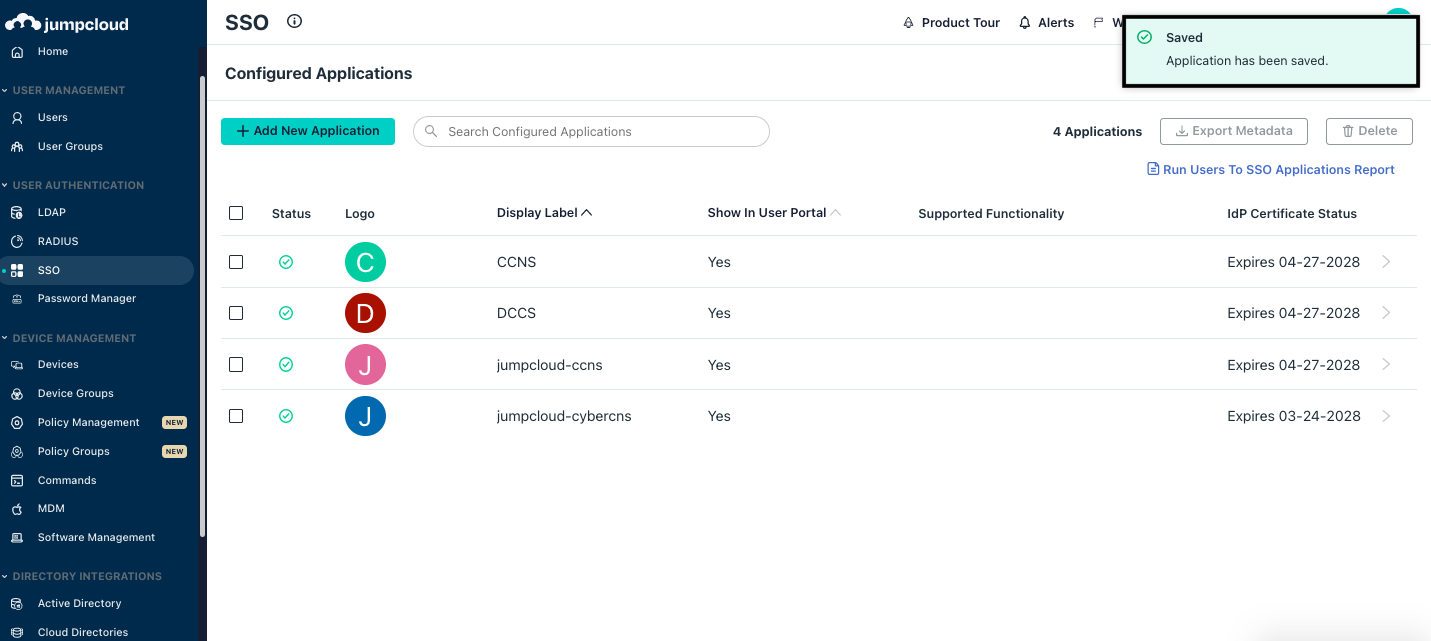
A pop-up message will be shown once the application gets Saved.
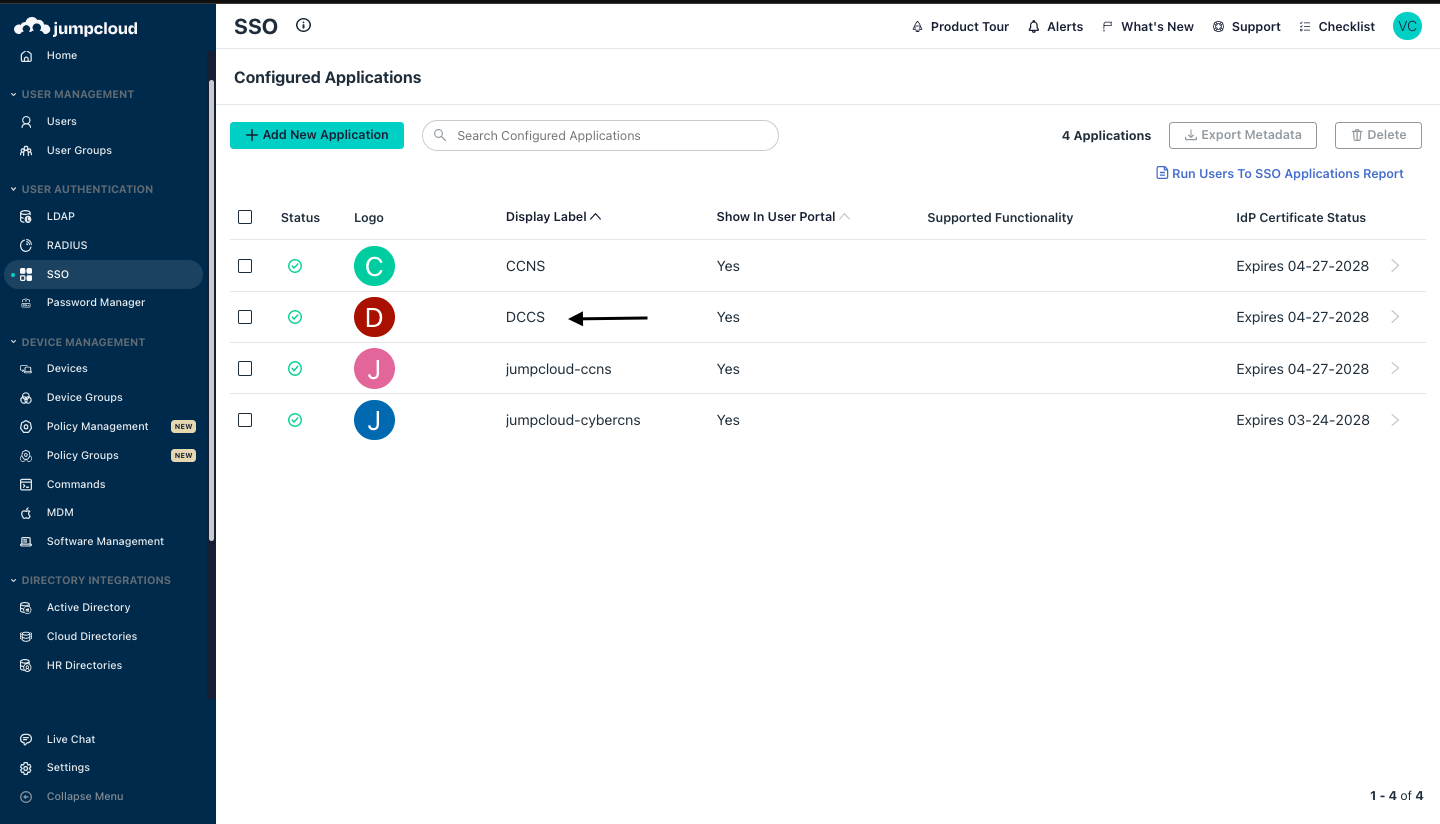
Click on the Configured Applications name.
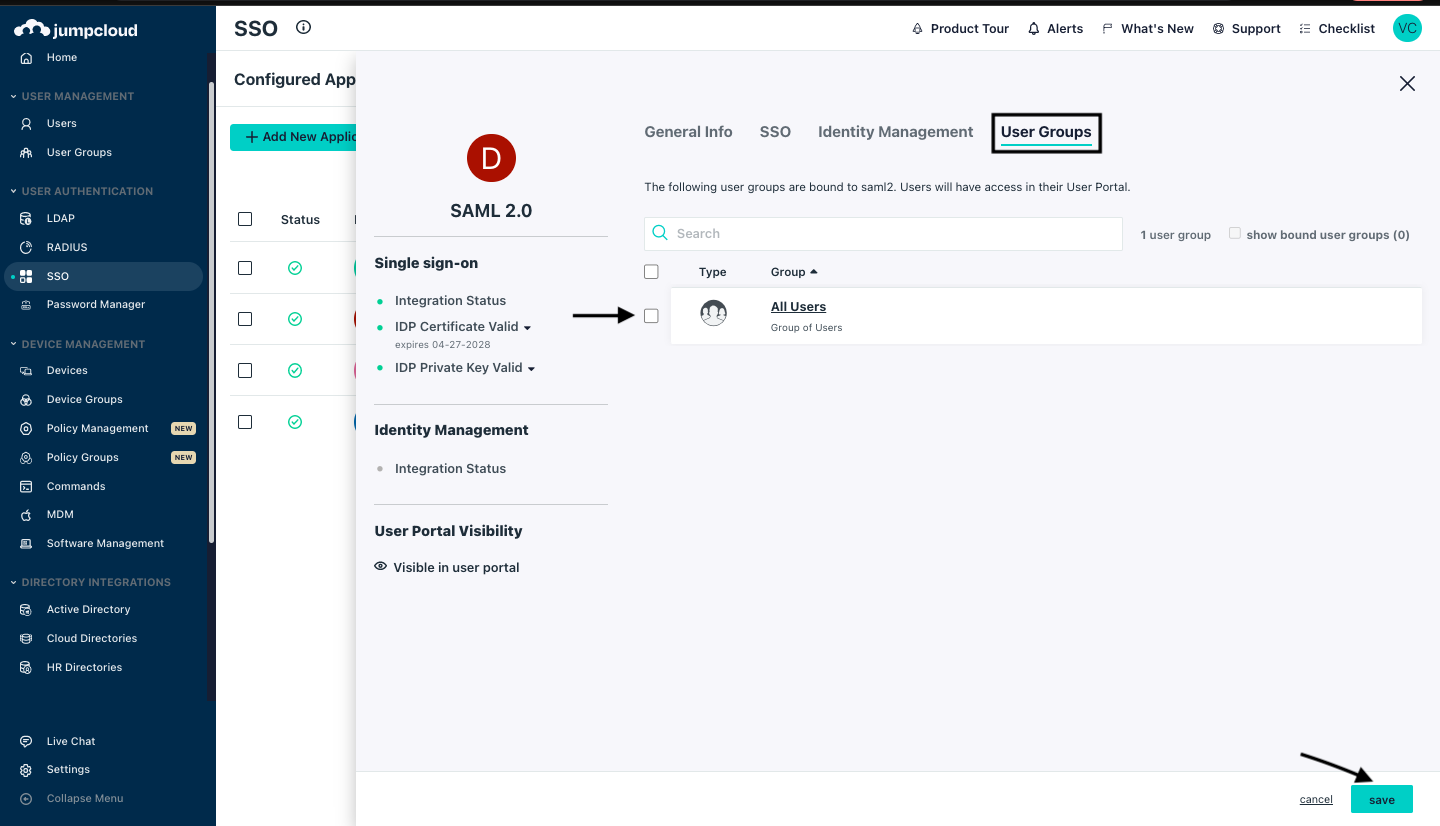
Select the checkbox of All Users under the User Groups and click on Save.
A pop-up message will be shown, once the application has been Saved.
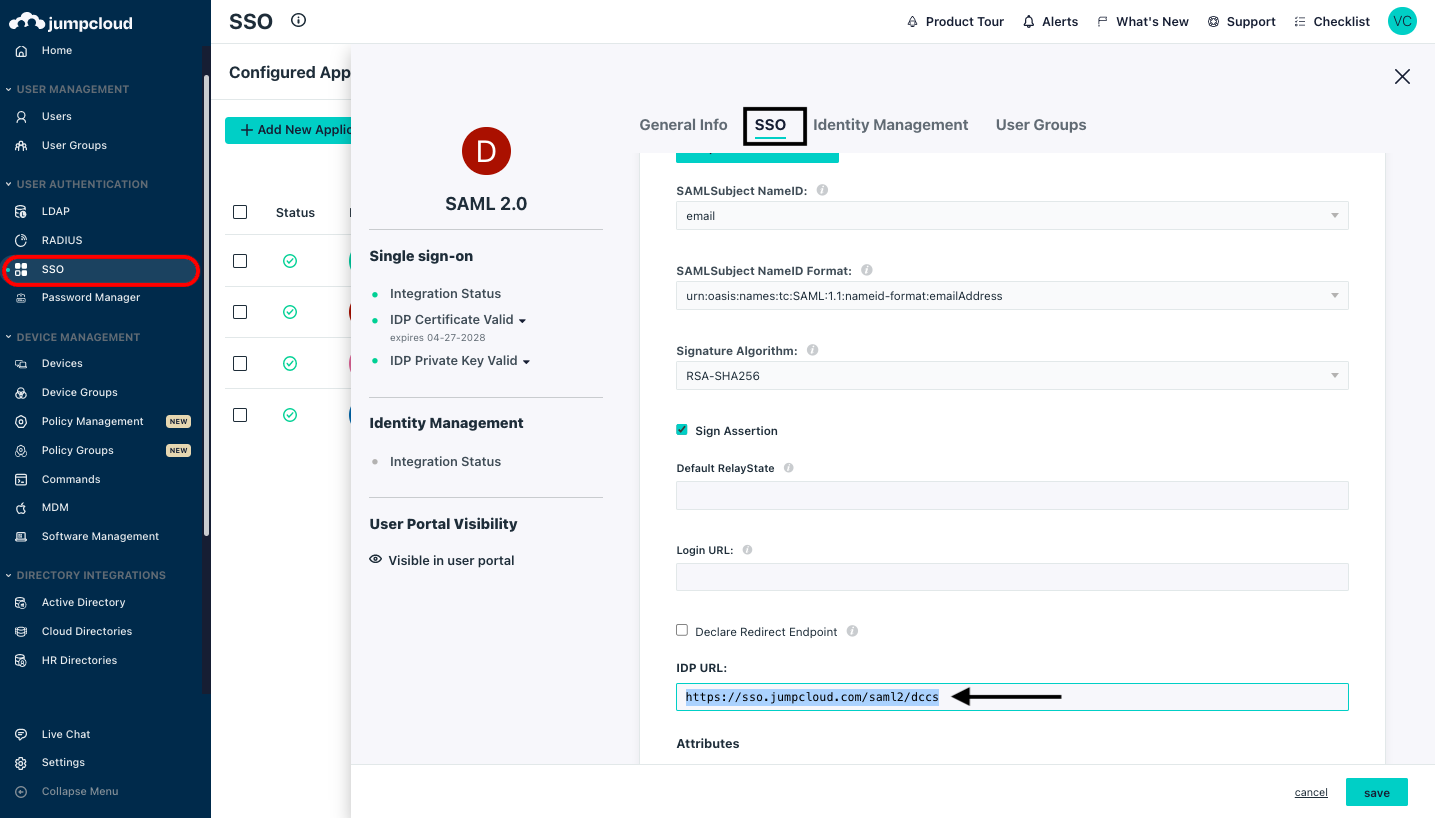
Click on the Configured Application name and in the SSO section copy the IDP URL.
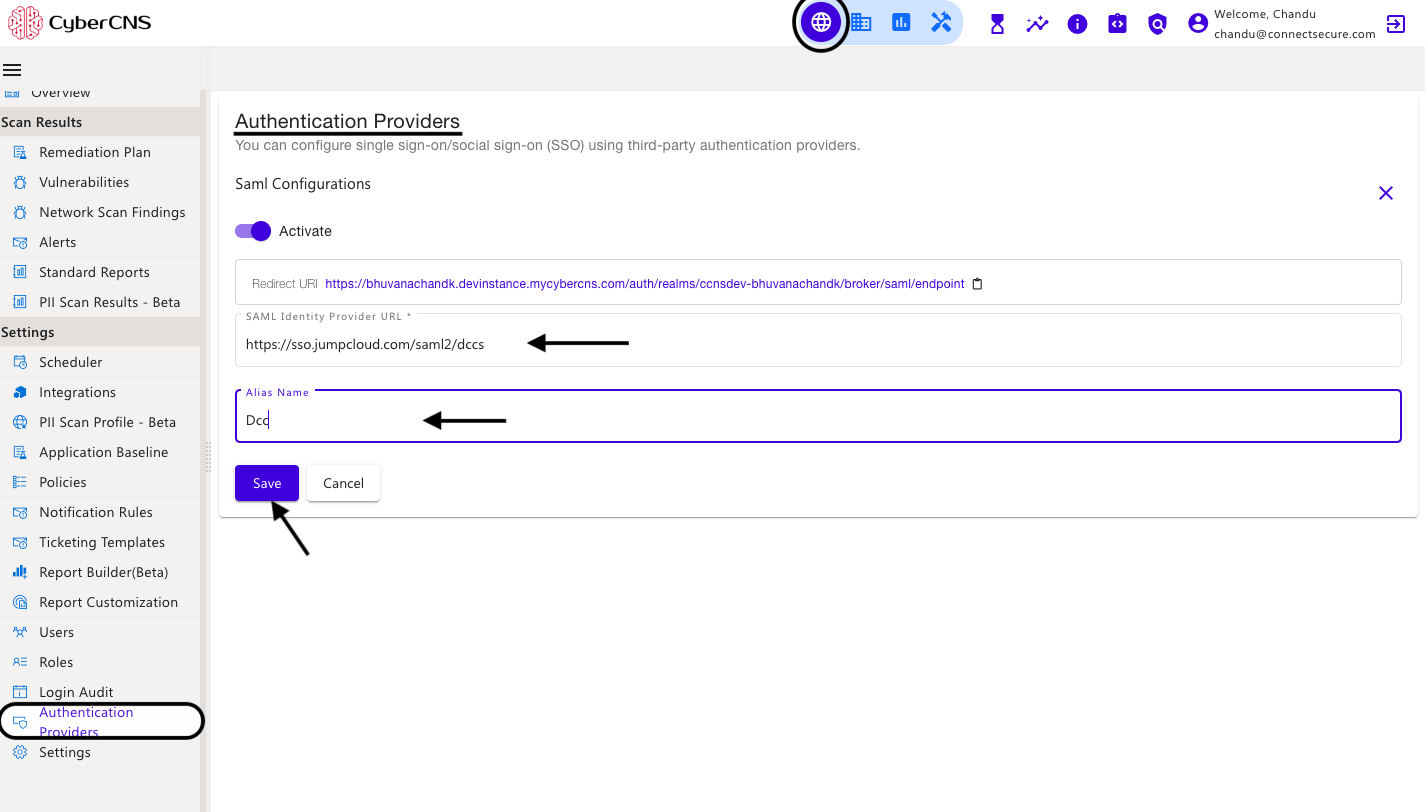
Paste the copied IDP URL, under CyberCNS Portal in the SAML Identity Provider URL section, provide the Alias Name as required, and click on Save.
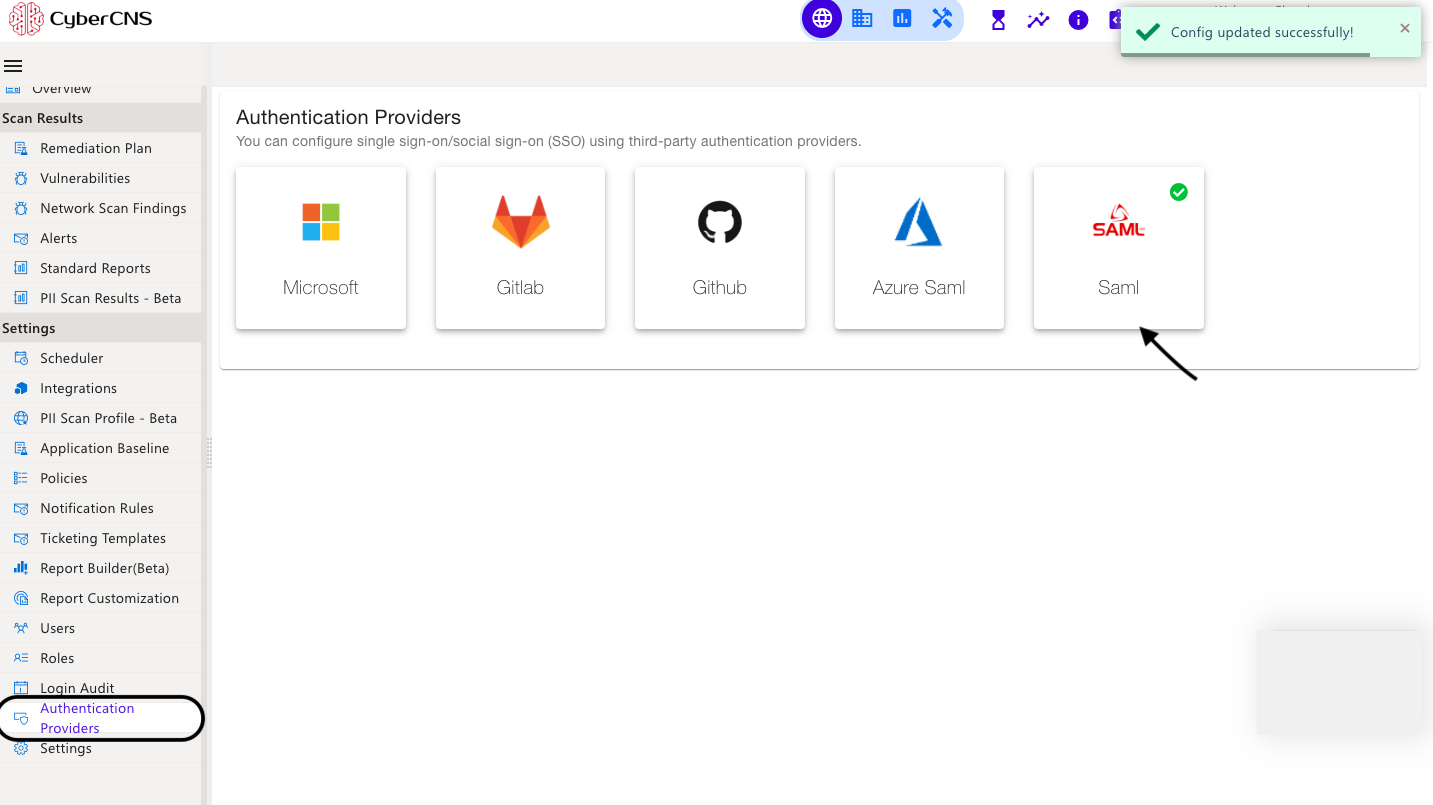
A pop-up message will be shown as Config updated successfully.
Once the configuration is completed, login into the CyberCNS portal → enter the Domain Name.
Now login with the created SAML application.
Provide the Email ID to log into your application using JumpCloud and click on Continue.
Enter the Password and click on SSO Login.
Automatically the provided Username, Email will be displayed, and enter the First name and Last Name as required, click on Submit.
Accept the Terms and Conditions, to login to the portal.
OKTA
Provide a Username to Sign in with your admin account to access Okta Dashboard on NEXT.
Provide the password and click on Verify
Once you are logged in successfully with the given credentials.
This is the Home page of OKTA and click on Admin to get into the Log-in page.
Log in to Okta and click on Applications in the Okta portal.
Click on Create App Integration to create a new application.
Select SAML 2.0 to create a new app integration. and click on the Next
Select Applications and select General settings to add the App name, App logo, Provisioning, etc.
Select Provisioning type. Here choose on-premise provisioning or SCIM as Okta is provisioned. Both deployment types are supported.
click on Save.
Navigate to Authentication Providers under the CyberCNS portal and select SAML configuration.
Add the Redirect URL as below: https://portaluseast2.mycybercns.com/auth/realms/ccnsuseast2/broker/saml/endpoint
Add Alias Name to Authentication Providers under CyberCNS portal and select SAML configuration.
Please navigate back to Okta and under Applications, continue with SAML Configurations as below:
Single sign-on URL will copied from CyberCNS Authentication Providers SAML Configurations.
click on
 to Use this for Recipient URL AND Destination URL.
to Use this for Recipient URL AND Destination URL.The Single sign-on URL, Recipient URL, and Destination URL will be the same as below:
https://portaluseast2.mycybercns.com/auth/realms/ccnsuseast2/broker/saml/endpoint
The Audience Restriction and Default Relay State will be the same as below:
https://portaluseast2.mycybercns.com/auth/realms/ccnsuseast2
Once the above URLs are added, Click on Next.
Click on Feedback ( Next Section) and select whether are you a customer or partner.
Then click on Finish this complete the configuration.
Under Applications, select Sign On and Copy the Sign On Url from more details to be copied into the CyberCNS portal under SAML Configurations as SAML Identity Provider URL.
Under Applications, click on Import to select Provisioning type. Here choose on-premise provisioning or SCIM as Okta is provisioned.
Click on Save.
SAML Settings summary will be displayed below once it's saved successfully.
Login to the Cyber CNS portal and provide a CyberCNS Domain Name.
click on given Alias Name displayed on the login page. E.g: test_okta as shown below.
This will redirect to Okta login page.
Sign In to the OKTA page by providing a Okta Username and password.
It will redirect to the CyberCNS page with successful login.
This completes the Authentication Providers setup.
Was this article helpful?
That’s Great!
Thank you for your feedback
Sorry! We couldn't be helpful
Thank you for your feedback
Feedback sent
We appreciate your effort and will try to fix the article